Example for Configuring Intra-AS Three-Segment VXLAN for Layer 3 Interconnection
Networking Requirements
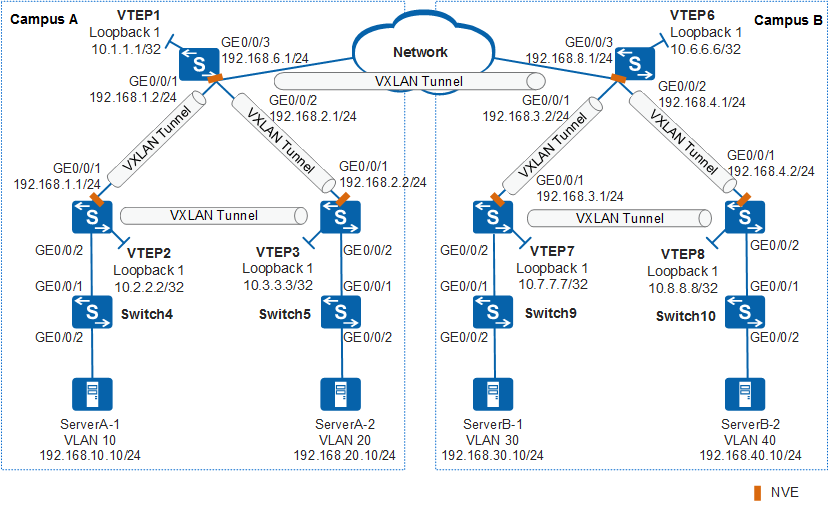
In Figure 1, campus A and campus B are planned in the same BGP AS domain (for example, BGP AS 100). BGP EVPN is configured on the campus network to create a VXLAN tunnel for the distributed gateways, implementing interconnection between ServerA-1 and ServerA-2 and between ServerB-1 and ServerB-2. BGP EVPN is configured between VTEP3 and VTEP7 to create a VXLAN tunnel for communication between campus A and campus B (for example, between ServerA-1 and ServerB-2).

This example uses the S6730-S, S6730S-S, S5732-H, S5731-S, S5731S-S, S5731S-H, S6730-H, S6730S-H, S5731-H, S5720-HI, S5730-HI, or S6720-HI as an example to describe the configuration.
Data Preparation
Device |
EVPN Instance |
RD Value |
BD |
VNI |
Router id |
Peer IP |
|---|---|---|---|---|---|---|
VTEP1 |
- |
- |
- |
- |
10.1.1.1 |
10.2.2.2 10.3.3.3 10.6.6.6 |
VTEP2 |
evpn10:
|
2:10 |
10 |
10 |
10.2.2.2 |
10.1.1.1 |
VTEP3 |
evpn20:
|
3:20 |
20 |
20 |
10.3.3.3 |
10.1.1.1 |
VTEP6 |
- |
- |
- |
- |
10.6.6.6 |
10.1.1.1 10.7.7.7 10.8.8.8 |
VTEP7 |
evpn30:
|
7:30 |
30 |
30 |
10.7.7.7 |
10.6.6.6 |
VTEP8 |
evpn40:
|
8:40 |
40 |
40 |
10.8.8.8 |
10.6.6.6 |
Device |
Interface |
VPN Instance |
VNI |
RD Value |
|---|---|---|---|---|
VTEP1 |
- |
vpn1:
|
100 |
1:100 |
VTEP2 |
VBDIF10:
|
vpn1:
|
100 |
2:100 |
VTEP3 |
VBDIF20:
|
vpn1:
|
100 |
3:100 |
VTEP6 |
- |
vpn1:
|
100 |
6:100 |
VTEP7 |
VBDIF30:
|
vpn1:
|
100 |
7:100 |
VTEP8 |
VBDIF40:
|
vpn1:
|
100 |
8:100 |

When configuring the RT (EVPN) attribute of a VPN instance, note that only devices (such as VTEP1 and VTEP6 in this example) used for inter-campus communication and devices within a campus support EVPN route cross with each other, and devices in different campuses do not support EVPN route cross with each other. The device used for inter-campus communication supports EVPN route cross with devices in the same campus and the device used for inter-campus communication in the other campus.
In this example, VTEP2 and VTEP3 in campus A support EVPN route cross with each other and with VTEP1 respectively. VTEP2 and VTEP3 do not support EVPN route cross with devices in campus B. VTEP1 in campus A and VTEP6 in campus B support EVPN route cross with each other.
Configuration Roadmap
The configuration roadmap is as follows:
Configuring a VXLAN tunnel within campus A and campus B to implement internal communication
- Configure a routing protocol on VTEP1, VTEP2, VTEP3, VTEP6, VTEP7, and VTEP8 to ensure network connectivity at Layer 3.
- Configure a deployment mode for the VXLAN access service on VTEP2, VTEP3, VTEP7, and VTEP8, and configure a VLAN on Switch4, Switch5, Switch9, and Switch10.
- Configure an EVPN instance on VTEP2, VTEP3, VTEP7, and VTEP8, and bind the instance to a BD.
- Configure a VPN instance on VTEP1, VTEP2, VTEP3, VTEP6, VTEP7, and VTEP8, and bind the VPN instance to a VBDIF interface on VTEP2, VTEP3, VTEP7, and VTEP8.
- Establish BGP EVPN peer relationships between VTEP1 and VTEP2, between VTEP1 and VTEP3, between VTEP6 and VTEP7, and between VTEP6 and VTEP8 to implement EVPN route receiving and advertisement between the VTEPs.
- Configure VTEP1 as a reflector and specify VTEP2 and VTEP3 as clients. Configure VTEP6 as a reflector and specify VTEP7 and VTEP8 as clients. In this way, BGP EVPN peer relationships can be established between VTEP2 and VTEP3 and between VTEP7 and VTEP8, and they can receive and advertise EVPN routes with each other.
- Configure the destination IP address of the VXLAN tunnel on VTEP2, VTEP3, VTEP7, and VTEP8.
- Configure a distributed VXLAN gateway on VTEP2, VTEP3, VTEP7, and VTEP8.
- Configure a default route on VTEP1 and VTEP6 respectively, and import BGP routes. VTEP1 is responsible for communication between users in campus A and those outside campus A, and VTEP6 is responsible for communication between users in campus B and those outside campus B.

Layer 3 interconnection of the campus network is the basis of the virtual network. If Layer 3 interconnection has been implemented on the live campus network, step 1 in this example can be omitted.
Configuring a VXLAN tunnel between campus A and campus B to implement interconnection between campuses
- Establish a BGP EVPN peer relationship between VTEP1 and VTEP6 to implement EVPN route receiving and advertisement between them.
- Configure EVPN route regeneration on VTEP1 and VTEP6 so that VTEP1 and VTEP6 can re-generate received IP prefix routes. Devices in the two campuses communicate through the VXLAN tunnel between VTEP1 and VTEP6.
Procedure
- Configure a routing protocol.
# Configure IP addresses for the interfaces on VTEP2. The configurations of VTEP1, VTEP3, VTEP6, VTEP7, and VTEP8 are similar to those of VTEP2, and are not mentioned here. When OSPF is used, the 32-bit loopback interface addresses of devices must be advertised.
<HUAWEI> system-view [HUAWEI] sysname VTEP2 [VTEP2] interface loopback 1 [VTEP2-LoopBack1] ip address 10.2.2.2 32 [VTEP2-LoopBack1] quit [VTEP2] interface gigabitethernet 0/0/1 [VTEP2-GigabitEthernet0/0/1] undo portswitch [VTEP2-GigabitEthernet0/0/1] ip address 192.168.1.1 24 [VTEP2-GigabitEthernet0/0/1] quit [VTEP2] ospf router-id 10.2.2.2 [VTEP2-ospf-1] area 0 [VTEP2-ospf-1-area-0.0.0.0] network 10.2.2.2 0.0.0.0 [VTEP2-ospf-1-area-0.0.0.0] network 192.168.1.0 0.0.0.255 [VTEP2-ospf-1-area-0.0.0.0] quit [VTEP2-ospf-1] quit
# After OSPF is configured, VTEP1, VTEP2, VTEP3, VTEP6, VTEP7, and VTEP8 can learn the loopback interface address of each other and successfully ping each other. The following shows the result when VTEP2 pings VTEP3.
[VTEP2] ping 10.3.3.3 PING 10.3.3.3: 56 data bytes, press CTRL_C to break Reply from 10.3.3.3: bytes=56 Sequence=1 ttl=255 time=240 ms Reply from 10.3.3.3: bytes=56 Sequence=2 ttl=255 time=5 ms Reply from 10.3.3.3: bytes=56 Sequence=3 ttl=255 time=5 ms Reply from 10.3.3.3: bytes=56 Sequence=4 ttl=255 time=14 ms Reply from 10.3.3.3: bytes=56 Sequence=5 ttl=255 time=5 ms --- 10.3.3.3 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 5/53/240 ms - Configure VLAN access on Switch4 and Switch5 in campus A, and configure VXLAN service access points on VTEP2 and VTEP3. Configure VLAN access on Switch9 and Switch10 in campus B, and configure VXLAN service access points on VTEP7 and VTEP8.
# Configure Switch4. The configurations of Switch9 are similar to those of Switch4.
<HUAWEI> system-view [HUAWEI] sysname Switch4 [Switch4] vlan batch 10 [Switch4] interface gigabitethernet 0/0/2 [Switch4-GigabitEthernet0/0/2] port link-type access [Switch4-GigabitEthernet0/0/2] port default vlan 10 [Switch4-GigabitEthernet0/0/2] quit [Switch4] interface gigabitethernet 0/0/1 [Switch4-GigabitEthernet0/0/1] port link-type trunk [Switch4-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [Switch4-GigabitEthernet0/0/1] quit
# Configure Switch5. The configurations of Switch10 are similar to those of Switch5.
<HUAWEI> system-view [HUAWEI] sysname Switch5 [Switch5] vlan batch 20 [Switch5] interface gigabitethernet 0/0/2 [Switch5-GigabitEthernet0/0/2] port link-type access [Switch5-GigabitEthernet0/0/2] port default vlan 20 [Switch5-GigabitEthernet0/0/2] quit [Switch5] interface gigabitethernet 0/0/1 [Switch5-GigabitEthernet0/0/1] port link-type trunk [Switch5-GigabitEthernet0/0/1] port trunk allow-pass vlan 20 [Switch5-GigabitEthernet0/0/1] quit
# Configure VTEP2. The configurations of VTEP7 are similar to those of VTEP2.
[VTEP2] bridge-domain 10 [VTEP2-bd10] quit [VTEP2] vcmp role silent [VTEP2] interface gigabitethernet 0/0/2 [VTEP2-GigabitEthernet0/0/2] port link-type trunk [VTEP2-GigabitEthernet0/0/2] quit [VTEP2] interface gigabitethernet 0/0/2.1 mode l2 [VTEP2-GigabitEthernet0/0/2.1] encapsulation dot1q vid 10 [VTEP2-GigabitEthernet0/0/2.1] bridge-domain 10 [VTEP2-GigabitEthernet0/0/2.1] quit
# Configure VTEP3. The configurations of VTEP8 are similar to those of VTEP3.
[VTEP3] bridge-domain 20 [VTEP3-bd20] quit [VTEP3] vcmp role silent [VTEP3] interface gigabitethernet 0/0/2 [VTEP3-GigabitEthernet0/0/2] port link-type trunk [VTEP3-GigabitEthernet0/0/2] quit [VTEP3] interface gigabitethernet 0/0/2.1 mode l2 [VTEP3-GigabitEthernet0/0/2.1] encapsulation dot1q vid 20 [VTEP3-GigabitEthernet0/0/2.1] bridge-domain 20 [VTEP3-GigabitEthernet0/0/2.1] quit
- Configure an EVPN instance on VTEP2 and VTEP3 in campus A and bind the instance to a BD. Configure an EVPN instance on VTEP7 and VTEP8 in campus B and bind the instance to a BD.
# Configure VTEP2. The configurations of VTEP7 are similar to those of VTEP2.
[VTEP2] evpn vpn-instance evpn10 bd-mode [VTEP2-evpn-instance-evpn10] route-distinguisher 2:10 [VTEP2-evpn-instance-evpn10] vpn-target 10:1 both [VTEP2-evpn-instance-evpn10] vpn-target 1:100 export-extcommunity [VTEP2-evpn-instance-evpn10] quit [VTEP2] bridge-domain 10 [VTEP2-bd10] vxlan vni 10 [VTEP2-bd10] evpn binding vpn-instance evpn10 [VTEP2-bd10] quit
# Configure VTEP3. The configurations of VTEP8 are similar to those of VTEP3.
[VTEP3] evpn vpn-instance evpn20 bd-mode [VTEP3-evpn-instance-evpn20] route-distinguisher 3:20 [VTEP3-evpn-instance-evpn20] vpn-target 20:1 both [VTEP3-evpn-instance-evpn20] vpn-target 1:100 export-extcommunity [VTEP3-evpn-instance-evpn20] quit [VTEP3] bridge-domain 20 [VTEP3-bd20] vxlan vni 20 [VTEP3-bd20] evpn binding vpn-instance evpn20 [VTEP3-bd20] quit
- Configure a VPN instance on VTEP1 in campus A and VTEP6 in campus B, configure VPN instances on VTEP2 and VTEP3 in campus A and VTEP7 and VTEP8 in campus B, and bind the VPN instances on VTEP2, VTEP3, VTEP7, and VTEP8 to VBDIF interfaces.
# Configure VTEP1. The configurations of VTEP6 are similar to those of VTEP1.
[VTEP1] ip vpn-instance vpn1 [VTEP1-vpn-instance-vpn1] ipv4-family [VTEP1-vpn-instance-vpn1-af-ipv4] route-distinguisher 1:100 [VTEP1-vpn-instance-vpn1-af-ipv4] vpn-target 1:100 both evpn [VTEP1-vpn-instance-vpn1-af-ipv4] vpn-target 10:100 both evpn [VTEP1-vpn-instance-vpn1-af-ipv4] quit [VTEP1-vpn-instance-vpn1] vxlan vni 100 [VTEP1-vpn-instance-vpn1] quit
# Configure VTEP2. The configurations of VTEP7 are similar to those of VTEP2.
[VTEP2] ip vpn-instance vpn1 [VTEP2-vpn-instance-vpn1] ipv4-family [VTEP2-vpn-instance-vpn1-af-ipv4] route-distinguisher 2:100 [VTEP2-vpn-instance-vpn1-af-ipv4] vpn-target 1:100 both evpn [VTEP2-vpn-instance-vpn1-af-ipv4] quit [VTEP2-vpn-instance-vpn1] vxlan vni 100 [VTEP2-vpn-instance-vpn1] quit [VTEP2] interface vbdif 10 [VTEP2-Vbdif10] ip binding vpn-instance vpn1 [VTEP2-Vbdif10] quit
# Configure VTEP3. The configurations of VTEP8 are similar to those of VTEP3.
[VTEP3] ip vpn-instance vpn1 [VTEP3-vpn-instance-vpn1] ipv4-family [VTEP3-vpn-instance-vpn1-af-ipv4] route-distinguisher 3:100 [VTEP3-vpn-instance-vpn1-af-ipv4] vpn-target 1:100 both evpn [VTEP3-vpn-instance-vpn1-af-ipv4] quit [VTEP3-vpn-instance-vpn1] vxlan vni 100 [VTEP3-vpn-instance-vpn1] quit [VTEP3] interface vbdif 20 [VTEP3-Vbdif20] ip binding vpn-instance vpn1 [VTEP3-Vbdif20] quit
- Establish BGP EVPN peer relationships between VTEP1 and VTEP2 and between VTEP1 and VTEP3 in campus A. Establish BGP EVPN peer relationships between VTEP6 and VTEP7 and between VTEP6 and VTEP8 in campus B.
# Configure VTEP1. The configurations of VTEP6 are similar to those of VTEP1.
[VTEP1] bgp 100 [VTEP1-bgp] router-id 10.1.1.1 [VTEP1-bgp] peer 10.2.2.2 as-number 100 [VTEP1-bgp] peer 10.2.2.2 connect-interface LoopBack1 [VTEP1-bgp] peer 10.3.3.3 as-number 100 [VTEP1-bgp] peer 10.3.3.3 connect-interface LoopBack1 [VTEP1-bgp] l2vpn-family evpn [VTEP1-bgp-af-evpn] peer 10.2.2.2 enable [VTEP1-bgp-af-evpn] peer 10.2.2.2 advertise irb [VTEP1-bgp-af-evpn] peer 10.3.3.3 enable [VTEP1-bgp-af-evpn] peer 10.3.3.3 advertise irb [VTEP1-bgp-af-evpn] quit [VTEP1-bgp] ipv4-family vpn-instance vpn1 [VTEP1-bgp-vpn1] import-route direct [VTEP1-bgp-vpn1] advertise l2vpn evpn [VTEP1-bgp-vpn1] quit [VTEP1-bgp] quit
# Configure VTEP2. The configurations of VTEP7 are similar to those of VTEP2.
[VTEP2] bgp 100 [VTEP2-bgp] router-id 10.2.2.2 [VTEP2-bgp] peer 10.1.1.1 as-number 100 [VTEP2-bgp] peer 10.1.1.1 connect-interface LoopBack1 [VTEP2-bgp] l2vpn-family evpn [VTEP2-bgp-af-evpn] peer 10.1.1.1 enable [VTEP2-bgp-af-evpn] peer 10.1.1.1 advertise irb [VTEP2-bgp-af-evpn] quit [VTEP2-bgp] ipv4-family vpn-instance vpn1 [VTEP2-bgp-vpn1] import-route direct [VTEP2-bgp-vpn1] advertise l2vpn evpn [VTEP2-bgp-vpn1] quit [VTEP2-bgp] quit
# Configure VTEP3. The configurations of VTEP8 are similar to those of VTEP3.
[VTEP3] bgp 100 [VTEP3-bgp] router-id 10.3.3.3 [VTEP3-bgp] peer 10.1.1.1 as-number 100 [VTEP3-bgp] peer 10.1.1.1 connect-interface LoopBack1 [VTEP3-bgp] l2vpn-family evpn [VTEP3-bgp-af-evpn] peer 10.1.1.1 enable [VTEP3-bgp-af-evpn] peer 10.1.1.1 advertise irb [VTEP3-bgp-af-evpn] quit [VTEP3-bgp] ipv4-family vpn-instance vpn1 [VTEP3-bgp-vpn1] import-route direct [VTEP3-bgp-vpn1] advertise l2vpn evpn [VTEP3-bgp-vpn1] quit [VTEP3-bgp] quit
- Configure VTEP1 as a reflector and specify VTEP2 and VTEP3 as clients. Configure VTEP6 as a reflector and specify VTEP7 and VTEP8 as clients.
# Configure VTEP1. The configurations of VTEP6 are similar to those of VTEP1.
[VTEP1] bgp 100 [VTEP1-bgp] l2vpn-family evpn [VTEP1-bgp-af-evpn] peer 10.2.2.2 reflect-client [VTEP1-bgp-af-evpn] peer 10.3.3.3 reflect-client [VTEP1-bgp-af-evpn] undo policy vpn-target [VTEP1-bgp-af-evpn] quit [VTEP1-bgp] quit
- Configure the destination IP address of the VXLAN tunnel on VTEP1, VTEP2, and VTEP3 in campus A. Configure the destination IP address of the VXLAN tunnel on VTEP6, VTEP7, and VTEP8 in campus B.
# Configure VTEP1. The configurations of VTEP6 are similar to those of VTEP1.
[VTEP1] interface nve 1 [VTEP1-Nve1] source 10.1.1.1 [VTEP1-Nve1] quit
# Configure VTEP2. The configurations of VTEP7 are similar to those of VTEP2.
[VTEP2] interface nve 1 [VTEP2-Nve1] source 10.2.2.2 [VTEP2-Nve1] vni 10 head-end peer-list protocol bgp [VTEP2-Nve1] quit
# Configure VTEP3. The configurations of VTEP8 are similar to those of VTEP3.
[VTEP3] interface nve 1 [VTEP3-Nve1] source 10.3.3.3 [VTEP3-Nve1] vni 20 head-end peer-list protocol bgp [VTEP3-Nve1] quit
- Configure a distributed VXLAN gateway on VTEP2 and VTEP3 in campus A. Configure a distributed VXLAN gateway on VTEP7 and VTEP8 in campus B.
# Configure VTEP2. The configurations of VTEP7 are similar to those of VTEP2.
[VTEP2] interface vbdif 10 [VTEP2-Vbdif10] ip address 192.168.10.1 24 [VTEP2-Vbdif10] arp distribute-gateway enable [VTEP2-Vbdif10] arp collect host enable [VTEP2-Vbdif10] mac-address 0000-5e00-0101 [VTEP2-Vbdif10] quit
# Configure VTEP3. The configurations of VTEP8 are similar to those of VTEP3.
[VTEP3] interface vbdif 20 [VTEP3-Vbdif20] ip address 192.168.20.1 24 [VTEP3-Vbdif20] arp distribute-gateway enable [VTEP3-Vbdif20] arp collect host enable [VTEP3-Vbdif20] mac-address 0000-5e00-0102 [VTEP3-Vbdif20] quit
- Configure a default route on VTEP1 in campus A and import BGP routes. Configure a default route on VTEP6 in campus B and import BGP routes.
# Configure VTEP1.
[VTEP1] ip route-static vpn-instance vpn1 0.0.0.0 0 NULL0 [VTEP1] bgp 100 [VTEP1-bgp] ipv4-family vpn-instance vpn1 [VTEP1-bgp-vpn1] import-route static [VTEP1-bgp-vpn1] default-route imported [VTEP1] quit
# Configure VTEP6.
[VTEP6] ip route-static vpn-instance vpn1 0.0.0.0 0 NULL0 [VTEP6] bgp 100 [VTEP6-bgp] ipv4-family vpn-instance vpn1 [VTEP6-bgp-vpn1] import-route static [VTEP6-bgp-vpn1] default-route imported [VTEP6] quit
- Verify the configuration results of VXLAN-based intra-campus interconnection.
# After the preceding configuration, run the display vxlan tunnel command on VTEP2, VTEP3, VTEP7, and VTEP8. You can view the VXLAN tunnel information. The following shows the result on VTEP2.
[VTEP2] display vxlan tunnel Tunnel ID Source Destination State Type ---------------------------------------------------------------------------- 24 10.2.2.2 10.1.1.1 up l3 dynamic 20 10.2.2.2 10.3.3.3 up l3 dynamic ---------------------------------------------------------------------------- Number of vxlan tunnel : Total : 2 Static: 0 L2 dynamic: 0 L3 dynamic: 2
# After the preceding configuration, users can communicate with each other across network segments at Layer 3. The following shows the result after ServerA-1 pings VM1 on ServerA-2.
C:\Users\VM1> ping 192.168.20.10 Pinging 192.168.20.10 with 32 bytes of data: Reply from 192.168.20.10: bytes=32 time=1ms TTL=126 Reply from 192.168.20.10: bytes=32 time=1ms TTL=126 Reply from 192.168.20.10: bytes=32 time=1ms TTL=126 Reply from 192.168.20.10: bytes=32 time=1ms TTL=126 Ping statistics for 192.168.20.10: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 1ms, Maximum = 1ms, Average = 1ms - Establish an EVPN peer relationship between VTEP1 in campus A and VTEP6 in campus B.
# Configure VTEP1.
[VTEP1] bgp 100 [VTEP1-bgp] peer 10.6.6.6 as-number 100 [VTEP1-bgp] peer 10.6.6.6 connect-interface LoopBack1 [VTEP1-bgp] l2vpn-family evpn [VTEP1-bgp-af-evpn] peer 10.6.6.6 enable [VTEP1-bgp-af-evpn] quit [VTEP1-bgp] quit
# Configure VTEP6.
[VTEP6] bgp 100 [VTEP6-bgp] peer 10.1.1.1 as-number 100 [VTEP6-bgp] peer 10.1.1.1 connect-interface LoopBack1 [VTEP6-bgp] l2vpn-family evpn [VTEP6-bgp-af-evpn] peer 10.1.1.1 enable [VTEP6-bgp-af-evpn] quit [VTEP6-bgp] quit
- Configure the function to re-originate IP prefix routes in the EVPN routing table on VTEP1 in campus A and VTEP6 in campus B.
# Configure VTEP1.
[VTEP1] bgp 100 [VTEP1-bgp] l2vpn-family evpn [VTEP1-bgp-af-evpn] peer 10.2.2.2 import reoriginate [VTEP1-bgp-af-evpn] peer 10.3.3.3 import reoriginate [VTEP1-bgp-af-evpn] peer 10.6.6.6 advertise route-reoriginated evpn ip [VTEP1-bgp-af-evpn] quit [VTEP1-bgp] quit
# Configure VTEP6.
[VTEP6] bgp 100 [VTEP6-bgp] l2vpn-family evpn [VTEP6-bgp-af-evpn] peer 10.7.7.7 import reoriginate [VTEP6-bgp-af-evpn] peer 10.8.8.8 import reoriginate [VTEP6-bgp-af-evpn] peer 10.1.1.1 advertise route-reoriginated evpn ip [VTEP6-bgp-af-evpn] quit [VTEP6-bgp] quit
- Verify the results of re-originating IP prefix routes between campus A and campus B.
# After the preceding configuration, the IP prefix routes between campus A and campus B are re-originated through the VXLAN tunnel between the campuses. The following shows the result on VTEP1.
[VTEP1] display ip routing-table vpn-instance vpn1 Route Flags: R - relay, D - download to fib, T - to vpn-instance ------------------------------------------------------------------------------ Routing Tables: vpn1 Destinations : 6 Routes : 6 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 60 0 D 0.0.0.0 NULL0 192.168.10.0/24 IBGP 255 0 RD 10.2.2.2 VXLAN 192.168.10.10/32 IBGP 255 0 RD 10.2.2.2 VXLAN 192.168.20.0/24 IBGP 255 0 RD 10.3.3.3 VXLAN 192.168.20.10/32 IBGP 255 0 RD 10.3.3.3 VXLAN 192.168.30.0/24 IBGP 255 0 RD 10.6.6.6 VXLAN 192.168.40.0/24 IBGP 255 0 RD 10.6.6.6 VXLAN - Verify the configuration results of VXLAN-based inter-campus interconnection.
# After the preceding configuration, users can communicate with each other across network segments of different campus networks at Layer 3. The following shows the result after ServerA-1 pings VM1 on ServerB-2.
C:\Users\VM1> ping 192.168.40.10 Pinging 192.168.40.10 with 32 bytes of data: Reply from 192.168.40.10: bytes=32 time=1ms TTL=126 Reply from 192.168.40.10: bytes=32 time=1ms TTL=126 Reply from 192.168.40.10: bytes=32 time=1ms TTL=126 Reply from 192.168.40.10: bytes=32 time=1ms TTL=126 Ping statistics for 192.168.40.10: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 1ms, Maximum = 1ms, Average = 1ms
Configuration Files
VTEP1 configuration file
# sysname VTEP1 # ip vpn-instance vpn1 ipv4-family route-distinguisher 1:100 vpn-target 1:100 10:100 export-extcommunity evpn vpn-target 1:100 10:100 import-extcommunity evpn vxlan vni 100 # interface GigabitEthernet0/0/1 undo portswitch ip address 192.168.1.2 255.255.255.0 # interface GigabitEthernet0/0/2 undo portswitch ip address 192.168.2.1 255.255.255.0 # interface GigabitEthernet0/0/3 undo portswitch ip address 192.168.6.1 255.255.255.0 # interface LoopBack1 ip address 10.1.1.1 255.255.255.255 # interface Nve1 source 10.1.1.1 # bgp 100 router-id 10.1.1.1 peer 10.2.2.2 as-number 100 peer 10.2.2.2 connect-interface LoopBack1 peer 10.3.3.3 as-number 100 peer 10.3.3.3 connect-interface LoopBack1 peer 10.6.6.6 as-number 100 peer 10.6.6.6 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 10.2.2.2 enable peer 10.3.3.3 enable peer 10.6.6.6 enable # l2vpn-family evpn undo policy vpn-target peer 10.2.2.2 enable peer 10.2.2.2 advertise irb peer 10.2.2.2 reflect-client peer 10.2.2.2 import reoriginate peer 10.3.3.3 enable peer 10.3.3.3 advertise irb peer 10.3.3.3 reflect-client peer 10.3.3.3 import reoriginate peer 10.6.6.6 enable peer 10.6.6.6 advertise route-reoriginated evpn ip # ipv4-family vpn-instance vpn1 default-route imported import-route direct import-route static advertise l2vpn evpn # ospf 1 router-id 10.1.1.1 area 0.0.0.0 network 10.1.1.1 0.0.0.0 network 192.168.1.0 0.0.0.255 network 192.168.2.0 0.0.0.255 network 192.168.6.0 0.0.0.255 # ip route-static vpn-instance vpn1 0.0.0.0 0.0.0.0 NULL0 # return
VTEP2 configuration file
# sysname VTEP2 # vcmp role silent # ip vpn-instance vpn1 ipv4-family route-distinguisher 2:100 vpn-target 1:100 export-extcommunity evpn vpn-target 1:100 import-extcommunity evpn vxlan vni 100 # evpn vpn-instance evpn10 bd-mode route-distinguisher 2:10 vpn-target 1:100 10:1 export-extcommunity vpn-target 10:1 import-extcommunity # bridge-domain 10 vxlan vni 10 evpn binding vpn-instance evpn10 # interface GigabitEthernet0/0/1 undo portswitch ip address 192.168.1.1 255.255.255.0 # interface GigabitEthernet0/0/2 port link-type trunk # interface GigabitEthernet0/0/2.1 mode l2 encapsulation dot1q vid 10 bridge-domain 10 # interface LoopBack1 ip address 10.2.2.2 255.255.255.255 # interface Vbdif10 mac-address 0000-5e00-0101 ip binding vpn-instance vpn1 arp collect host enable arp distribute-gateway enable ip address 192.168.10.1 255.255.255.0 # interface Nve1 source 10.2.2.2 vni 10 head-end peer-list protocol bgp # bgp 100 router-id 10.2.2.2 peer 10.1.1.1 as-number 100 peer 10.1.1.1 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 10.1.1.1 enable # l2vpn-family evpn policy vpn-target peer 10.1.1.1 enable peer 10.1.1.1 advertise irb # ipv4-family vpn-instance vpn1 import-route direct advertise l2vpn evpn # ospf 1 router-id 10.2.2.2 area 0.0.0.0 network 10.2.2.2 0.0.0.0 network 192.168.1.0 0.0.0.255 # return
VTEP3 configuration file
# sysname VTEP3 # vcmp role silent # ip vpn-instance vpn1 ipv4-family route-distinguisher 3:100 vpn-target 1:100 export-extcommunity evpn vpn-target 1:100 import-extcommunity evpn vxlan vni 100 # evpn vpn-instance evpn20 bd-mode route-distinguisher 3:20 vpn-target 1:100 20:1 export-extcommunity vpn-target 20:1 import-extcommunity # bridge-domain 20 vxlan vni 20 evpn binding vpn-instance evpn20 # interface GigabitEthernet0/0/1 undo portswitch ip address 192.168.2.2 255.255.255.0 # interface GigabitEthernet0/0/2 port link-type trunk # interface GigabitEthernet0/0/2.1 mode l2 encapsulation dot1q vid 20 bridge-domain 20 # interface LoopBack1 ip address 10.3.3.3 255.255.255.255 # interface Vbdif20 mac-address 0000-5e00-0102 ip binding vpn-instance vpn1 arp collect host enable arp distribute-gateway enable ip address 192.168.20.1 255.255.255.0 # interface Nve1 source 10.3.3.3 vni 20 head-end peer-list protocol bgp # bgp 100 router-id 10.3.3.3 peer 10.1.1.1 as-number 100 peer 10.1.1.1 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 10.1.1.1 enable # l2vpn-family evpn policy vpn-target peer 10.1.1.1 enable peer 10.1.1.1 advertise irb # ipv4-family vpn-instance vpn1 import-route direct advertise l2vpn evpn # ospf 1 router-id 10.3.3.3 area 0.0.0.0 network 10.3.3.3 0.0.0.0 network 192.168.2.0 0.0.0.255 # return
Switch4 configuration file
# sysname Switch4 # vlan batch 10 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 # interface GigabitEthernet0/0/2 port link-type access port default vlan 10 # return
Switch5 configuration file
# sysname Switch5 # vlan batch 20 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 20 # interface GigabitEthernet0/0/2 port link-type access port default vlan 20 # return
VTEP6 configuration file
# sysname VTEP6 # ip vpn-instance vpn1 ipv4-family route-distinguisher 6:100 vpn-target 6:100 10:100 export-extcommunity evpn vpn-target 6:100 10:100 import-extcommunity evpn vxlan vni 100 # interface GigabitEthernet0/0/1 undo portswitch ip address 192.168.3.2 255.255.255.0 # interface GigabitEthernet0/0/2 undo portswitch ip address 192.168.4.1 255.255.255.0 # interface GigabitEthernet0/0/3 undo portswitch ip address 192.168.8.1 255.255.255.0 # interface LoopBack1 ip address 10.6.6.6 255.255.255.255 # interface Nve1 source 10.6.6.6 # bgp 100 router-id 10.6.6.6 peer 10.1.1.1 as-number 100 peer 10.1.1.1 connect-interface LoopBack1 peer 10.7.7.7 as-number 100 peer 10.7.7.7 connect-interface LoopBack1 peer 10.8.8.8 as-number 100 peer 10.8.8.8 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 10.1.1.1 enable peer 10.7.7.7 enable peer 10.8.8.8 enable # l2vpn-family evpn undo policy vpn-target peer 10.1.1.1 enable peer 10.1.1.1 advertise route-reoriginated evpn ip peer 10.7.7.7 enable peer 10.7.7.7 advertise irb peer 10.7.7.7 reflect-client peer 10.7.7.7 import reoriginate peer 10.8.8.8 enable peer 10.8.8.8 advertise irb peer 10.8.8.8 reflect-client peer 10.8.8.8 import reoriginate # ipv4-family vpn-instance vpn1 default-route imported import-route direct import-route static advertise l2vpn evpn # ospf 1 router-id 10.6.6.6 area 0.0.0.0 network 10.6.6.6 0.0.0.0 network 192.168.3.0 0.0.0.255 network 192.168.4.0 0.0.0.255 network 192.168.8.0 0.0.0.255 # ip route-static vpn-instance vpn1 0.0.0.0 0.0.0.0 NULL0 # return
VTEP7 configuration file
# sysname VTEP7 # vcmp role silent # ip vpn-instance vpn1 ipv4-family route-distinguisher 7:100 vpn-target 6:100 export-extcommunity evpn vpn-target 6:100 import-extcommunity evpn vxlan vni 100 # evpn vpn-instance evpn30 bd-mode route-distinguisher 7:30 vpn-target 6:100 30:1 export-extcommunity vpn-target 30:1 import-extcommunity # bridge-domain 30 vxlan vni 30 evpn binding vpn-instance evpn30 # interface GigabitEthernet0/0/1 undo portswitch ip address 192.168.3.1 255.255.255.0 # interface GigabitEthernet0/0/2 port link-type trunk # interface GigabitEthernet0/0/2.1 mode l2 encapsulation dot1q vid 30 bridge-domain 30 # interface LoopBack1 ip address 10.7.7.7 255.255.255.255 # interface Vbdif30 mac-address 0000-5e00-0103 ip binding vpn-instance vpn1 arp collect host enable arp distribute-gateway enable ip address 192.168.30.1 255.255.255.0 # interface Nve1 source 10.7.7.7 vni 30 head-end peer-list protocol bgp # bgp 100 router-id 10.7.7.7 peer 10.6.6.6 as-number 100 peer 10.6.6.6 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 10.6.6.6 enable # l2vpn-family evpn policy vpn-target peer 10.6.6.6 enable peer 10.6.6.6 advertise irb # ipv4-family vpn-instance vpn1 import-route direct advertise l2vpn evpn # ospf 1 router-id 10.7.7.7 area 0.0.0.0 network 10.7.7.7 0.0.0.0 network 192.168.3.0 0.0.0.255 # return
VTEP8 configuration file
# sysname VTEP8 # vcmp role silent # ip vpn-instance vpn1 ipv4-family route-distinguisher 8:100 vpn-target 6:100 export-extcommunity evpn vpn-target 6:100 import-extcommunity evpn vxlan vni 100 # evpn vpn-instance evpn40 bd-mode route-distinguisher 8:40 vpn-target 6:100 40:1 export-extcommunity vpn-target 40:1 import-extcommunity # bridge-domain 40 vxlan vni 40 evpn binding vpn-instance evpn40 # interface GigabitEthernet0/0/1 undo portswitch ip address 192.168.4.2 255.255.255.0 # interface GigabitEthernet0/0/2 port link-type trunk # interface GigabitEthernet0/0/2.1 mode l2 encapsulation dot1q vid 40 bridge-domain 40 # interface LoopBack1 ip address 10.8.8.8 255.255.255.255 # interface Vbdif40 mac-address 0000-5e00-0104 ip binding vpn-instance vpn1 arp collect host enable arp distribute-gateway enable ip address 192.168.40.1 255.255.255.0 # interface Nve1 source 10.8.8.8 vni 40 head-end peer-list protocol bgp # bgp 100 router-id 10.8.8.8 peer 10.6.6.6 as-number 100 peer 10.6.6.6 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 10.6.6.6 enable # l2vpn-family evpn policy vpn-target peer 10.6.6.6 enable peer 10.6.6.6 advertise irb # ipv4-family vpn-instance vpn1 import-route direct advertise l2vpn evpn # ospf 1 router-id 10.8.8.8 area 0.0.0.0 network 10.8.8.8 0.0.0.0 network 192.168.4.0 0.0.0.255 # return
Switch9 configuration file
# sysname Switch9 # vlan batch 30 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 30 # interface GigabitEthernet0/0/2 port link-type access port default vlan 30 # return
Switch10 configuration file
# sysname Switch10 # vlan batch 40 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 40 # interface GigabitEthernet0/0/2 port link-type access port default vlan 40 # return