Example for Configuring Layer 3 DHCPv6 to Support IANA+IAPD Access (Web Authentication)
This section provides an example for configuring Layer 3 DHCPv6 to support IANA+IAPD access.
Networking Requirements
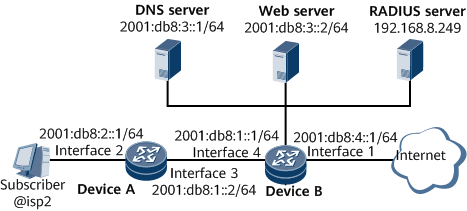
On the network shown in Figure 1, the networking requirements are as follows:
A user belongs to the domain isp2 and connects to GE 0/1/2.1 on Device B through Device A, a DHCPv6 relay agent, in DHCPv6 (IANA+IAPD) mode.
The user adopts web authentication, Remote Authentication Dial In User Service (RADIUS) authentication, and RADIUS accounting.
The IP address of the RADIUS server is 192.168.8.249. The authentication port number is 1812, and the accounting port number is 1813. The standard RADIUS protocol is used, and the key is it-is-my-secret1.
The IP address of the DNS server is 2001:db8:3::1/64.
The IP address of the web server is 2001:db8:3::2/64. The shared key is webvlan.
Configuration Roadmap
All functions are configured on Device B except the DHCPv6 relay function. The configuration roadmap is as follows:
- Configure IPv6 addresses for interfaces on Device A and Device B.
Configure DHCPv6 relay on Device A.
- Configure network-side address pools on Device B. The gateway address of the address pools must be on the same network segment as the IPv6 address of the inbound interface on Device A, the DHCP relay agent.
Configure AAA schemes.
- Configure an IP address used by the Device B to receive portal packets from the web authentication server.
- Configure a web server.
Configure a RADIUS server group.
- Configure an ACL to allow the user to access only the web server address before web authentication succeeds.
- Configure the DUID of the BRAS.
Configure a domain.
Configure a BAS interface and a downstream interface.
Data Preparation
To complete the configuration, you need the following data:
Authentication template name and authentication mode
Accounting template name and accounting mode
RADIUS server group name as well as IP addresses and port numbers of the RADIUS authentication server and accounting server
Address pool names
Domain name
BAS interface parameters
Procedure
- Configure IPv6 addresses for interfaces on Device A and Device B.
# Configure Device A.
<HUAWEI> system-view [~HUAWEI] sysname DeviceA [*HUAWEI] commit [~DeviceA] interface GigabitEthernet1/0/2 [~DeviceA-GigabitEthernet1/0/2] ipv6 enable [*DeviceA-GigabitEthernet1/0/2] ipv6 address 2001:db8:2::1/64 [*DeviceA-GigabitEthernet1/0/2] ipv6 address auto link-local [*DeviceA-GigabitEthernet1/0/2] commit [~DeviceA-GigabitEthernet1/0/2] quit [~DeviceA] interface GigabitEthernet1/0/1.1 [*DeviceA-GigabitEthernet1/0/1.1] ipv6 enable [*DeviceA-GigabitEthernet1/0/1.1] ipv6 address 2001:db8:1::2/64 [*DeviceA-GigabitEthernet1/0/1.1] vlan-type dot1q 1 [*DeviceA-GigabitEthernet1/0/1.1] ipv6 address auto link-local [*DeviceA-GigabitEthernet1/0/1.1] commit [~DeviceA-GigabitEthernet1/0/1.1] quit
# Configure Device B.
<HUAWEI> system-view [~HUAWEI] sysname DeviceB [*HUAWEI] commit [~DeviceB] interface GigabitEthernet1/0/2.1 [*DeviceB-GigabitEthernet1/0/2.1] ipv6 enable [*DeviceB-GigabitEthernet1/0/2.1] ipv6 address 2001:db8:1::1/64 [*DeviceB-GigabitEthernet1/0/2.1] vlan-type dot1q 1 [*DeviceB-GigabitEthernet1/0/2.1] commit [~DeviceB-GigabitEthernet1/0/2.1] quit
- Configure DHCPv6 relay on Device A.
[~DeviceA] interface GigabitEthernet1/0/2 [~DeviceA-GigabitEthernet1/0/2] dhcp select relay [*DeviceA-GigabitEthernet1/0/2] dhcpv6 relay destination 2001:db8:1::1 [*DeviceA-GigabitEthernet1/0/2] ipv6 address auto link-local [*DeviceA-GigabitEthernet1/0/2] commit [~DeviceA-GigabitEthernet1/0/2] quit
- Configure network-side address pools on Device B. The gateway address of the address pools must be on the same network segment as the IPv6 address of the inbound interface on Device A, the DHCP relay agent.
# Configure an IAPD prefix pool.
[~DeviceB] ipv6 prefix prefixpd delegation [*DeviceB-ipv6-prefix-prefixpd] prefix 2001:db8:3::/48 [*DeviceB-ipv6-prefix-prefixpd] commit [~DeviceB-ipv6-prefix-prefixpd] quit
# Configure an IAPD address pool.
[~DeviceB] ipv6 pool poolpd bas delegation [*DeviceB-ipv6-pool-poolpd] prefix prefixpd [*DeviceB-ipv6-pool-poolpd] dns-server 2001:db8:3::1 [*DeviceB-ipv6-pool-poolpd] commit [~DeviceB-ipv6-pool-poolpd] quit
# Configure an IANA prefix pool.
[~DeviceB] ipv6 prefix na local [*DeviceB-ipv6-prefix-na] prefix 2001:db8:2::/64 [*DeviceB-ipv6-prefix-na] commit [~DeviceB-ipv6-prefix-na] quit
# Configure an IANA relay address pool.
[~DeviceB] ipv6 pool na bas relay [*DeviceB-ipv6-prefix-na] prefix na [*DeviceB-ipv6-prefix-na] dns-server 2001:db8:3::1 [*DeviceB-ipv6-prefix-na] commit [~DeviceB-ipv6-prefix-na] quit
- Configure AAA schemes.
# Configure an authentication scheme.
[~DeviceB] aaa [~DeviceB-aaa] authentication-scheme auth2 [*DeviceB-aaa-authen-auth2] authentication-mode radius [*DeviceB-aaa-authen-auth2] commit [~DeviceB-aaa-authen-auth2] quit
# Configure an accounting scheme.
[~DeviceB-aaa] accounting-scheme acct2 [*DeviceB-aaa-accounting-acct2] accounting-mode radius [*DeviceB-aaa-accounting-acct2] commit [~DeviceB-aaa-accounting-acct2] quit [~DeviceB-aaa] quit
- Configure an IP address used by the Device B to receive portal packets from the web authentication server.
[~DeviceB] interface LoopBack 0 [*DeviceB-LoopBack0] ipv6 enable [*DeviceB-LoopBack0] ipv6 address 2001:db8:3::3 128 [*DeviceB-LoopBack0] ipv6 address auto link-local [*DeviceB-LoopBack0] commit [~DeviceB-LoopBack0] quit [~DeviceB] web-auth-server source-ipv6 2001:db8:1::3
- Configure a web server.
[~DeviceB] web-auth-server enable [~DeviceB] web-auth-server source interface LoopBack 0 [~DeviceB] web-auth-server 2001:db8:3::3 key cipher Root@123
- Configure a RADIUS server group.
[~DeviceB] radius-server group rd2 [*DeviceB-radius-rd2] radius-server authentication 192.168.8.249 1812 [*DeviceB-radius-rd2] radius-server accounting 192.168.8.249 1813 [*DeviceB-radius-rd2] commit [~DeviceB-radius-rd2] radius-server type standard [~DeviceB-radius-rd2] radius-server shared-key-cipher it-is-my-secret1 [*DeviceB-radius-rd2] commit [~DeviceB-radius-rd2] quit
- Configure an ACL to allow the user to access only the web server address before web authentication succeeds.
# Configure a user group.
[~Device] user-group huawei
# Configure ACL numbered 6000 and create ACL rules to match traffic between the user group huawei and the web authentication and DNS server, so that the traffic can pass through.
[~DeviceB] acl ipv6 number 6000 [*Device-acl6-ucl-6000] rule permit ipv6 source user-group huawei destination ipv6-address 2001:db8:3::2/128 [*DeviceB-acl6-ucl-6000] rule permit ipv6 source ipv6-address 2001:db8:3::2/128 destination user-group huawei [*DeviceB-acl6-ucl-6000] rule permit ipv6 source user-group huawei destination ipv6-address 2001:db8:3::1/128 [*DeviceB-acl6-ucl-6000] rule permit ipv6 source ipv6-address 2001:db8:3::1/128 destination user-group huawei [*DeviceB-acl6-ucl-6000] commit [~DeviceB-acl6-ucl-6000] quit
# Configure ACL numbered 6001 and create ACL rules to match TCP packets from the user group huawei and with a destination port of www or 8080, so that the packets can be redirected to a web authentication server address.
[~DeviceB] acl ipv6 number 6001 [*DeviceB-acl6-ucl-6001] rule permit tcp source user-group huawei destination-port eq www [*DeviceB-acl6-ucl-6001] rule permit tcp source user-group huawei destination-port eq 8080 [*DeviceB-acl6-ucl-6001] commit [~DeviceB-acl6-ucl-6001] quit
# Configure ACL numbered 6002 and create ACL rules to match all traffic from the user group huawei, so that the traffic can be denied access to the network.
[~DeviceB] acl ipv6 number 6002 [*DeviceB-acl6-ucl-6002] rule permit ipv6 source ipv6-address any destination user-group huawei [*DeviceB-acl6-ucl-6002] rule deny ipv6 source user-group huawei destination ipv6-address any [*DeviceB-acl6-ucl-6002] commit [~DeviceB-acl6-ucl-6002] quit
# Configure a traffic classifier.
[~DeviceB] traffic classifier c1 [*DeviceB-classifier-c1] if-match ipv6 acl 6000 [*DeviceB-classifier-c1] commit [~DeviceB-classifier-c1] quit [~DeviceB] traffic classifier c2 [*DeviceB-classifier-c2] if-match ipv6 acl 6001 [*DeviceB-classifier-c2] commit [~DeviceB-classifier-c2] quit [~DeviceB] traffic classifier c3 [*DeviceB-classifier-c3] if-match ipv6 acl 6002 [*DeviceB-classifier-c3] commit [~DeviceB-classifier-c3] quit
# Configure a traffic behavior.
[~DeviceB] traffic behavior b1 [*DeviceB-behavior-b1] permit [*DeviceB-behavior-b1] commit [~DeviceB-behavior-b1] quit [~DeviceB] traffic behavior b2 [*DeviceB-behavior-b2] http-redirect [*DeviceB-behavior-b2] commit [~DeviceB-behavior-b2] quit [~DeviceB] traffic behavior b3 [*DeviceB-behavior-b3] deny [*DeviceB-behavior-b3] commit
# Configure a traffic policy.
[~DeviceB] traffic policy policy [*DeviceB-trafficpolicy-policy] classifier c1 behavior b1 [*DeviceB-trafficpolicy-policy] classifier c2 behavior b2 [*DeviceB-trafficpolicy-policy] classifier c3 behavior b3 [*DeviceB-trafficpolicy-policy] commit [~DeviceB-trafficpolicy-policy] quit
# Apply the traffic policy globally.
[~DeviceB] traffic-policy policy inbound
- Configure the DUID of the BRAS.
[~DeviceB] dhcpv6 duid 12345678 [*DeviceB] commit
- Configure a domain.
# Configure a pre-authentication domain named domain1.
[~DeviceB] aaa [~DeviceB-aaa] domain domain1 [*DeviceB-aaa-domain-domain1] authentication-scheme none [*DeviceB-aaa-domain-domain1] accounting-scheme none [*DeviceB-aaa-domain-domain1] commit [~DeviceB-aaa-domain-domain1] prefix-assign-mode unshared [~DeviceB-aaa-domain-domain1] user-group huawei [~DeviceB-aaa-domain-domain1] ipv6-pool poolpd [~DeviceB-aaa-domain-domain1] ipv6-pool na [~DeviceB-aaa-domain-domain1] web-server 2001:db8:3::2 [~DeviceB-aaa-domain-domain1] web-server url http://www.isp1.com [~DeviceB-aaa-domain-domain1] web-server identical-url [~DeviceB-aaa-domain-domain1] quit
# Configure an authentication domain named isp2.
[~DeviceB] aaa [~DeviceB-aaa] domain isp2 [*DeviceB-aaa-domain-isp2] authentication-scheme auth2 [*DeviceB-aaa-domain-isp2] accounting-scheme acct2 [*DeviceB-aaa-domain-isp2] radius-server group rd2 [*DeviceB-aaa-domain-isp2] commit [~DeviceB-aaa-domain-isp2] quit [~DeviceB-aaa] quit
- Configure interfaces.
# Configure a BAS interface.
[~DeviceB] interface GigabitEthernet 1/0/2.1 [~DeviceB-GigabitEthernet1/0/2.1] ipv6 address auto link-local [*DeviceB-GigabitEthernet1/0/2.1] ipv6 nd autoconfig managed-address-flag [*DeviceB-GigabitEthernet1/0/2.1] commit [~DeviceB-GigabitEthernet1/0/2.1] bas [~DeviceB-GigabitEthernet1/0/2.1-bas] access-type layer3-subscriber default-domain pre-authentication isp2 authentication isp2 [*DeviceB-GigabitEthernet1/0/2.1-bas] commit [~DeviceB-GigabitEthernet1/0/2.1-bas] quit [~DeviceB-GigabitEthernet1/0/2.1] quit
# Configure an uplink interface connected to the Internet.
[~DeviceB] interface GigabitEthernet 1/0/1 [~DeviceB-GigabitEthernet1/0/1] ipv6 enable [*DeviceB-GigabitEthernet1/0/1] ipv6 address 2001:db8:4::1/64 [*DeviceB-GigabitEthernet1/0/1] ipv6 address auto link-local [*DeviceB-GigabitEthernet1/0/1] commit [~DeviceB-GigabitEthernet1/0/1] quit
Configuration File
- Device A configuration file
# sysname DeviceA # interface GigabitEthernet1/0/1.1 vlan-type dot1q 1 ipv6 enable ipv6 address 2001:DB8:1::2/64 ipv6 address auto link-local # interface GigabitEthernet1/0/2 undo shutdown ipv6 enable ipv6 address 2001:DB8:2::1/64 dhcp select relay ipv6 address auto link-local dhcpv6 relay destination 2001:DB8:1::1 # return - Device B configuration file
# sysname DeviceB # radius-server group rd2 radius-server shared-key-cipher %^%#clY:%[]x='-RMNJus[s/VJ:3YBq3<..|.{'xgbp+%^%# radius-server authentication 192.168.8.249 1812 weight 0 radius-server accounting 192.168.8.249 1813 weight 0 # ipv6 prefix prefixpd delegation prefix 2001:DB8:3::/48 # ipv6 prefix na local prefix 2001:DB8:2::/64 # ipv6 pool na bas relay dns-server 2001:DB8:3::1 prefix na # ipv6 pool poolpd bas delegation dns-server 2001:DB8:3::1 prefix prefixpd # user-group huawei # acl ipv6 number 6000 rule 5 permit ipv6 source user-group huawei destination ipv6-address 2001:DB8:3::2/128 rule 10 permit ipv6 source ipv6-address 2001:DB8:3::2/128 destination user-group huawei rule 15 permit ipv6 source user-group huawei destination ipv6-address 2001:DB8:3::1/128 rule 20 permit ipv6 source ipv6-address 2001:DB8:3::1/128 destination user-group huawei # acl ipv6 number 6001 rule 5 permit tcp source user-group huawei destination-port eq www rule 10 permit tcp source user-group huawei destination-port eq 8080 # acl ipv6 number 6002 rule 5 permit ipv6 source ipv6-address any destination user-group huawei rule 10 deny ipv6 source user-group huawei destination ipv6-address any # dhcpv6 duid 12345678 # traffic classifier c1 operator or if-match ipv6 acl 6000 precedence 21 # traffic classifier c2 operator or if-match ipv6 acl 6001 precedence 23 # traffic classifier c3 operator or if-match ipv6 acl 6002 precedence 25 # traffic behavior b1 # traffic behavior b2 http-redirect # traffic behavior b3 deny # traffic policy policy share-mode classifier c1 behavior b1 precedence 1 classifier c2 behavior b2 precedence 2 classifier c3 behavior b3 precedence 3 # aaa # authentication-scheme default0 # authentication-scheme default1 # authentication-scheme default authentication-mode local radius # authentication-scheme auth2 # authorization-scheme default # accounting-scheme default0 # accounting-scheme default1 # accounting-scheme acct2 # domain default0 # domain default1 # domain default_admin # domain isp2 authentication-scheme auth2 accounting-scheme acct2 radius-server group rd2 ipv6-pool poolpd # interface GigabitEthernet1/0/1 undo shutdown ipv6 enable ipv6 address 2001:DB8:4::1/64 ipv6 address auto link-local dcn # interface GigabitEthernet1/0/2 undo shutdown # interface GigabitEthernet1/0/2.1 vlan-type dot1q 1 ipv6 enable ipv6 address 2001:DB8:1::1/64 ipv6 nd autoconfig managed-address-flag bas # access-type layer3-subscriber default-domain pre-authentication isp2 authentication isp2 # # interface LoopBack0 ipv6 enable ipv6 address 2001:DB8:3::3/128 ipv6 address auto link-local # web-auth-server enable web-auth-server source interface LoopBack0 web-auth-server 2001:DB8:3::2 port 50100 key cipher %^%#\39J9tmKl#+;)]1yEd@V#i(1Jeq"vO=9ka=-\qN<%^%# # undo web-auth-server source-ip all # undo web-auth-server source-ipv6 all web-auth-server source-ipv6 2001:DB8:3::3 # return