Example for Configuring VPN-based L2TP Tunnels for User Access
This section provides an example for configuring VPN-based L2TP tunnels for user access.
Networking Requirements
On the network shown in Figure 1, a carrier expects to use private network addresses to establish L2TP tunnels for saving public network addresses.

Interfaces 1 through 3 in this example represent GE 0/1/1, GE 0/1/8.100, and GE 0/1/2, respectively.
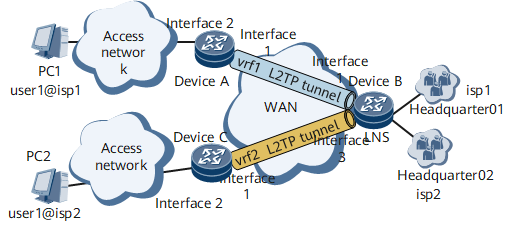
Device |
Tunnel Interface |
IP Address |
Loopback Interface |
IP Address |
Device A |
GE 0/1/1 |
10.0.0.1/24 |
Loopback 0 |
1.1.1.1 |
Device B |
GE 0/1/1 |
10.0.0.2/24 |
Loopback 0 |
3.3.3.3 |
Device B |
GE 0/1/2 |
10.10.0.2/24 |
Loopback 1 |
4.4.4.4 |
Device C |
GE 0/1/1 |
10.10.0.1/24 |
Loopback 1 |
2.2.2.2 |
Configuration Roadmap
The configuration roadmap is as follows:
Configure a dial-up connection on the user side.
Configure the LACs.
Configure the LNS.
Data Preparation
To complete the configuration, you need the following data:
Usernames and passwords of PC1 and PC2
Tunnel password, tunnel name on the LNS, and tunnel names on the LACs
VPN instance names
Virtual template IDs and L2TP group IDs
Number, range, and address mask of the remote address pool
Procedure
- Configure a dial-up connection on the user side.
To create a dial-up connection, dial the Device A access number for receiving the addresses assigned by LNSs.
Enter the username user1@isp1 and password (already registered on the LNS) in the displayed dial-up terminal window on PC1.
Enter the username user1@isp2 and password (already registered on the LNS) in the displayed dial-up terminal window on PC2.
- Configure Device A (LAC).
# Create a virtual template and configure a PPP authentication mode for it.
<Device> system-view [~Device] sysname DeviceA [*DeviceA] interface virtual-template 1 [*DeviceA-Virtual-Template1] ppp authentication-mode chap [*DeviceA-Virtual-Template1] commit [~DeviceA-Virtual-Template1] quit
# Bind virtual template 1 to GE 0/1/8.100.
[~DeviceA] interface gigabitethernet 0/1/8.100 [*DeviceA-GigabitEthernet0/1/8.100] pppoe-server bind virtual-template 1 [*DeviceA-GigabitEthernet0/1/8.100] user-vlan 1 100 [*DeviceA-GigabitEthernet0/1/8.100-vlan-1-100] commit [~DeviceA-GigabitEthernet0/1/8.100-vlan-1-100] quit
# Configure BAS.
[~DeviceA-GigabitEthernet0/1/8.100] bas [*DeviceA-GigabitEthernet0/1/8.100-bas] access-type layer2-subscriber [*DeviceA-GigabitEthernet0/1/8.100-bas] authentication-method ppp [*DeviceA-GigabitEthernet0/1/8.100-bas] commit [~DeviceA-GigabitEthernet0/1/8.100-bas] quit [~DeviceA-GigabitEthernet0/1/8.100] quit
# Create a VPN instance.
[~DeviceA] ip vpn-instance vrf1 [*DeviceA-vpn-instance-vrf1] route-distinguisher 100:1 [*DeviceA-vpn-instance-vrf1] apply-label per-instance [*DeviceA-vpn-instance-vrf1] vpn-target 100:1 both [*DeviceA–vpn-instance-vrf1] commit [~DeviceA–vpn-instance-vrf1] quit
# Bind the LAC interface connected to the LNS to the VPN instance.
[~DeviceA] interface gigabitethernet0/1/1 [*DeviceA-GigabitEthernet0/1/1] ip binding vpn-instance vrf1 [*DeviceA--GigabitEthernet0/1/1] ip address 10.0.0.1 255.255.255.0 [*DeviceA--GigabitEthernet0/1/1] commit [~DeviceA--GigabitEthernet0/1/1] quit
# Create loopback 0 and bind it to the VPN instance.
[~DeviceA] interface loopback0 [*DeviceA-LoopBack0] ip binding vpn-instance vrf1 [*DeviceA-LoopBack0] ip address 1.1.1.1 255.255.255.255 [*DeviceA-LoopBack0] commit [~DeviceA-LoopBack0] quit
# Configure an L2TP group and L2TP attributes.
[~DeviceA] l2tp enable [*DeviceA] commit [~DeviceA] l2tp-group lac1 [*DeviceA-l2tp-lac1] tunnel name lac1 [*DeviceA-l2tp-lac1] start l2tp ip 3.3.3.3 [*DeviceA-l2tp-lac1] tunnel authentication [*DeviceA-l2tp-lac1] tunnel password cipher root@123 [*DeviceA-l2tp-lac1] tunnel source loopback0 [*DeviceA-l2tp-lac1] commit [~DeviceA-l2tp-lac1] quit
# Configure a RADIUS server group.
[~DeviceA] radius-server group radius1 [*DeviceA-radius-radius1] radius-server authentication 10.0.0.249 1812 [*DeviceA-radius-radius1] radius-server accounting 10.0.0.249 1813 [*DeviceA-radius-radius1] radius-server shared-key itellin [*DeviceA-radius-radius1] commit [~DeviceA-radius-radius1] quit
# Configure a user access domain.
[~DeviceA] aaa [*DeviceA-aaa] domain isp1 [*DeviceA-aaa-domain-isp1] l2tp-group lac1 [*DeviceA-aaa-domain-isp1] radius-server group radius1 [*DeviceA-aaa-domain-isp1] authentication-scheme default1 [*DeviceA-aaa-domain-isp1] accounting-scheme default1 [* DeviceA-aaa-domain-isp1] commit [~DeviceA-aaa-domain-isp1] quit [~DeviceA-aaa] quit
# Configure a static route to the LNS.
[~DeviceA] ip route-static vpn-instance vrf1 3.3.3.3 255.255.255.255 10.0.0.2
- Configure Device C (LAC).
# Create a virtual template and configure a PPP authentication mode for it.
<Device> system-view [~Device] sysname DeviceC [*DeviceC] interface virtual-template 1 [*DeviceC-Virtual-Template1] ppp authentication-mode chap [*DeviceC-Virtual-Template1] commit [~DeviceC-Virtual-Template1] quit
# Bind virtual template 1 to GE 0/1/8.100.
[~DeviceC] interface gigabitethernet 0/1/8.100 [*DeviceC-GigabitEthernet0/1/8.100] pppoe-server bind virtual-template 1 [*DeviceA-GigabitEthernet0/1/8.100] user-vlan 1 100 [*DeviceA-GigabitEthernet0/1/8.100-vlan-1-100] commit [~DeviceA-GigabitEthernet0/1/8.100-vlan-1-100] quit
# Configure BAS.
[~DeviceA-GigabitEthernet0/1/8.100] bas [*DeviceA-GigabitEthernet0/1/8.100-bas] access-type layer2-subscriber [*DeviceA-GigabitEthernet0/1/8.100-bas] authentication-method ppp [*DeviceA-GigabitEthernet0/1/8.100-bas] commit [~DeviceA-GigabitEthernet0/1/8.100-bas] quit [~DeviceA-GigabitEthernet0/1/8.100] quit
# Create a VPN instance.
[DeviceC] ip vpn-instance vrf2 [~DeviceC] ip vpn-instance vrf2 [*DeviceC-vpn-instance-vrf2] route-distinguisher 100:2 [*DeviceC-vpn-instance-vrf2] apply-label per-instance [*DeviceC-vpn-instance-vrf2] vpn-target 100:2 both [*DeviceC–vpn-instance-vrf2] commit [~DeviceC–vpn-instance-vrf2] quit
# Bind the LAC interface connected to the LNS to the VPN instance.
[DeviceC] interface gigabitethernet0/1/1 [~DeviceC] interface gigabitethernet0/1/1 [*DeviceC-GigabitEthernet0/1/1] ip binding vpn-instance vrf2 [*DeviceC-GigabitEthernet0/1/1] ip address 10.10.0.1 255.255.255.0 [*DeviceC-GigabitEthernet0/1/1] commit [~DeviceC-GigabitEthernet0/1/1] quit
# Create loopback 1 and bind it to the VPN instance.
[~DeviceC] interface loopback1 [*DeviceC-LoopBack1] ip binding vpn-instance vrf2 [*DeviceC-LoopBack1] ip address 2.2.2.2 255.255.255.255 [*DeviceC-LoopBack1] commit [~DeviceC-LoopBack1] quit
# Configure an L2TP group and L2TP attributes.
[~DeviceC] l2tp enable [~DeviceC] l2tp-group lac2 [*DeviceC-l2tp-lac2] tunnel name lac2 [*DeviceC-l2tp-lac2] start l2tp ip 4.4.4.4 [*DeviceC-l2tp-lac2] tunnel authentication [*DeviceC-l2tp-lac2] tunnel password cipher root@123 [*DeviceC-l2tp-lac2] tunnel source loopback1 [*DeviceC-l2tp-lac2] commit [~DeviceC-l2tp-lac2] quit
# Configure a RADIUS server group.
[~DeviceC] radius-server group radius1 [*DeviceC-radius-radius1] radius-server authentication 10.10.0.249 1812 [*DeviceC-radius-radius1] radius-server accounting 10.10.0.249 1813 [*DeviceC-radius-radius1] radius-server shared-key itellin [*DeviceC-radius-radius1] commit [~DeviceC-radius-radius1] quit
# Configure a user access domain.
[~DeviceC] aaa [*DeviceC-aaa] domain isp2 [*DeviceC-aaa-domain-isp2] l2tp-group lac2 [*DeviceC-aaa-domain-isp2] radius-server group radius1 [*DeviceC-aaa-domain-isp2] authentication-scheme default1 [*DeviceC-aaa-domain-isp2] accounting-scheme default1 [*DeviceC-aaa-domain-isp2] commit [~DeviceC-aaa-domain-isp2] quit [~DeviceC-aaa] quit
# Configure a static route to the LNS.
[~DeviceC] ip route-static vpn-instance vrf2 4.4.4.4 255.255.255.255 10.10.0.2
- Configure Device B (LNS)
# Create two VPN instances.
[~DeviceB] ip vpn-instance vrf1 [*DeviceB-vpn-instance-vrf1] route-distinguisher 100:1 [*DeviceB-vpn-instance-vrf1] apply-label per-instance [*DeviceB-vpn-instance-vrf1] vpn-target 100:1 both [*DeviceB–vpn-instance-vrf1] commit [~DeviceB–vpn-instance-vrf1] quit [~DeviceB] ip vpn-instance vrf2 [*DeviceB-vpn-instance-vrf2] route-distinguisher 100:2 [*DeviceB-vpn-instance-vrf2] apply-label per-instance [*DeviceB-vpn-instance-vrf2] vpn-target 100:2 both [*DeviceB–vpn-instance-vrf2] commit [~DeviceB–vpn-instance-vrf2] quit
# Create two interfaces and bind each to a VPN instance.
[~DeviceB] interface gigabitethernet0/1/1 [*DeviceB-GigabitEthernet0/1/1] ip binding vpn-instance vrf1 [*DeviceB--GigabitEthernet0/1/1] ip address 10.0.0.2 255.255.255.0 [*DeviceB--GigabitEthernet0/1/1] commit [~DeviceB--GigabitEthernet0/1/1] quit [~DeviceB] interface gigabitethernet0/1/2 [*DeviceB-GigabitEthernet0/1/2] ip binding vpn-instance vrf2 [*DeviceB-GigabitEthernet0/1/2] ip address 10.10.0.2 255.255.255.0 [*DeviceB-GigabitEthernet0/1/2] commit [~DeviceB-GigabitEthernet0/1/2] quit
# Create loopback interfaces and bind each to a VPN instance.
[~DeviceB] interface loopback0 [*DeviceB-LoopBack0] ip binding vpn-instance vrf1 [*DeviceB-LoopBack0] ip address 3.3.3.3 255.255.255.255 [*DeviceB-LoopBack0] commit [~DeviceB-LoopBack0] quit [~DeviceB] interface loopback1 [*DeviceB-LoopBack1] ip binding vpn-instance vrf2 [*DeviceB-LoopBack1] ip address 4.4.4.4 255.255.255.255 [*DeviceB-LoopBack1] commit [~DeviceB-LoopBack1] quit
# Create a virtual template and configure a PPP authentication mode for it.
[~DeviceB] interface virtual-template 1 [*DeviceB-Virtual-Template1] ppp authentication-mode chap [*DeviceB-Virtual-Template1] commit [~DeviceB-Virtual-Template1] quit
# Enable L2TP and configure L2TP groups.
[~DeviceB] l2tp enable [*DeviceB] commit [~DeviceB] l2tp-group lns1 [*DeviceB-l2tp-lns1] tunnel name lns1 [*DeviceB-l2tp-lns1] allow l2tp virtual-template 1 remote lac1 [*DeviceB-l2tp-lns1] tunnel authentication [*DeviceB-l2tp-lns1] tunnel password cipher root@123 [*DeviceB-l2tp-lns1] commit [~DeviceB-l2tp-lns1] quit [~DeviceB] l2tp-group lns2 [*DeviceB-l2tp-lns1] tunnel name lns2 [*DeviceB-l2tp-lns1] allow l2tp virtual-template 1 remote lac2 [*DeviceB-l2tp-lns1] tunnel authentication [*DeviceB-l2tp-lns1] tunnel password cipher root@123 [*DeviceB-l2tp-lns1] commit [~DeviceB-l2tp-lns1] quit
# Create an LNS group named group1, and bind the tunnel board and tunnel interfaces to the LNS group.
[~DeviceB] lns-group group1 [*DeviceB-lns-group-group1] bind slot 1 [*DeviceB-lns-group-group1] bind source LoopBack0 [*DeviceB-lns-group-group1] bind source LoopBack1 [*DeviceB-lns-group-group1] commit [~DeviceB-lns-group-group1] quit
# Configure address pools used to assign addresses to users.
[~DeviceB] ip pool pool1 bas local [*DeviceB-ip-pool-pool1] gateway 10.1.10.1 255.255.255.0 [*DeviceB-ip-pool-pool1] section 0 10.1.10.10 10.1.10.100 [*DeviceB-ip-pool-pool1] commit [~DeviceB-ip-pool-pool1] quit [~DeviceB] ip pool pool2 bas local [*DeviceB-ip-pool-pool2] gateway 10.1.155.1 255.255.255.0 [*DeviceB-ip-pool-pool2] section 0 10.1.155.10 10.1.155.100 [*DeviceB-ip-pool-pool2] commit [~DeviceB-ip-pool-pool2] quit
# Configure a RADIUS server group.
[~DeviceB] radius-server group radius1 [*DeviceB-radius-radius1] radius-server authentication 10.1.20.1 1812 [*DeviceB-radius-radius1] radius-server accounting 10.1.20.1 1813 [*DeviceB-radius-radius1] radius-server shared-key itellin [*DeviceB-radius-radius1] commit [~DeviceB-radius-radius1] quit
# Configure user access domains.
[~DeviceB] aaa [*DeviceB-aaa] domain isp1 [*DeviceB-aaa-domain-isp1] radius-server group radius1 [*DeviceB-aaa-domain-isp1] authentication-scheme default1 [*DeviceB-aaa-domain-isp1] accounting-scheme default1 [*DeviceB-aaa-domain-isp1] ip-pool pool1 [*DeviceB-aaa-domain-isp1] commit [~DeviceB-aaa-domain-isp1] quit [~DeviceB-aaa] domain isp2 [*DeviceB-aaa-domain-isp2] radius-server group radius1 [*DeviceB-aaa-domain-isp2] authentication-scheme default1 [*DeviceB-aaa-domain-isp2] accounting-scheme default1 [*DeviceB-aaa-domain-isp2] ip-pool pool2 [*DeviceB-aaa-domain-isp2] commit [~DeviceB-aaa-domain-isp2] quit [~DeviceB-aaa] quit
# Configure static routes to the LACs.
[~DeviceB] ip route-static vpn-instance vrf1 1.1.1.1 255.255.255.255 10.0.0.1 [~DeviceB] ip route-static vpn-instance vrf2 2.2.2.2 255.255.255.255 10.10.0.1
- Verify the configuration.
[~DeviceA] ping -vpn-instance vrf1 3.3.3.3 PING 3.3.3.3: 56 data bytes, press CTRL_C to break Reply from 3.3.3.3: bytes=56 Sequence=1 ttl=255 time=12 ms Reply from 3.3.3.3: bytes=56 Sequence=2 ttl=255 time=10 ms Reply from 3.3.3.3: bytes=56 Sequence=3 ttl=255 time=5 ms Reply from 3.3.3.3: bytes=56 Sequence=4 ttl=255 time=8 ms --- 3.3.3.3 ping statistics --- 4 packet(s) transmitted 4 packet(s) received 0.00% packet loss round-trip min/avg/max = 5/8/12 ms [~DeviceC] ping -vpn-instance vrf2 4.4.4.4 PING 4.4.4.4: 56 data bytes, press CTRL_C to break Reply from 4.4.4.4: bytes=56 Sequence=1 ttl=255 time=12 ms Reply from 4.4.4.4: bytes=56 Sequence=2 ttl=255 time=10 ms Reply from 4.4.4.4: bytes=56 Sequence=3 ttl=255 time=5 ms Reply from 4.4.4.4: bytes=56 Sequence=4 ttl=255 time=8 ms --- 4.4.4.4 ping statistics --- 4 packet(s) transmitted 4 packet(s) received 0.00% packet loss round-trip min/avg/max = 5/8/12 ms [~DeviceA] test l2tp-tunnel l2tp-group lac1 ip-address 3.3.3.3 Testing L2TP tunnel connectivity now....... Test L2TP tunnel connectivity success. [~DeviceC] test l2tp-tunnel l2tp-group lac2 ip-address 4.4.4.4 Testing L2TP tunnel connectivity now....... Test L2TP tunnel connectivity success.
Configuration Files
Device A configuration file
# sysname DeviceA # l2tp enable # radius-server group radius1 radius-server authentication 10.0.0.249 1812 radius-server accounting 10.0.0.249 1813 radius-server shared-key %^%#vS%796FO7%C~pB%CR=q;j}gSCqR-X6+P!.DYI@)%^% # interface Virtual-Template1 ppp authentication-mode chap # interface GigabitEthernet0/1/8.100 undo shutdown pppoe-server bind Virtual-Template 1 user-vlan 1 100 bas access-type layer2-subscriber # ip vpn-instance vrf1 route-distinguisher 100:1 apply-label per-instance vpn-target 100:1 export-extcommunity vpn-target 100:1 import-extcommunity # interface LoopBack0 ip binding vpn-instance vrf1 ip address 1.1.1.1 255.255.255.255 l2tp-group lac1 tunnel password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81fv"uMoKKZ.1k"`AO!X2K2N.b~'NB^V!!!!!!!!!!1!!!!o/4J(q"J1F.!K9%M!6x8%@%# tunnel name lac1 start l2tp ip 3.3.3.3 tunnel source LoopBack0 # aaa domain isp1 authentication-scheme default1 accounting-scheme default1 radius-server group radius1 l2tp-group lac1 # interface GigabitEthernet0/1/1 undo shutdown ip binding vpn-instance vrf1 ip address 10.0.0.1 255.255.255.0 # ip route-static vpn-instance vrf1 3.3.3.3 255.255.255.255 10.0.0.2 # return
Device C configuration file
# sysname DeviceC # l2tp enable # radius-server group radius1 radius-server authentication 10.10.0.249 1812 radius-server accounting 10.10.0.249 1813 radius-server shared-key %^%#vS%796FO7%C~pB%CR=q;j}gSCqR-X6+P!.DYI@)%^% # interface Virtual-Template1 ppp authentication-mode chap # interface GigabitEthernet0/1/8.100 undo shutdown pppoe-server bind Virtual-Template 1 user-vlan 1 100 bas access-type layer2-subscriber # ip vpn-instance vrf2 route-distinguisher 200:1 apply-label per-instance vpn-target 200:1 export-extcommunity vpn-target 200:1 import-extcommunity # interface LoopBack0 ip binding vpn-instance vrf2 ip address 2.2.2.2 255.255.255.255 l2tp-group lac2 tunnel password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81fv"uMoKKZ.1k"`AO!X2K2N.b~'NB^V!!!!!!!!!!1!!!!o/4J(q"J1F.!K9%M!6x8%@%# tunnel name lac2 start l2tp ip 4.4.4.4 tunnel source LoopBack0 # aaa domain isp2 authentication-scheme default1 accounting-scheme default1 radius-server group radius1 l2tp-group lac2 # interface GigabitEthernet0/1/1 undo shutdown ip binding vpn-instance vrf2 ip address 10.10.0.1 255.255.255.0 # ip route-static vpn-instance vrf2 4.4.4.4 255.255.255.255 10.10.0.2 # return
Device B configuration file
# sysname DeviceB # l2tp enable # radius-server group radius1 radius-server authentication 10.1.20.1 1812 radius-server accounting 10.1.20.1 1813 radius-server shared-key %^%#vS%796FO7%C~pB%CR=q;j}gSCqR-X6+P!.DYI@)%^% # interface Virtual-Template1 ppp authentication-mode chap # ip vpn-instance vrf1 route-distinguisher 100:1 apply-label per-instance vpn-target 100:1 export-extcommunity vpn-target 100:1 import-extcommunity # ip vpn-instance vrf2 route-distinguisher 100:2 apply-label per-instance vpn-target 100:2 export-extcommunity vpn-target 100:2 import-extcommunity # interface LoopBack0 ip binding vpn-instance vrf1 ip address 3.3.3.3 255.255.255.255 # interface LoopBack1 ip binding vpn-instance vrf2 ip address 4.4.4.4 255.255.255.255 # l2tp-group lns1 allow l2tp virtual-template 1 remote lac1 tunnel password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81fv"uMoKKZ.1k"`AO!X2K2N.b~'NB^V!!!!!!!!!!1!!!!o/4J(q"J1F.!K9%M!6x8%@%# tunnel name lns1 # l2tp-group lns2 allow l2tp virtual-template 1 remote lac2 tunnel password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81fv"uMoKKZ.1k"`AO!X2K2N.b~'NB^V!!!!!!!!!!1!!!!o/4J(q"J1F.!K9%M!6x8%@%# tunnel name lns2 # lns-group group1 bind slot 1 bind source LoopBack0 bind source LoopBack1 # ip pool pool1 bas local gateway 10.1.10.1 255.255.255.0 section 0 10.1.10.10 10.10.0.100 # ip pool pool2 bas local gateway 10.1.155.1 255.255.255.0 section 0 10.1.155.10 10.10.0.100 # aaa domain isp1 radius-server group radius1 authentication-scheme default1 accounting-scheme default1 ip-pool pool1 domain isp2 radius-server group radius1 authentication-scheme default1 accounting-scheme default1 ip-pool pool2 # interface GigabitEthernet0/1/1 undo shutdown ip binding vpn-instance vrf1 ip address 10.0.0.2 255.255.255.0 # interface GigabitEthernet0/1/2 undo shutdown ip binding vpn-instance vrf2 ip address 10.10.0.2 255.255.255.0 # ip route-static vpn-instance vrf1 1.1.1.1 255.255.255.255 10.0.0.1 ip route-static vpn-instance vrf2 2.2.2.2 255.255.255.255 10.10.0.1 # return