Example for Configuring Dynamic ACL Delivery Through a RADIUS Server
This section provides an example for configuring dynamic ACL delivery through a RADIUS server.
Networking Requirements
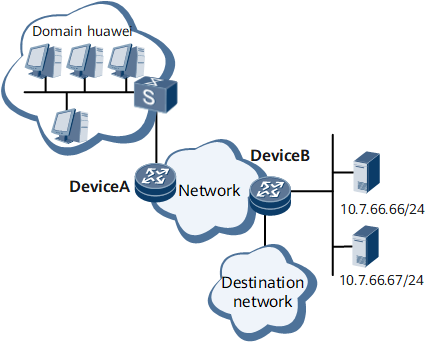
On the network shown in Figure 1, users in the domain named huawei access the network through Device A. Device B functions as the access server for the target network. The users can access the target network only through Device A and Device B and after they are being authenticated by the remote server. Remote authentication on Device B is as follows:
RADIUS servers are used to perform authentication on the access users.
The RADIUS server at 10.7.66.66/24 functions as the primary authentication server, and the RADIUS server at 10.7.66.67/24 functions as the secondary authentication server. The default authentication port number 1812 is used.
Configuration Roadmap
The configuration roadmap is as follows:
Configure a RADIUS server group, an authentication scheme, and dynamic ACL delivery.
Bind the RADIUS server group and authentication scheme and apply dynamic ACL delivery to the domain.

Run the adminuser-priority command in the domain view if you want to configure a user not in the default_admin domain to log in as an administrator. The domain must be configured as the authentication domain for BAS access users.
Data Preparation
To complete the configuration, you need the IP addresses of the primary and secondary RADIUS authentication servers.
Procedure
- Configure a RADIUS server group, an authentication scheme, and dynamic ACL delivery.
# Configure a RADIUS server group named shiva.
<Device> system-view [~Device] radius-server group shiva
# Configure an IP address and a port number for the primary RADIUS authentication server.
[*Device-radius-shiva] radius-server authentication 10.7.66.66 1812
# Configure an IP address and a port number for the secondary RADIUS authentication server.
[*Device-radius-shiva] radius-server authentication 10.7.66.67 1812
# Configure a shared key and the number of retransmissions for the RADIUS server group.
[*Device-radius-shiva] radius-server shared-key-cipher it-is-my-secret1 [*Device-radius-shiva] radius-server retransmit 2 [*Device-radius-shiva] commit [~Device-radius-shiva] quit
# Configure dynamic ACL delivery through the RADIUS server.
[~Device] aaa [~Device-aaa] remote-download acl enable
# Configure authentication scheme 1, with RADIUS as the authentication mode.
[~Device-aaa] authentication-scheme 1 [*Device-aaa-authen-1] authentication-mode radius [*Device-aaa-authen-1] commit [~Device-aaa-authen-1] quit
- Configure a domain named huawei and bind authentication scheme 1 and RADIUS server group shiva to the domain.
[~Device-aaa] domain huawei [*Device-aaa-domain-huawei] authentication-scheme 1 [*Device-aaa-domain-huawei] radius-server group shiva [*Device-aaa-domain-huawei] commit [*Device-aaa-domain-huawei] quit
- Configure user templates and BAS interfaces.
[~Device-aaa] default-password template huawei cipher huawei123 [~Device-aaa] default-user-name template huawei include sysname [*Device-aaa] commit [*Device-aaa] quit
[~Device] interface GigabitEthernet 0/1/1.1 [*Device-GigabitEthernet0/1/1.1] commit [~Device-GigabitEthernet0/1/1.1] user-vlan 1 [~Device-GigabitEthernet0/1/1.1-vlan-1-1] quit [~Device-GigabitEthernet0/1/1.1] bas [~Device-GigabitEthernet0/1/1.1-bas] access-type layer2-subscriber default-domain authentication huawei [~Device-GigabitEthernet0/1/1.1-bas] authentication-method bind [*Device-GigabitEthernet0/1/1.1-bas] user detect retransmit 2 interval 0 [*Device-GigabitEthernet0/1/1.1-bas] default-user-name-template huawei [*Device-GigabitEthernet0/1/1.1-bas] commit [~Device-GigabitEthernet0/1/1.1-bas] default-password-template huawei [~Device-GigabitEthernet0/1/1.1-bas] quit [~Device-GigabitEthernet0/1/1.1] quit
- Verify the configuration.
Run the display aaa remote-download acl item verbose command on the router to check RADIUS server group configurations.
<HUAWEI> display aaa remote-download acl item verbose ------------------------------------------------------------------------------- ClassifierName ReferedNumByUser RuleNumber ClassifierType ------------------------------------------------------------------------------- c1 1 1 remote ------------------------------------------------------------------------------- rc=c1; rule:(number: 1) ipv4;ruleid=5;dir=in;su-group=huawei;dipv4=10.1.0.1/24; rb=b1; deny; The used user-id table are : 0 ------------------------------------------------------------------------------- Total Classifier-Behavior Number : 1
Configuration Files
# sysname HUAWEI # user-group huawei # radius-server group shiva radius-server authentication 10.7.66.66 1812 weight 0 radius-server authentication 10.7.66.67 1812 weight 0 radius-server shared-key-cipher %^%#h{FXVBLZX9#`VI]EWUUaOSHGd5E!.1DGeVYEie=%^% radius-server retransmit 2 # aaa remote-download acl enable default-password template huawei cipher %^%#M*p1,itN!4kQo5%Dc1s(whyJCM@xt0u[,,XMWG/O%^% default-user-name template huawei include sysname # authentication-scheme 1 # authorization-scheme default # domain huawei authentication-scheme 1 radius-server group shiva ip-pool huawei user-group huawei # interface GigabitEthernet0/1/1 # interface GigabitEthernet0/1/1.1 user-vlan 1 bas # access-type layer2-subscriber default-domain authentication huawei authentication-method bind user detect retransmit 2 interval 0 default-user-name-template huawei default-password-template huawei # # return