Example for Configuring Authentication for Telnet Login Users (RADIUS Authentication)
RADIUS Authentication Overview
When a RADIUS authentication server is deployed on a network, users can be authenticated through RADIUS. User information is created and maintained by the RADIUS authentication server. A user can successfully log in to the device only when the entered user name and password are the same as those configured on the RADIUS server. Generally, RADIUS authentication is configured on the network requiring high security, for example, financial, government, and telecommunication carrier networks.
Networking Requirements
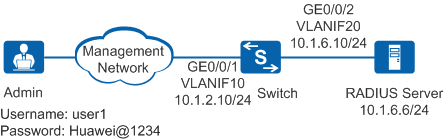
As shown in Figure 1, a RADIUS server is deployed on a network. The administrator is authenticated through RADIUS and Telnet to the device to remotely manage it. The specific requirements are as follows:
- The administrator must enter correct user name and password to log in to the device through Telnet.
- After logging in to the device through Telnet, the administrator can run the commands at levels 0-15.
Configuration Roadmap
- Enable the Telnet service.
- Set the authentication method for Telnet login users to AAA.
- Configure RADIUS authentication, including creating a RADIUS server template, an AAA authentication scheme, and a service scheme, and applying the schemes to a domain.
- Configure the domain to which the administrator belongs as the default administrative domain so that the administrator does not need to enter the domain name when logging in.

This example only provides the configurations on the device. Ensure that the required parameters have been set on the RADIUS server, for example, device's IP address, shared key, and the creating user.
Procedure
- Configure interfaces and assign IP addresses.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 10 20 [Switch] interface vlanif 10 [Switch-Vlanif10] ip address 10.1.2.10 24 [Switch-Vlanif10] quit [Switch] interface vlanif 20 [Switch-Vlanif20] ip address 10.1.6.10 24 [Switch-Vlanif20] quit [Switch] interface gigabitethernet0/0/1 [Switch-GigabitEthernet0/0/1] port link-type access [Switch-GigabitEthernet0/0/1] port default vlan 10 [Switch-GigabitEthernet0/0/1] quit [Switch] interface gigabitethernet0/0/2 [Switch-GigabitEthernet0/0/2] port link-type access [Switch-GigabitEthernet0/0/2] port default vlan 20 [Switch-GigabitEthernet0/0/2] quit
- Enable the Telnet server.
[Switch] telnet server enable - Set the authentication method for the VTY user interface to AAA.
[Switch] user-interface maximum-vty 15 //Set the maximum number of VTY login uses to 15 (The value range varies according to product versions and models). By default, the maximum number of Telnet users is 5. [Switch] user-interface vty 0 14 //Enter the VTY 0-14 user view. [Switch-ui-vty0-14] authentication-mode aaa //Set the authentication method for the VTY user view to AAA. [Switch-ui-vty0-14] protocol inbound telnet //Configure the VTY user interface to support Telnet. By default, switches in V200R006 and earlier versions support Telnet, and switches in V200R007 and later versions support SSH. [Switch-ui-vty0-14] quit
- Configure RADIUS authentication.
# Configure the RADIUS server template to implement communication between the device and the RADIUS server.
[Switch] radius-server template 1 [Switch-radius-1] radius-server authentication 10.1.6.6 1812 //Specify the IP address and port number of the RADIUS authentication server. [Switch-radius-1] radius-server shared-key cipher Hello@1234 //Specify the shared key of the RADIUS server, which must be the same as that configured on the RADIUS server. [Switch-radius-1] quit

If the RADIUS server does not accept the user names containing domain names, run the undo radius-server user-name domain-included command on the device so that the packets sent from the device to the RADIUS server do not contain domain names.
# Configure an AAA authentication scheme and set the authentication mode to RADIUS.
[Switch] aaa [Switch-aaa] authentication-scheme sch1 [Switch-aaa-authen-sch1] authentication-mode radius [Switch-aaa-authen-sch1] quit
# Configure a service scheme and set the user level to 15.
[Switch-aaa] service-scheme sch1 [Switch-aaa-service-sch1] admin-user privilege level 15 [Switch-aaa-service-sch1] quit
# Apply the AAA authentication scheme, RADIUS server template, and service scheme to the domain.
[Switch-aaa] domain huawei.com [Switch-aaa-domain-huawei.com] authentication-scheme sch1 [Switch-aaa-domain-huawei.com] radius-server 1 [Switch-aaa-domain-huawei.com] service-scheme sch1 [Switch-aaa-domain-huawei.com] quit [Switch-aaa] quit
- Configure the domain to which the administrator belongs as the default administrative domain so that the administrator does not need to enter the domain name when logging in to the device through Telnet.
[Switch] domain huawei.com admin - Verify the configuration.
# Run the test-aaa command on the device to test whether the administrator can pass the authentication.
[Switch] test-aaa user1 Huawei@1234 radius-template 1# Choose Start > Run on your computer running Windows operating system and enter cmd to open the cmd window. Run the telnet command and enter the user name user1 and password Huawei@1234 to log in to the device through Telnet.
C:\Documents and Settings\Administrator> telnet 10.1.2.10 Username:user1 Password:*********** <Switch>//The administrator successfully logs in.
Configuration Files
Configuration file of the Switch
# sysname Switch # vlan batch 10 20 # domain huawei.com admin # telnet server enable # radius-server template 1 radius-server shared-key cipher %^%#Zh-H!i<+2RUI,E4_q<''+[14Fmj4@>Aa0pM0H}@D%^%# radius-server authentication 10.1.6.6 1812 weight 80 # aaa authentication-scheme sch1 authentication-mode radius service-scheme sch1 admin-user privilege level 15 domain huawei.com authentication-scheme sch1 service-scheme sch1 radius-server 1 # interface Vlanif10 ip address 10.1.2.10 255.255.255.0 # interface Vlanif20 ip address 10.1.6.10 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type access port default vlan 10 # interface GigabitEthernet0/0/2 port link-type access port default vlan 20 # user-interface maximum-vty 15 user-interface vty 0 14 authentication-mode aaa protocol inbound telnet # return