Authentication Scheme
Procedure
- Create an authentication scheme.
- Modify an authentication scheme.
- Choose . The Authentication Scheme List page is displayed.
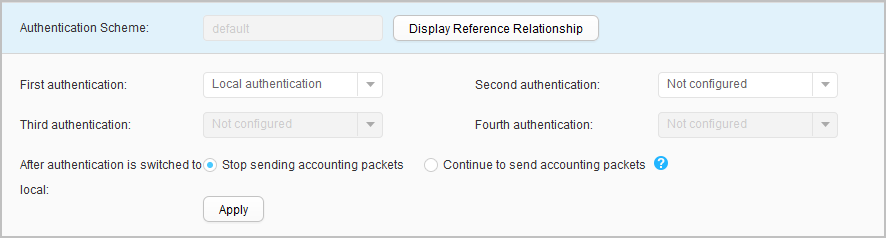
- Click the authentication scheme to modify. The authentication scheme configuration page is displayed.
- Set parameters for modifying an authentication scheme. Table 1 describes the parameters for modifying an authentication scheme.
- Click Apply.
- Delete an authentication scheme.
- Choose . The Authentication Scheme List page is displayed.
- Select the profile that you want to delete and click Delete. In the Confirm dialog box that is displayed, click OK.
- Display the profile reference relationship.