Example for Using Advanced ACLs to Restrict Mutual Access Between Network Segments
Networking Requirements
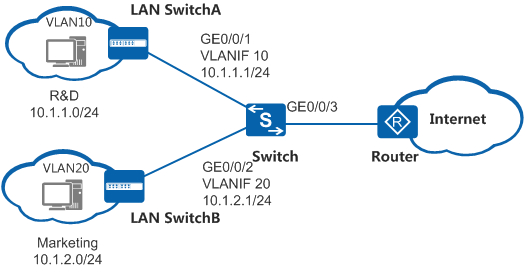
As shown in Figure 1, the departments of an enterprise are connected through a switch. To facilitate network management, the administrator allocates IP addresses of different network segments to the R&D and marketing departments. In addition, the administrator adds the two departments to different VLANs for broadcast domain isolation. For information security purposes, the enterprise requires that the switch prevent user hosts on different network segments from communicating with each other.
Configuration Roadmap
The configuration roadmap is as follows:
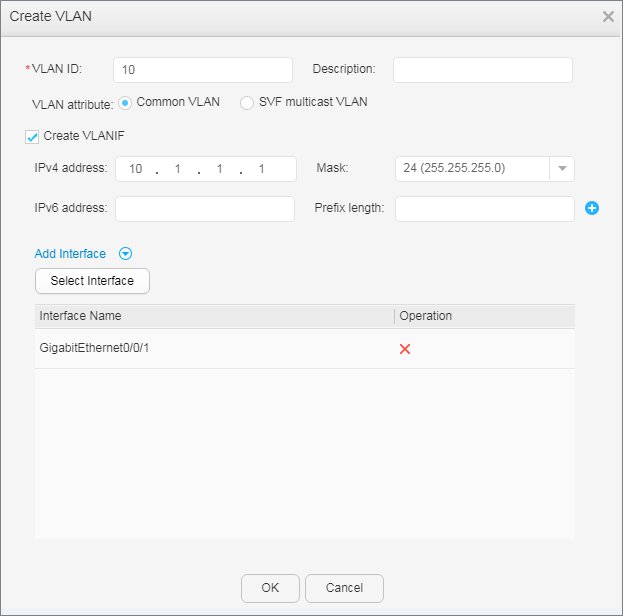
- Configure VLANs and configure IP addresses for VLANIF interfaces.
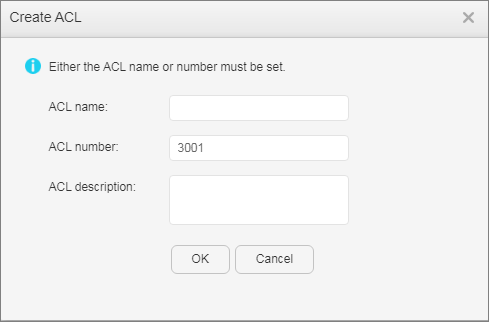
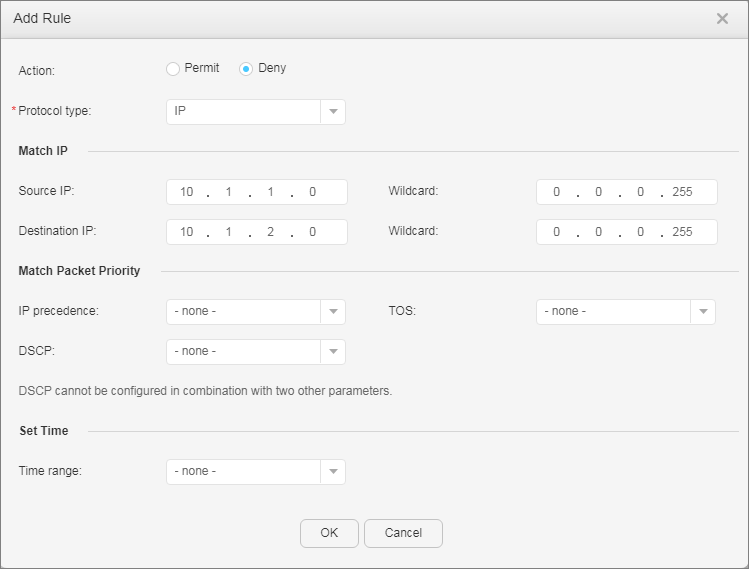
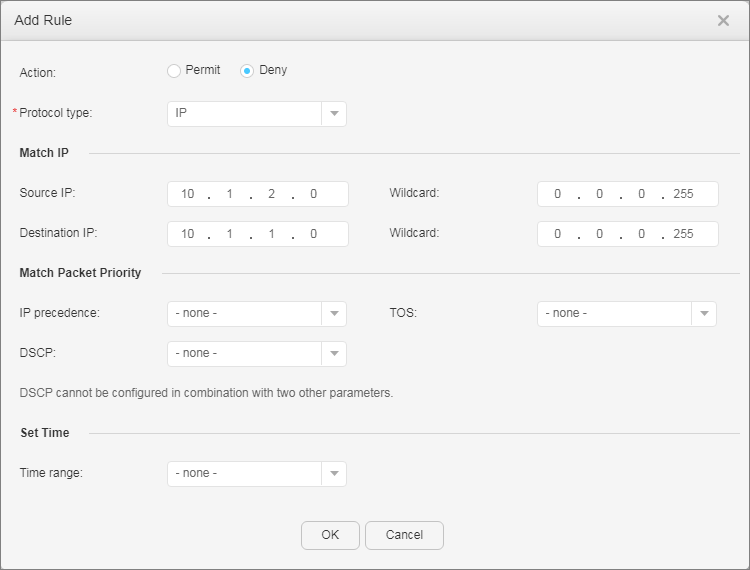
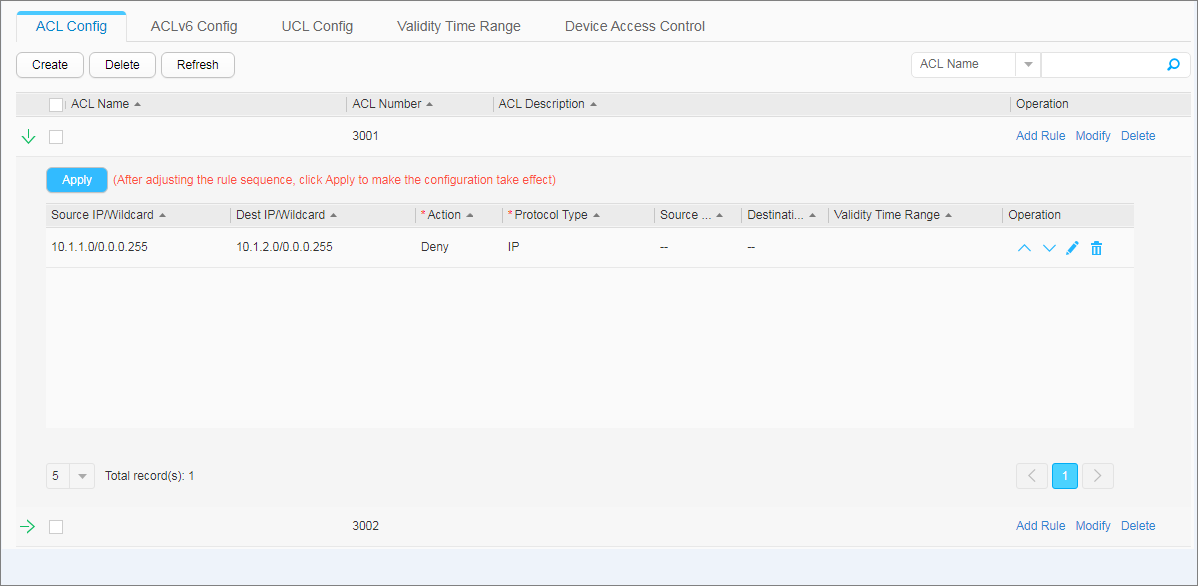
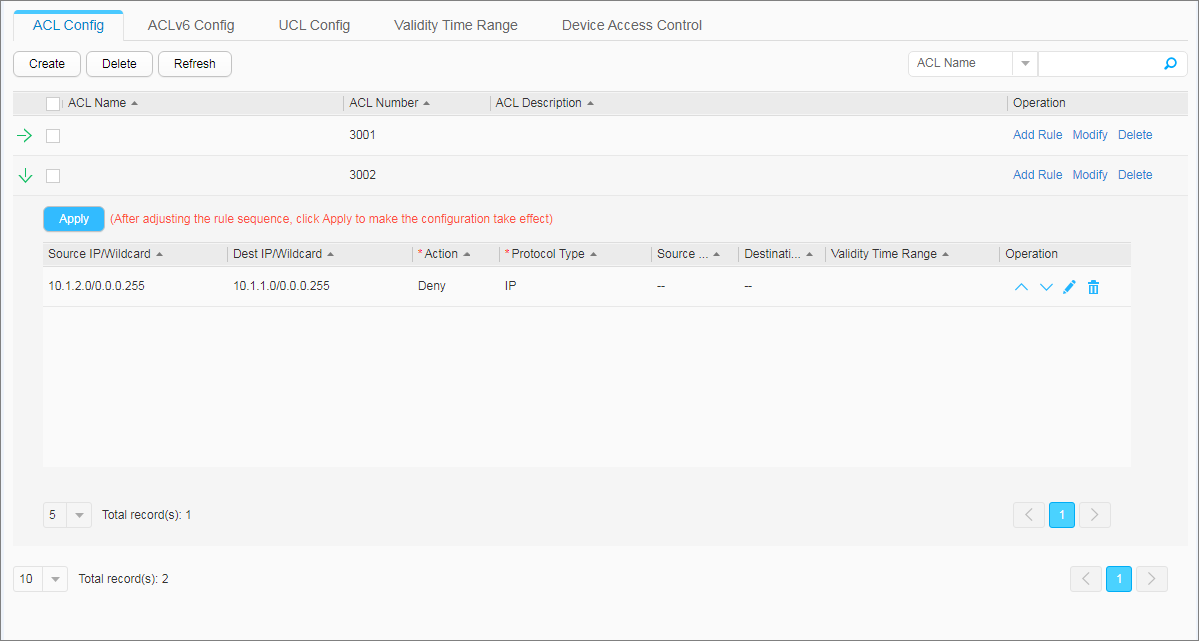
- Configure advanced ACLs.
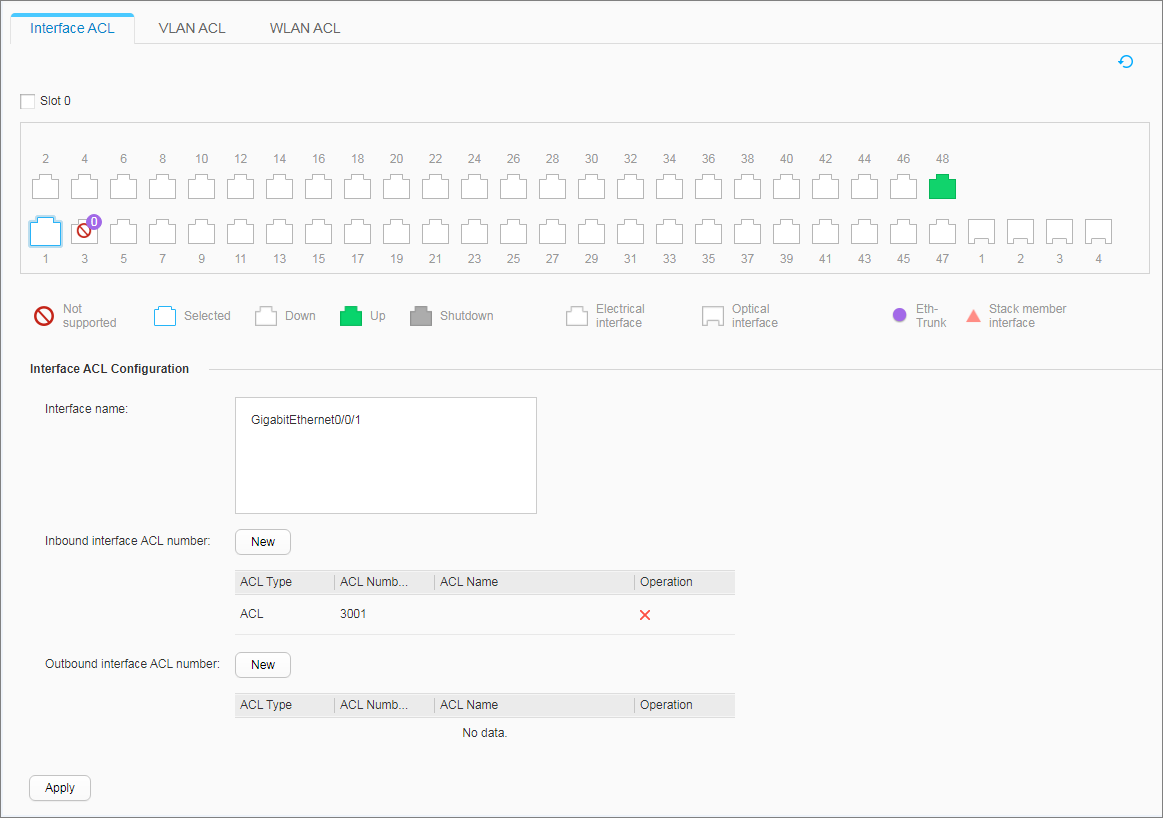
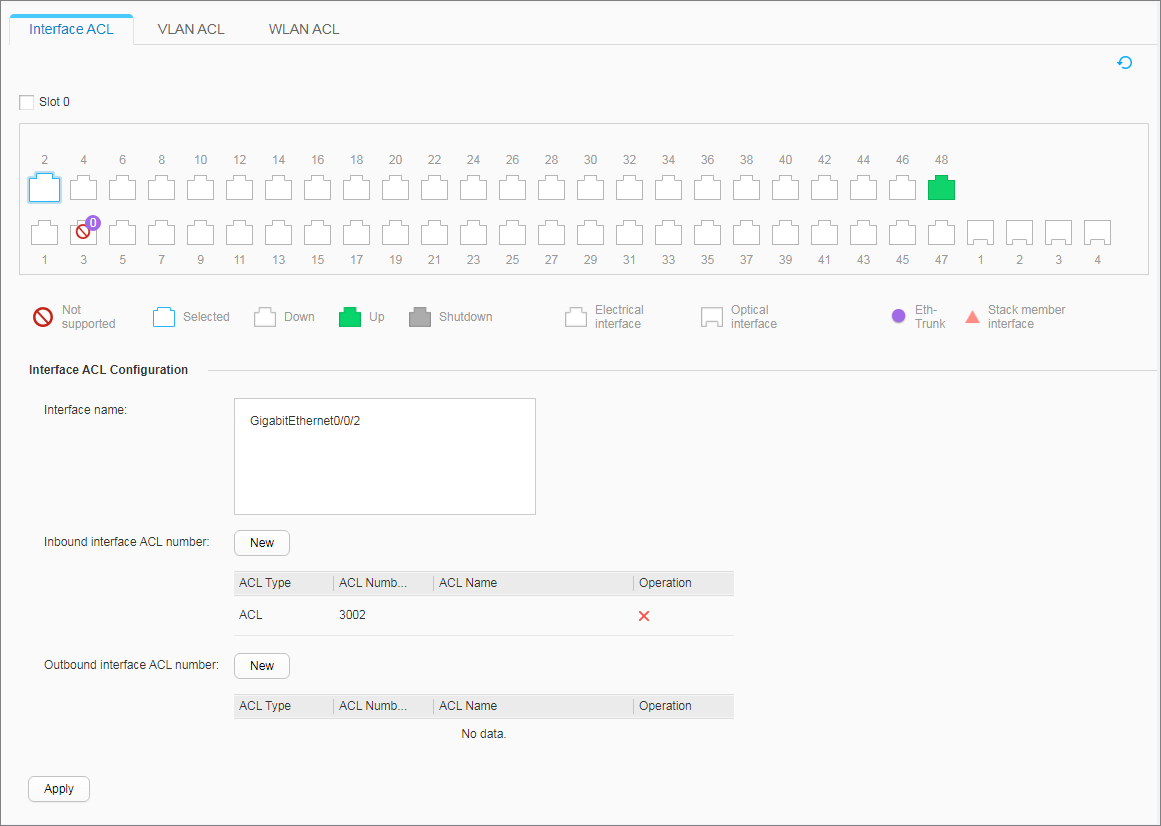
- Apply the ACLs to enable the device to filter user packets based on the source and destination IP addresses, thereby restricting mutual access between users on different network segments.
Procedure
- Add interfaces to VLANs and assign IP addresses to the VLANIF interfaces.
- Configure ACLs.
- Apply the ACLs.