Example for Configuring BRAS Access Through L3VPN Termination
This section provides an example for configuring BRAS access through L3VPN termination.
Networking Requirements
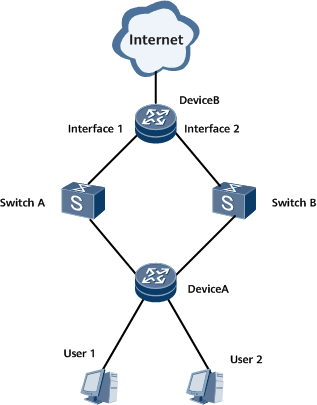
Device B uses OSPF to exchange traffic with Device A through interfaces on multiple boards in load balancing mode. Traffic from the same user may be sent from different boards. Device B uses policy-based routing (PBR) to send traffic from the same user but different boards through the backplane to the same board for Layer 3 user authentication, as shown in Figure 1.

Only Layer 3 static user access is supported in scenarios of BRAS access through L3VPN termination.
Interfaces 1 and 2 in this example represent VE1/0/1 and VE2/0/1, respectively.
- Device A sends upstream traffic to different interfaces on Device B in load balancing mode.
Device B adds all the inbound interfaces to an L3VPN and configures PBR. Then, Device B routes all traffic from the same user to the specified next hop based on the source IP address/VLAN ID/DSCP priority. The outbound interface of the next hop directly connects to the BAS interface and resides on the same network segment as the BAS interface.
After user traffic arrives at the BAS interface and the user goes online, user forwarding entries are delivered. Subsequent user traffic will then be authenticated and forwarded based on these forwarding entries.
Downstream traffic is forwarded through the BAS interface to the L3VPN domain based on user forwarding entries.
Device B then sends downstream traffic in the L3VPN domain to Device A along routes (the traffic can be balanced). Then, Device A forwards the traffic to the user.
Configuration Roadmap
The configuration roadmap is as follows:
- Configuring Local L3VPN
Configure PBR to redirect user traffic to the primary and backup next hops. If the primary next hop fails, traffic is automatically switched to the backup next hop to trigger user login.
Configure user access interfaces (User traffic enters the interface, not the BAS interface).
Configure IP addresses as the redirection next hop IP addresses.
Configure an authentication domain on the BAS interface..
Configure BAS interfaces.
- Configure Layer 3 static users.
Data Preparation
To complete the configuration, you need the following data:
VE-group number
Local L3VPN name
OSPF parameters
Layer 3 user authentication mode, accounting mode, and authentication domain name
Interface IP addresses
Configuration Procedure
Configure a local L3VPN.
Configure a local L3VPN on Device B.
<HUAWEI> system-view [~HUAWEI] sysname DeviceB [*HUAWEI] commit [~DeviceB] ip vpn-instance access [*DeviceB-vpn-instance-access] ipv4-family [*DeviceB-vpn-instance-access-af-ipv4] route-distinguisher 200:1 [*DeviceB-vpn-instance-access-af-ipv4] vpn-target 111:1 both [*DeviceB-vpn-instance-access-af-ipv4] commit [~DeviceB-vpn-instance-access-af-ipv4] quit [~DeviceB-vpn-instance-access] quit
Configure PBR on DeviceB.
Configure PBR to redirect user traffic to the primary and backup next hops based on the source IP address. If the primary next hop fails, traffic is automatically switched to the backup next hop to trigger user login.
[~DeviceB] acl 3000 [*DeviceB-acl4-advance-3000] rule permit ip source 192.168.1.1 255.255.255.255 [*DeviceB-acl4-advance-3000] quit [*DeviceB] traffic classifier class1 [*DeviceB-classifier-class1] if-match acl 3000 [*DeviceB-classifier-class1] quit [*DeviceB] traffic behavior behavior1 [*DeviceB-behavior-behavior1] redirect ipv4-multinhp nhp 192.168.112.2 vpn access nhp 192.168.223.2 vpn access non-revertive [*DeviceB-behavior-behavior1] quit [*DeviceB] traffic policy loadbalance [*DeviceB-trafficpolicy-loadbalance] share-mode [*DeviceB-trafficpolicy-loadbalance] classifier class1 behavior behavior1 [*DeviceB-trafficpolicy-loadbalance] quit [*DeviceB] commit
Configure the user access interface where user traffic is transmitted. This interface is not a BAS interface.
[~DeviceB] interface GigabitEthernet1/0/3.100 [*DeviceB-GigabitEthernet1/0/3.100] vlan-type dot1q 100 [*DeviceB-GigabitEthernet1/0/3.100] ip binding vpn-instance access [*DeviceB-GigabitEthernet1/0/3.100] ip address 192.168.111.1 255.255.255.0 [*DeviceB-GigabitEthernet1/0/3.100] traffic-policy loadbalance inbound [*DeviceB-GigabitEthernet1/0/3.100] ospf enable 100 area 0.0.0.0 [*DeviceB-GigabitEthernet1/0/3.100] quit [*DeviceB] interface GigabitEthernet2/2/7.100 [*DeviceB-GigabitEthernet2/2/7.100] vlan-type dot1q 100 [*DeviceB-GigabitEthernet2/2/7.100] ip binding vpn-instance access [*DeviceB-GigabitEthernet2/2/7.100] ip address 192.168.222.1 255.255.255.0 [*DeviceB-GigabitEthernet2/2/7.100] traffic-policy loadbalance inbound [*DeviceB-GigabitEthernet2/2/7.100] ospf enable 100 area 0.0.0.0 [*DeviceB-GigabitEthernet2/2/7.100] quit
Configure the outbound interface of the redirection next hop.
[*DeviceB] interface Virtual-Ethernet1/0/0 [*DeviceB-Virtual-Ethernet1/0/0] ve-group 1 l3-terminate [*DeviceB-Virtual-Ethernet1/0/0] quit [*DeviceB] interface Virtual-Ethernet1/0/0.100 [*DeviceB-Virtual-Ethernet1/0/0.100] vlan-type dot1q 100 [*DeviceB-Virtual-Ethernet1/0/0.100] ip address 192.168.112.1 255.255.255.0 [*DeviceB-Virtual-Ethernet1/0/0.100] quit
Configure the backup interface.
[*DeviceB] interface Virtual-Ethernet2/0/0 [*DeviceB-Virtual-Ethernet2/0/0] ve-group 2 l3-terminate [*DeviceB-Virtual-Ethernet2/0/0] quit [*DeviceB] interface Virtual-Ethernet2/0/0.100 [*DeviceB-Virtual-Ethernet2/0/0.100] vlan-type dot1q 100 [*DeviceB-Virtual-Ethernet2/0/0.100] ip address 192.168.223.1 255.255.255.0 [*DeviceB-Virtual-Ethernet2/0/0.100] quit [*DeviceB] commit
Configure an authentication domain on the BAS interface.
# Configure an authentication scheme.
[~DeviceB] aaa [~DeviceB-aaa] authentication-scheme auth2 [*DeviceB-aaa-authen-auth2] authentication-mode radius [*DeviceB-aaa-authen-auth2] commit [~DeviceB-aaa-authen-auth2] quit
# Configure an accounting scheme.
[~DeviceB-aaa] accounting-scheme acct2 [*DeviceB-aaa-accounting-acct2] accounting-mode radius [*DeviceB-aaa-accounting-acct2] commit [~DeviceB-aaa-accounting-acct2] quit [~DeviceB-aaa] quit
# Configure a RADIUS server group.
[~DeviceB] radius-server group rd2 [*DeviceB-radius-rd2] radius-server authentication 192.168.8.249 1812 [*DeviceB-radius-rd2] radius-server accounting 192.168.8.249 1813 [*DeviceB-radius-rd2] commit [~DeviceB-radius-rd2] radius-server type standard [~DeviceB-radius-rd2] radius-server shared-key-cipher it-is-my-secret1 [*DeviceB-radius-rd2] commit [~DeviceB-radius-rd2] quit
# Configure an address pool.
[~DeviceB] ip pool pool2 bas local [*DeviceB-ip-pool-pool2] gateway 10.82.1.1 255.255.255.0 [*DeviceB-ip-pool-pool2] commit [~DeviceB-ip-pool-pool2] section 0 10.82.1.2 10.82.1.200 [~DeviceB-ip-pool-pool2] dns-server 192.168.8.252 [*DeviceB-ip-pool-pool2] commit [~DeviceB-ip-pool-pool2] vpn-instance vpn1 [~DeviceB-ip-pool-pool2] quit
# Configure a domain.
[~DeviceB] aaa [~DeviceB-aaa] domain fastweb [*DeviceB-aaa-domain-fastweb] commit [~DeviceB-aaa-domain-fastweb] authentication-scheme auth2 [*DeviceB-aaa-domain-fastweb] accounting-scheme acct2 [*DeviceB-aaa-domain-fastweb] commit [~DeviceB-aaa-domain-fastweb] ip-pool pool2 [~DeviceB-aaa-domain-fastweb] quit
Configure BAS access on an interface.
# Configure the user template names of users and the name of the template used to determine the user password generation mode.
[~DeviceB-aaa] default-user-name template fastweb include ip-address . [*DeviceB-aaa] commit [~DeviceB-aaa] default-password template fastweb cipher huawei_123 [~DeviceB-aaa] quit
# Configure the interface through which BAS users go online.
[~DeviceB] interface Virtual-Ethernet1/0/1 [*DeviceB-Virtual-Ethernet1/0/1] ve-group 1 l3-access [*DeviceB-Virtual-Ethernet1/0/1] quit [*DeviceB] interface Virtual-Ethernet1/0/1.100 [*DeviceB-Virtual-Ethernet1/0/1.100] vlan-type dot1q 100 [*DeviceB-Virtual-Ethernet1/0/0.100] ip binding vpn-instance access [*DeviceB-Virtual-Ethernet1/0/1.100] ip address 192.168.112.2 255.255.255.0 [*DeviceB-Virtual-Ethernet1/0/1.100] commit [~DeviceB-Virtual-Ethernet1/0/1.100] bas [~DeviceB-Virtual-Ethernet1/0/1.100-bas] access-type layer3-subscriber default-domain authentication fastweb [*DeviceB-Virtual-Ethernet1/0/1.100-bas] default-user-name-template fastweb [*DeviceB-Virtual-Ethernet1/0/1.100-bas] commit [~DeviceB-Virtual-Ethernet1/0/1.100-bas] default-password-template fastweb [~DeviceB-Virtual-Ethernet1/0/1.100-bas] quit [~DeviceB-Virtual-Ethernet1/0/1.100] quit
# Configure a backup interface for BAS users to go online.
[~DeviceB] interface Virtual-Ethernet2/0/1 [*DeviceB-Virtual-Ethernet2/0/1] ve-group 2 l3-access [*DeviceB-Virtual-Ethernet2/0/1] quit [*DeviceB] interface Virtual-Ethernet2/0/1.100 [*DeviceB-Virtual-Ethernet2/0/1.100] vlan-type dot1q 100 [*DeviceB-Virtual-Ethernet2/0/0.100] ip binding vpn-instance access [*DeviceB-Virtual-Ethernet2/0/1.100] ip address 192.168.223.2 255.255.255.0 [*DeviceB-Virtual-Ethernet2/0/1.100] commit [~DeviceB-Virtual-Ethernet2/0/1.100] bas [*DeviceB-Virtual-Ethernet1/0/1.100-bas] default-user-name-template fastweb [*DeviceB-Virtual-Ethernet1/0/1.100-bas] commit [~DeviceB-Virtual-Ethernet1/0/1.100-bas] default-password-template fastweb [~DeviceB-Virtual-Ethernet1/0/1.100-bas] quit [~DeviceB-Virtual-Ethernet1/0/1.100] quit
Configure a Layer 3 static user.
[~DeviceB] layer3-subscriber 192.168.1.1 vpn-instance access domain-name fastweb
Configuration Files
Device B configuration file
# sysname DeviceB # ip vpn-instance access ipv4-family route-distinguisher 200:1 apply-label per-instance vpn-target 111:1 export-extcommunity vpn-target 111:1 import-extcommunity # radius-server group rd2 radius-server shared-key-cipher %^%#clY:%[]x='-RMNJus[s/VJ:3YBq3<..|.{'xgbp+%^%# radius-server authentication 192.168.8.249 1812 weight 0 radius-server accounting 192.168.8.249 1813 weight 0 # ip pool pool2 bas local vpn-instance vpn1 gateway 10.82.1.1 255.255.255.0 section 0 10.82.1.2 10.82.1.200 dns-server 192.168.8.252 # acl number 3000 rule permit source 192.168.1.1 255.255.255.255 # traffic classifier class1 operator or if-match acl 3000 precedence 8 # traffic behavior behavior1 redirect ipv4-multinhp nhp 192.168.112.2 vpn access nhp 192.168.223.2 vpn access non-revertive # traffic policy loadbalance share-mode classifier class1 behavior behavior1 precedence 1 # aaa default-password template fastweb cipher %^%#:d"1K5>aICqP6}.%)!#0IngT9sGU-B%6]>H7Ylj%%^%# default-user-name template fastweb include ip-address . # authentication-scheme auth2 # accounting-scheme acct2 # domain fastweb authentication-scheme auth2 accounting-scheme acct2 ip-pool pool2 # interface GigabitEthernet1/0/3 undo shutdown # interface GigabitEthernet1/0/3.100 vlan-type dot1q 100 ip binding vpn-instance access ip address 192.168.111.1 255.255.255.0 traffic-policy loadbalance inbound ospf enable 100 area 0.0.0.0 # interface GigabitEthernet2/2/7 undo shutdown # interface GigabitEthernet2/2/7.100 vlan-type dot1q 100 ip binding vpn-instance access ip address 192.168.222.1 255.255.255.0 traffic-policy loadbalance inbound ospf enable 100 area 0.0.0.0 # interface Virtual-Ethernet1/0/0 ve-group 1 l3-terminate # interface Virtual-Ethernet1/0/0.100 vlan-type dot1q 100 ip address 192.168.112.1 255.255.255.0 # interface Virtual-Ethernet1/0/1 ve-group 1 l3-access # interface Virtual-Ethernet1/0/1.100 vlan-type dot1q 100 ip binding vpn-instance access ip address 192.168.112.2 255.255.255.0 bas # access-type layer3-subscriber default-domain authentication fastweb default-user-name-template fastweb default-password-template fastweb # # interface Virtual-Ethernet2/0/0 ve-group 2 l3-terminate # interface Virtual-Ethernet2/0/0.100 vlan-type dot1q 100 ip address 192.168.223.1 255.255.255.0 # interface Virtual-Ethernet2/0/1 ve-group 2 l3-access # interface Virtual-Ethernet2/0/1.100 vlan-type dot1q 100 ip binding vpn-instance access ip address 192.168.223.2 255.255.255.0 bas # access-type layer3-subscriber default-domain pre-authentication fastweb default-user-name-template fastweb default-password-template fastweb # # ospf 100 area 0.0.0.0 # layer3-subscriber 192.168.1.1 192.168.1.1 vpn-instance access domain-name fastweb # return