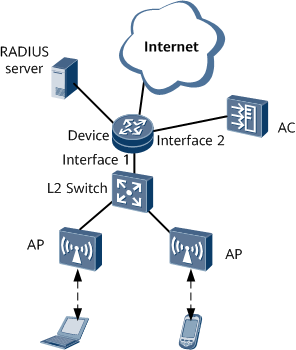
Example for Configuring WLAN User Access Based on RADIUS Proxy Authentication
This section provides an example for configuring WLAN user access based on RADIUS proxy authentication.
Networking Requirements
- A WLAN user sends an EAP packet to the AC. The AC terminates the EAP packet and sends a RADIUS packet to the router.
- The router functions as a RADIUS proxy. The router listens to authentication packets sent from the AC to the RADIUS server and forwards them to the RADIUS server, and listens to authentication response packets sent by the RADIUS server and forwards them to the AC. In the proxy process, the router saves the authorization information delivered by the RADIUS server to the user account.
- After the authentication is successful, the user sends DHCP messages to the router to obtain an IP address. The router queries the authorization information saved for the user account in the proxy process based on the user's MAC address. If the user account's authorization information exists, the router assigns an idle IP address to the user and uses the saved authorization information to authorize the user. In addition, the router sends an Accounting Start packet to the RADIUS server for user accounting.
- The router directly responds to accounting packets sent by the AC without sending them to the RADIUS server.
Configuration Roadmap
The configuration roadmap is as follows:
- Configure a RADIUS server group, an authentication scheme, an accounting scheme, and an address pool.
- Bind the RADIUS server group, authentication scheme, accounting scheme, and address pool to the domain.
- Configure RADIUS proxy.
- Configure BAS access on an interface.
- Configure an IP address for AC access on an interface.

By default, the router can listen to RADIUS packets through ports 1812, 1813, 1645, 1646, and 3799. To use another port to listen to RADIUS packets, run the radius-server extended-source-ports port-number port-number command in the system view to specify a listening port.
Data Preparation
To complete the configuration, you need the following data:
- IP address of the RADIUS authentication server
- IP address of the RADIUS accounting server
- Interface IP address for the AC to send RADIUS packets
Procedure
- Configure a RADIUS server group, an authentication scheme, an accounting scheme, and an address pool.
# Configure a RADIUS server group named shiva.
<HUAWEI> system-view [~HUAWEI] radius-server group shiva [*HUAWEI-radius-shiva] radius-server authentication 10.1.123.151 1812 [*HUAWEI-radius-shiva] radius-server accounting 10.1.123.151 1813 [*HUAWEI-radius-shiva] commit [~HUAWEI-radius-shiva] quit
# Configure a local IP address pool named a.
[~HUAWEI] ip pool a bas local [*HUAWEI-ip-pool-a] gateway 172.30.0.1 24 [*HUAWEI-ip-pool-a] commit [~HUAWEI-ip-pool-a] section 0 172.30.0.2 172.30.0.254 [~HUAWEI-ip-pool-a] quit
# Configure an authentication scheme named rdp, with RADIUS proxy authentication specified.
[~HUAWEI] aaa [~HUAWEI-aaa] authentication-scheme rdp [*HUAWEI-aaa-authen-rdp] authentication-mode radius-proxy [*HUAWEI-aaa-authen-rdp] commit [~HUAWEI-aaa-authen-rdp] quit
# Configure an accounting scheme named rds, with RADIUS accounting specified.
[~HUAWEI-aaa] accounting-scheme rds [*HUAWEI-aaa-accounting-rds] accounting-mode radius [*HUAWEI-aaa-accounting-rds] commit [~HUAWEI-aaa-accounting-rds] quit
- Configure a domain named radiusproxy, and bind the authentication scheme rdp, accounting scheme rds, and RADIUS server group shiva to the domain.
[~HUAWEI-aaa] domain radiusproxy [*HUAWEI-aaa-domain-radiusproxy] authentication-scheme rdp [*HUAWEI-aaa-domain-radiusproxy] accounting-scheme rds [*HUAWEI-aaa-domain-radiusproxy] radius-server group shiva [*HUAWEI-aaa-domain-radiusproxy] commit [~HUAWEI-aaa-domain-radiusproxy] ip-pool a [~HUAWEI-aaa-domain-radiusproxy] quit [~HUAWEI-aaa] quit
- Configure RADIUS proxy.
[~HUAWEI] radius-client 10.1.0.201 server-group shiva shared-key-cipher it-is-my-secret1 [*HUAWEI] commit

The IP address configured after radius-client is the interface IP address for the AC to send RADIUS packets. In this example, the RADIUS server group bound to the domain is the same as that for RADIUS proxy. In practice, the RADIUS server group bound to a domain may be different from that for RADIUS proxy.
- Configure an IP address for AC access.
[~HUAWEI] interface gigabitethernet 0/1/2 [*HUAWEI-GigabitEthernet0/1/2] ip address 10.1.0.197 8 [*HUAWEI-GigabitEthernet0/1/2] commit [~HUAWEI-GigabitEthernet0/1/2] quit

This IP address is used for AC access. RADIUS authentication packets sent by the AC must be sent to this address. If the router has another IP address connected to the AC, you may not configure the IP address.
- Configure BAS access on an interface.

The BAS access configuration on an interface in RADIUS proxy scenarios is the same as that in IPoE access scenarios. RADIUS proxy applies only to IPoE users, not PPPoE users.
- Verify the configuration.
Run the display radius-server configuration group shiva command on the router to view RADIUS server group configurations.
[~HUAWEI] display radius-server configuration group shiva ------------------------------------------------------- Server-group-name : shiva Authentication-server: IP:10.1.123.151 Port:1812 Weight[0] [UP] Vpn: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Accounting-server : IP:10.1.123.151 Port:1813 Weight[0] [UP] Vpn: - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Protocol-version : radius Shared-secret-key : ****** Retransmission : 3 Timeout-interval(s) : 5 Acct-Stop-Packet Resend : NO Acct-Stop-Packet Resend-Times : 0 Traffic-unit : B ClassAsCar : NO User-name-format : Domain-included Option82 parse mode : - Attribute-translation: NO Packet send algorithm: Master-Backup Tunnel password : cipher
Run the display domain command on the router to view domain configurations.
[~HUAWEI] display domain radiusproxy ------------------------------------------------------------------------------ Domain-name : radiusproxy Domain-state : Active Authentication-scheme-name : rdp Accounting-scheme-name : rds Authorization-scheme-name : - Primary-DNS-IP-address : - Second-DNS-IP-address : - Primary-DNS-IPV6-address : - Second-DNS-IPV6-address : - Web-server-URL-parameter : No Portal-server-URL-parameter : No Primary-NBNS-IP-address : - Second-NBNS-IP-address : - Time-range : Disable Idle-cut direction : Both Idle-data-attribute (time,flow) : 0, 60 User detect interval : 0s User detect retransmit times : 0 Install-BOD-Count : 0 Report-VSM-User-Count : 0 Value-added-service : default User-access-limit : 283648 Online-number : 0 Web-IP-address : - Web-URL : - Web-auth-server : - Web-auth-state : - Web-server-mode : get Slave Web-IP-address : - Slave Web-URL : - Slave Web-auth-server : - Slave Web-auth-state : - Portal-server-IP : - Portal-URL : - Portal-force-times : 2 Service-policy(Portal) : - PPPoE-user-URL : Disable AdminUser-priority : 16 IPUser-ReAuth-Time : 300s mscg-name-portal-key : - Portal-user-first-url-key : - User-session-limit : 4294967295 Ancp auto qos adapt : Disable L2TP-group-name : - User-lease-time-no-response : 0s RADIUS-server-template : shiva Two-acct-template : - RADIUS-server-pre-template : - - - HWTACACS-server-template : - Bill Flow : Disable Tunnel-acct-2867 : Disable Qos-profile-name inbound : - Qos-profile-name outbound : - Flow Statistic: Flow-Statistic-Up : Yes Flow-Statistic-Down : Yes Source-IP-route : Disable IP-warning-threshold : - IP-warning-threshold(Low) : - IPv6-warning-threshold : - IPv6-warning-threshold(Low) : - Multicast Forwarding : Yes Multicast Virtual : No Max-multilist num : 4 Multicast-profile : - Multicast-profile ipv6 : - IP-address-pool-name : a Quota-out : Offline Service-type : - User-basic-service-ip-type : -/-/- PPP-ipv6-address-protocol : Ndra IPv6-information-protocol : Stateless dhcpv6 IPv6-PPP-assign-interfaceid : Disable IPv6-PPP-NDRA-halt : Disable IPv6-PPP-NDRA-unicast : Disable Trigger-packet-wait-delay : 60s Peer-backup : Enable Reallocate-ip-address : Disable Cui enable : Disable Igmp enable : Enable L2tp-user radius-force : Disable Accounting dual-stack : Separate Radius server domain-annex : - Dhcp-option64-service : Disable Parse-separator : - Parse-segment-value : - Dhcp-receive-server-packet : - Http-hostcar : Disable Public-address assign-first : Disable Public-address nat : Enable Dhcp-user auto-save : Disable IP-pool usage-status threshold : 255 , 255 Select-Pool-Rule : gateway + local priority AFTR name : - Traffic-rate-mode : Separate Traffic-statistic-mode : Separate Rate-limit-mode-inbound : Car Rate-limit-mode-outbound : Car Service-change-mode : Stop-start DAA Direction : both ------------------------------------------------------------------------------
Run the display radius-client configuration command on the router to view RADIUS proxy configurations.
[~HUAWEI] display radius-client configuration Radius-client packet dscp value: 7 ----------------------------------------------------------------------------- IP-Address Mask VPN-instance Group Domain-authorization Roam-domain Trigger-web ----------------------------------------------------------------------------- 10.1.0.201 255.255.255.255 -- shiva NO -- ACCT_TRIGGER ----------------------------------------------------------------------------- 1 Radius client(s) in total
Configuration Files
# sysname HUAWEI # radius-server group shiva radius-server authentication 10.1.123.151 1812 weight 0 radius-server accounting 10.1.123.151 1813 weight 0 # ip pool a bas local gateway 172.30.0.1 255.255.255.0 section 0 172.30.0.2 172.30.0.254 # aaa # authentication-scheme rdp authentication-mode radius-proxy # accounting-scheme rds # domain radiusproxy authentication-scheme rdp accounting-scheme rds radius-server group shiva ip-pool a # radius-client 10.1.0.201 mask 255.255.255.255 shared-key-cipher %^%#}v{/ZA}>yTiC'[0bvy'X"N[+,uj*U)L0^5;4Jtf6%^%# server-group shiva # interface GigabitEthernet 0/1/1 undo shutdown bas # access-type layer2-subscriber default-domain authentication radiusproxy authentication-method bind # # interface GigabitEthernet 0/1/2 undo shutdown ip address 10.1.0.197 255.0.0.0 # return