IPsec applies only to IPv4 unicast packets. To cover IPv6 unicast, IPv4 multicast, IPv4 broadcast, and L2VPN/L3VPN IPv4 packets, configure IPv6 over GRE over IPsec.
Networking Requirements
Figure 1 shows the networking diagram.
Figure 1 Networking of IPv6 over GRE over IPsec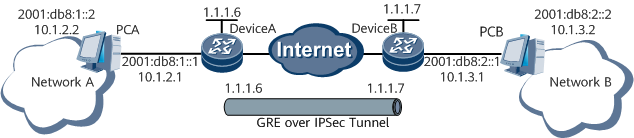
Network A is connected to Device A through GE 0/1/17.
Network B is connected to Device B through GE 0/1/2.
The IPv4 and IPv6 addresses of Device A are 10.1.2.1 and 2001:db8:1::1 respectively. The IPsec service board and tunnel service board of Device A are installed in slot 1 and slot 1 respectively.
The IPv4 and IPv6 addresses of Device B are 10.1.3.1 and 2001:db8:2::1 respectively. The IPsec service board and tunnel service board of Device B are installed in slot 1 and slot 1 respectively.
Device A and Device B are routable.
IPv4 unicast, IPv6 unicast, IPv4 multicast, IPv4 broadcast, L2VPN/L3VPN IPv4 packets must be encrypted before being sent between PCA and PCB.
Configuration Roadmap
The configuration roadmap is as follows:
Assign an IP address to each interface.
Create a loopback interface and bind it to GRE.
Create a tunnel interface and configure GRE for the tunnel interface.
Configure an ACL rule.
Configure an IPsec proposal.
Configure an IKE proposal.
Configure IKE peers.
Configure an IPsec policy.
Configure the IPsec service instance group.
Create a tunnel interface and configure IPsec for the tunnel interface.
Configure a static route to the destination network.
Data Preparation
To complete the configuration, you need the following data:
- IP addresses of interfaces
- Tunnel mode, IP address, source address, and destination address for each tunnel interface
- IP address segments
- Pre-shared key
- Security protocol, encapsulation mode, encryption algorithm, and authentication algorithm that an IPsec proposal uses
- Encryption algorithm and authentication algorithm that an IKE proposal uses
Procedure
- Configure Device A.
- Allocate IP addresses to interfaces.
Configure an IP address for GE 0/1/18.10.
<DeviceA> system-view
[~DeviceA] interface GigabitEthernet 0/1/18.10
[*DeviceA-GigabitEthernet0/1/18.10] vlan-type dot1q 200
[*DeviceA-GigabitEthernet0/1/18.10] ip address 10.1.1.6 24
[*DeviceA-GigabitEthernet0/1/18.10] quit
[*DeviceA] commit
Configure an IP address for GE 0/1/17.
[~DeviceA] interface GigabitEthernet 0/1/17
[~DeviceA-GigabitEthernet0/1/17] ip address 10.1.2.1 24
[*DeviceA-GigabitEthernet0/1/17] ipv6 enable
[*DeviceA-GigabitEthernet0/1/17] ipv6 address 2001:db8:1::1/64
[*DeviceA-GigabitEthernet0/1/17] ipv6 neighbor 2001:db8:1::2 11-11-11
[*DeviceA-GigabitEthernet0/1/17] quit
[*DeviceA] commit
- Create a loopback interface and bind it to GRE.
[~DeviceA] interface loopback 111
[*DeviceA-Loopback111] ip address 1.1.1.6 32
[*DeviceA-Loopback111] binding tunnel gre
[*DeviceA-Loopback111] quit
[*DeviceA] commit
- Configure a GRE tunnel.
[~DeviceA] interface tunnel 200
[*DeviceA-tunnel200] tunnel-protocol gre
[*DeviceA-tunnel200] ip address 10.1.4.1 24
[*DeviceA-tunnel200] source loopback 111
[*DeviceA-tunnel200] destination 1.1.1.7
[*DeviceA-tunnel200] ipv6 enable
[*DeviceA-tunnel200] ipv6 address 2001:db8:3::1/64
[*DeviceA-tunnel200] quit
[*DeviceA] commit
- Configure an ACL rule.
[~DeviceA] acl 3018
[*DeviceA-acl4-advance-3018] rule permit gre source 1.1.1.6 0 destination 1.1.1.7 0
[*DeviceA-acl4-advance-3018] quit
[*DeviceA] commit
- Configure an IPsec proposal named pro1.
[~DeviceA] ipsec proposal pro1
[*DeviceA-ipsec-proposal-pro1] encapsulation-mode tunnel
[*DeviceA-ipsec-proposal-pro1] transform esp
[*DeviceA-ipsec-proposal-pro1] esp authentication-algorithm sha2-256
[*DeviceA-ipsec-proposal-pro1] esp encryption-algorithm aes 256
[*DeviceA-ipsec-proposal-pro1] quit
[*DeviceA] commit
- Configure an IKE proposal numbered 1.
[~DeviceA] ike proposal 1
[*DeviceA-ike-proposal-1] authentication-method pre-share
[*DeviceA-ike-proposal-1] authentication-algorithm sha2-256
[*DeviceA-ike-proposal-1] dh group14
[*DeviceA-ike-proposal-1] quit
[*DeviceA] commit
- Configure an IKE peer named peer1.

- The setting of the pre-shared key should be identical with that on the peer device.
[~DeviceA] ike peer peer1
[*DeviceA-ike-peer-peer1] ike-proposal 1
[*DeviceA-ike-peer-peer1] remote-address 10.1.5.2
[*DeviceA-ike-peer-peer1] pre-shared-key 1234567890
[*DeviceA-ike-peer-peer1] quit
[*DeviceA] commit
- Configure IKE DPD.
[~DeviceA] ike dpd interval 10 10
[*DeviceA] commit
- Configure an IPsec policy named policy1 and numbered 1.
[~DeviceA] ipsec policy policy1 1 isakmp
[*DeviceA-ipsec-policy-isakmp-policy1-1] security acl 3018
[*DeviceA-ipsec-policy-isakmp-policy1-1] proposal pro1
[*DeviceA-ipsec-policy-isakmp-policy1-1] ike-peer peer1
[*DeviceA-ipsec-policy-isakmp-policy1-1] quit
[*DeviceA] commit
- Configure the IPsec service instance group.
[~DeviceA] service-location 1
[*DeviceA-service-location-1] location slot 1
[*DeviceA-service-location-1] commit
[~DeviceA-service-location-1] quit
[~DeviceA] service-instance-group group1
[*DeviceA-service-instance-group-group1] service-location 1
[*DeviceA-service-instance-group-group1] commit
[~DeviceA-service-instance-group-group1] quit
- Create a tunnel interface and configure IPsec for the tunnel interface.
[~DeviceA] interface Tunnel 1600
[*DeviceA-Tunnel1600] ip address 10.1.5.1 24
[*DeviceA-Tunnel1600] tunnel-protocol ipsec
[*DeviceA-Tunnel1600] ipsec policy policy1 service-instance-group group1
[*DeviceA-Tunnel1600] quit
[*DeviceA] commit
- Configure a static route to network B.
[~DeviceA] ip route-static 1.1.1.7 255.255.255.255 Tunnel1600 10.1.5.2
[*DeviceA] ip route-static 10.1.5.2 255.255.255.255 GigabitEthernet0/1/18.10 10.1.1.7
[*DeviceA] ip route-static 10.1.3.1 255.255.255.0 Tunnel200 1.1.1.7
[*DeviceA] ipv6 route-static 2001:db8:2::2 64 Tunnel200
[*DeviceA] commit
- Configure Device B.
- Allocate IP addresses to interfaces.
Configure an IP address for GE 0/1/1.10.
<DeviceB> system-view
[~DeviceB] interface GigabitEthernet0/1/1.10
[*DeviceB-GigabitEthernet0/1/1.10] vlan-type dot1q 200
[*DeviceB-GigabitEthernet0/1/1.10] ip address 10.1.1.7 24
[*DeviceB-GigabitEthernet0/1/1.10] quit
[*DeviceB] commit
Configure an IP address for GE 0/1/2.
[~DeviceB] interface GigabitEthernet 0/1/2
[*DeviceB-GigabitEthernet0/1/2] ip address 10.1.3.1 24
[*DeviceB-GigabitEthernet0/1/2] ipv6 enable
[*DeviceB-GigabitEthernet0/1/2] ipv6 address 2001:db8:2::1/64
[*DeviceB-GigabitEthernet0/1/2] ipv6 neighbor 2001:db8:2::2 22-22-22
[*DeviceB-GigabitEthernet0/1/2] quit
[*DeviceB] commit
- Create a loopback interface and bind it to GRE.
[~DeviceB] interface loopback 111
[*DeviceB-Loopback111] ip address 1.1.1.7 255.255.255.255
[*DeviceB-Loopback111] binding tunnel gre
[*DeviceB-Loopback111] quit
[*DeviceB] commit
- Configure a GRE tunnel.
[~DeviceB] interface tunnel 200
[*DeviceB-tunnel200] tunnel-protocol gre
[*DeviceB-tunnel200] ip address 10.1.4.2 255.255.255.0
[*DeviceB-tunnel200] ipv6 enable
[*DeviceB-tunnel200] ipv6 address 2001:db8:3::2/64
[*DeviceB-tunnel200] source LoopBack 111
[*DeviceB-tunnel200] destination 1.1.1.6
[*DeviceB-tunnel200] quit
[*DeviceB] commit
- Configure an ACL rule.
[~DeviceB] acl 3018
[*DeviceB-acl4-advance-3018] rule permit gre source 1.1.1.7 0 destination 1.1.1.6 0
[*DeviceB-acl4-advance-3018] quit
[*DeviceB] commit
- Configure an IPsec proposal named pro1.
[~DeviceB] ipsec proposal pro1
[*DeviceB-ipsec-proposal-pro1] encapsulation-mode tunnel
[*DeviceB-ipsec-proposal-pro1] transform esp
[*DeviceB-ipsec-proposal-pro1] esp authentication-algorithm sha2-256
[*DeviceB-ipsec-proposal-pro1] esp encryption-algorithm aes 256
[*DeviceB-ipsec-proposal-pro1] quit
[*DeviceB] commit
- Configure an IKE proposal numbered 1.
[~DeviceB] ike proposal 1
[*DeviceB-ike-proposal-1] authentication-method pre-share
[*DeviceB-ike-proposal-1] authentication-algorithm sha2-256
[*DeviceB-ike-proposal-1] dh group14
[*DeviceB-ike-proposal-1] quit
[*DeviceB] commit
- Configure an IKE peer named peer1.
[~DeviceB] ike peer peer1
[*DeviceB-ike-peer-peer1] ike-proposal 1
[*DeviceB-ike-peer-peer1] remote-address 10.1.5.1
[*DeviceB-ike-peer-peer1] pre-shared-key 1234567890
[*DeviceB-ike-peer-peer1] quit
[*DeviceB] commit
- Configure IKE DPD.
[~DeviceB] ike dpd interval 10 10
[*DeviceB] commit
- Configure an IPsec policy named policy1 and numbered 1.
[~DeviceB] ipsec policy policy1 1 isakmp
[*DeviceB-ipsec-policy-isakmp-policy1-1] security acl 3018
[*DeviceB-ipsec-policy-isakmp-policy1-1] proposal pro1
[*DeviceB-ipsec-policy-isakmp-policy1-1] ike-peer peer1
[*DeviceB-ipsec-policy-isakmp-policy1-1] quit
[*DeviceB] commit
- Configure the IPsec service instance group.
[~DeviceB] service-location 1
[*DeviceB-service-location-1] location slot 1
[*DeviceB-service-location-1] commit
[~DeviceB-service-location-1] quit
[~DeviceB] service-instance-group group1
[*DeviceB-service-instance-group-group1] service-location 1
[*DeviceB-service-instance-group-group1] commit
[~DeviceB-service-instance-group-group1] quit
- Create a tunnel interface and configure IPsec for the tunnel interface.
[~DeviceB] interface Tunnel 1600
[*DeviceB-Tunnel1600] ip address 10.1.5.2 24
[*DeviceB-Tunnel1600] tunnel-protocol ipsec
[*DeviceB-Tunnel1600] ipsec policy policy1 service-instance-group group1
[*DeviceB-Tunnel1600] quit
[*DeviceB] commit
- Configure a static route to network A.
[~DeviceB] ip route-static 10.1.2.1 255.255.255.0 Tunnel200 1.1.1.6
[*DeviceB] ip route-static 10.1.5.1 255.255.255.255 GigabitEthernet0/1/1.10 10.1.1.6
[*DeviceB] ip route-static 1.1.1.6 255.255.255.255 Tunnel1600 10.1.5.1
[*DeviceB] ipv6 route-static 2001:db8:1::2 64 Tunnel200
[*DeviceB] commit
Configuration Files
Device A configuration file
#
sysname DeviceA
#
ike dpd interval 10 10
#
service-location 1
location slot 1
#
service-instance-group group1
service-location 1
#
acl number 3018
rule 5 permit gre source 1.1.1.6 0 destination 1.1.1.7 0
#
ike proposal 1
encryption-algorithm aes-cbc 256
dh group14
authentication-algorithm sha2-256
integrity-algorithm hmac-sha2-256
#
ike peer peer1
pre-shared-key %$%$0\WT%.iDi6%K-f)_^mQ6,.2n%$%$
ike-proposal 1
remote-address 10.1.5.2
#
ipsec proposal pro1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes 256
#
ipsec policy policy1 1 isakmp
security acl 3018
ike-peer peer1
proposal pro1
#
interface GigabitEthernet0/1/17
undo shutdown
ipv6 enable
ip address 10.1.2.1 255.255.255.0
ipv6 address 2001:db8:1::1/64
ipv6 neighbor 2001:db8:1::2 00e0-fc12-3456
undo dcn
#
interface GigabitEthernet0/1/18.10
vlan-type dot1q 200
ip address 10.1.1.6 255.255.255.0
#
interface LoopBack111
ip address 1.1.1.6 255.255.255.255
binding tunnel gre
#
interface Tunnel1600
ip address 10.1.5.1 255.255.255.0
tunnel-protocol ipsec
ipsec policy policy1 service-instance-group group1
#
interface Tunnel200
ipv6 enable
ip address 10.1.4.1 255.255.255.0
ipv6 address 2001:db8:3::1/64
tunnel-protocol gre
source LoopBack111
destination 1.1.1.7
#
ip route-static 10.1.3.0 255.255.255.0 Tunnel200 1.1.1.7
ip route-static 10.1.5.2 255.255.255.255 GigabitEthernet0/1/18.10 10.1.1.7
ip route-static 1.1.1.7 255.255.255.255 Tunnel1600 10.1.5.2
#
ipv6 route-static 2001:db8:2::2 64 Tunnel200
#
return
- Device B configuration file
#
sysname DeviceB
#
ike dpd interval 10 10
#
service-location 1
location slot 1
#
service-instance-group group1
service-location 1
#
acl number 3018
rule 5 permit gre source 1.1.1.7 0 destination 1.1.1.6 0
#
ike proposal 1
encryption-algorithm aes-cbc 256
dh group14
authentication-algorithm sha2-256
integrity-algorithm hmac-sha2-256
#
ike peer peer1
pre-shared-key %$%$0\WT%.iDi6%K-f)_^mQ6,.2n%$%$
ike-proposal 1
remote-address 10.1.5.1
#
ipsec proposal pro1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes 256
#
ipsec policy policy1 1 isakmp
security acl 3018
ike-peer peer1
proposal pro1
#
interface GigabitEthernet0/1/1.10
vlan-type dot1q 200
ip address 10.1.1.7 255.255.255.0
#
interface LoopBack111
ip address 1.1.1.7 255.255.255.255
binding tunnel gre
#
interface Tunnel1600
ip address 10.1.5.2 255.255.255.0
tunnel-protocol ipsec
ipsec policy policy1 service-instance-group group1
#
interface Tunnel200
ipv6 enable
ip address 10.1.4.2 255.255.255.0
ipv6 address 2001:db8:3::2/64
tunnel-protocol gre
source LoopBack111
destination 1.1.1.6
#
ip route-static 10.1.2.0 255.255.255.0 Tunnel200 1.1.1.6
ip route-static 10.1.5.1 255.255.255.255 GigabitEthernet0/1/1.10 10.1.1.6
ip route-static 1.1.1.6 255.255.255.255 Tunnel1600 10.1.5.1
#
ipv6 route-static 2001:db8:1::2 64 Tunnel200
#
return

