WIDS
Procedure
- View device detection results.
- Choose Monitoring > Wireless Service > WIDS. The WIDS page is displayed.
- View device detection results in Device Detection. Table 1 describes the device detection parameters.
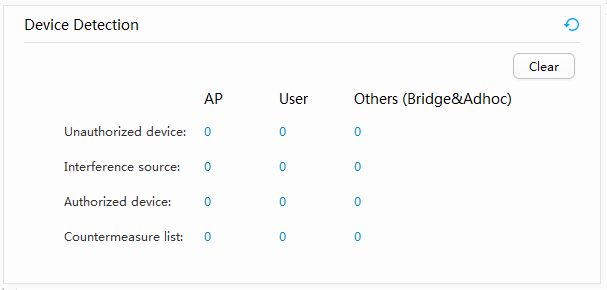
- Click a number in the detection result list.
The detected device information is displayed in Device Detection Information. Table 2 describes the parameters.
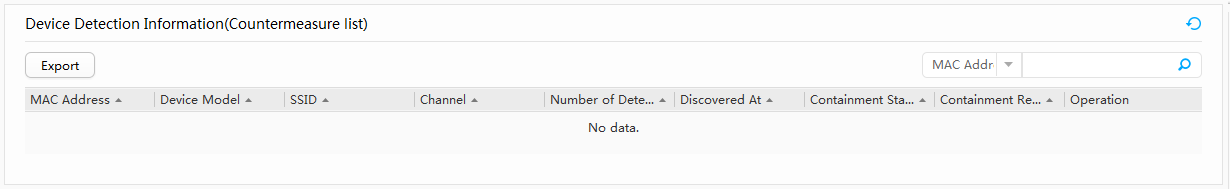
Table 2 Device detection parameters Parameter
Description
MAC Address
MAC address of the device.
Device Model
-
SSID
SSID of the device.
Channel
Channel used by the device.
Number of Detected APs
Number of APs that detect the device.
Discovered At
Time when the device is detected.
Containment Status Whether the rogue device is contained. Containment Reason Reason for the device to be contained. Operation Manual containment. - Click Export. The device detection information is exported in a .csv file.
- Select a device in the detected device list and click View Discovered APs. Information about the APs that detect
the device is displayed. Table 3 describes the parameters.
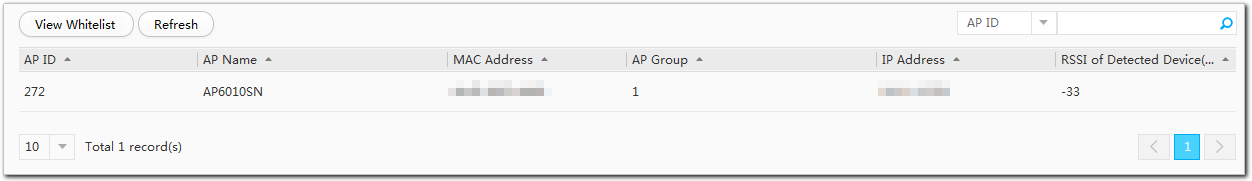
Table 3 Parameters of APs that detect the device Parameter
Description
AP ID
ID of the AP that detects the device.
AP Name
Name of the AP that detects the device.
MAC Address
MAC address of the AP that detects the device.
AP Group
AP group to which the AP that detects the device belongs.
IP Address
IP address of the AP that detects the device.
RSSI of Detected Device
RSSI of the detected device.
- In the list of APs that detect the device, select an AP and click View Whitelist to check the WIDS whitelist of the AP.
- Clear device detection statistics.
- Choose Monitoring > Wireless Service > WIDS. The WIDS page is displayed.
- Click Clear in Device Detection.
- View attack detection results.
- Choose Monitoring > Wireless Service > WIDS. The WIDS page is displayed.
- View attack detection results in Attack Detection. Table 4 describes the attack detection parameters.
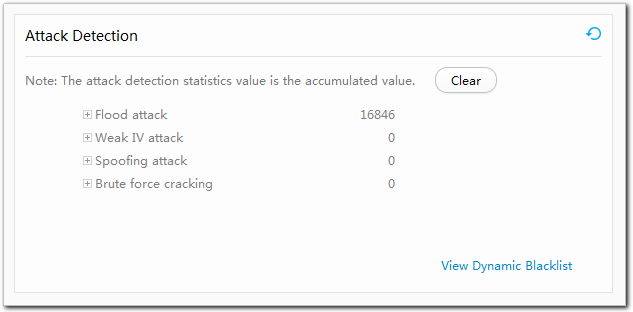
Table 4 Attack detection parameters Parameter
Description
Flood attack
Number of flood attacks, including the following types of attacks:
- Flood attack of probe request frames
- Flood attack of authentication request frames
- Flood attack of deauthentication request frames
- Flood attack of association request frames
- Flood attack of disassociation request frames
- Flood attack of reassociation request frames
- Flood attack of action frames
- Flood attack of EAPOL authentication request frames
- Flood attack of EAPOL offline frames
Weak IV attack
Number of weak IV attacks.
Spoofing attack
Number of spoofing attacks, including the following types of attacks:
- Attack of spoofing deauthentication frames
- Attack of spoofing disassociation frames
- Other types of spoofing frames
Brute force cracking
Number of brute force cracking attacks, including the following types of attacks:
- Brute force cracking attack in WEP-SK authentication mode
- Brute force cracking attack in WPA-PSK authentication mode
- Brute force cracking attack in WPA2-PSK authentication mode
- Brute force cracking attack in WAPI authentication mode
- Click a number in the attack detection result list to
view details. Table 5 describes the parameters.
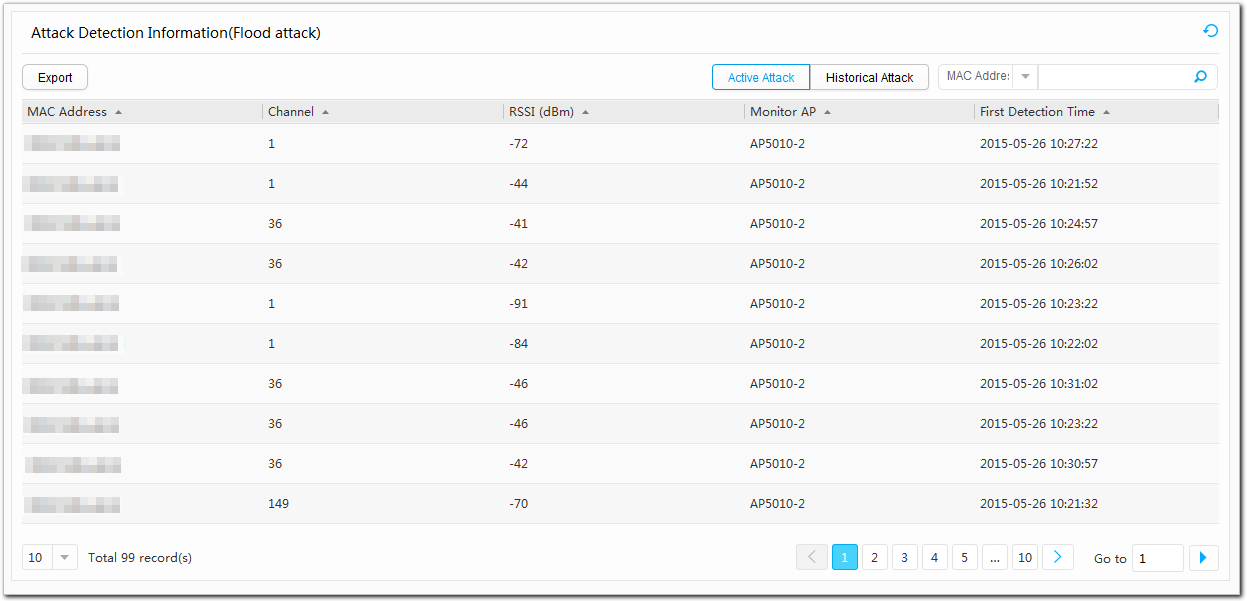
Table 5 Attack detection parameters Parameter
Description
MAC Address
MAC address of the attacking device.
Channel
Channel used by the attacking device.
RSSI
RSSI of the attacking device.
Monitor AP
Name of the AP that detects attacks.
First DetectionTime
Time when attacks are detected.

By default, information about the active attacks is displayed. You can click Historical Attack to check historical attack detection records.
- Click Export. The device detection information is exported in a .csv file.
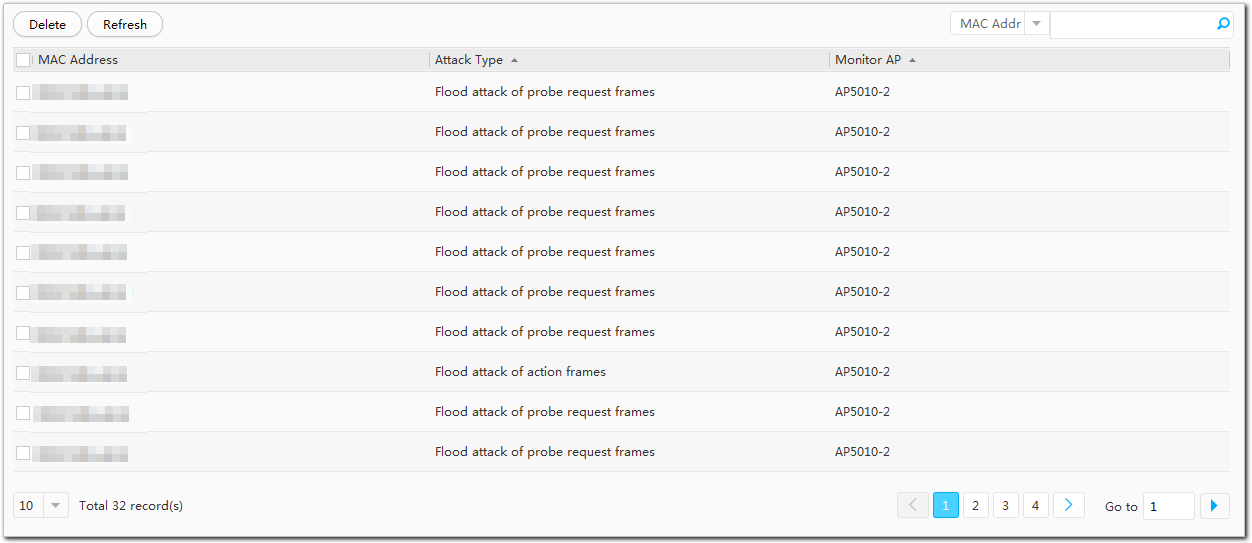
- Click View Dynamic Blacklist.
The View Dynamic Blacklist page is displayed. Table 6 describes
the dynamic blacklist parameters.
- Clear attack detection statistics.
- Choose Monitoring > Wireless Service > WIDS. The WIDS page is displayed.
- Click Clear in Attack Detection.