Example for Configuring the NAT Function
This section provides an example for configuring the NAT function to implement multiple-to-multiple translations from internal addresses of enterprise users to external addresses and allow only PCs on a specified network segment to access the Internet.
Networking Requirements
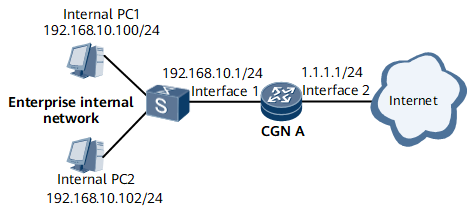
On the network shown in Figure 1, the NetEngine 8000 F performs the NAT function to help PCs within the enterprise network access the Internet. The NetEngine 8000 F uses GE 0/1/0 to connect to the enterprise network. The NetEngine 8000 F is connected to the Internet through GE 0/1/1. The company has five public IP addresses ranging from 11.11.11.101/32 to 11.11.11.105/32.
- Only PCs on the network segment of 192.168.10.0/24 can access the Internet.
- Multiple-to-multiple NAT translation is performed for internal and external IP addresses.
Configuration Roadmap
The configuration roadmap is as follows:
- Configure basic NAT functions.
- Configure a NAT traffic diversion policy.
Data Preparation
Service-location group index: 1
Service-instance group name: group1
NAT instance name: nat1; NAT instance index: 1
NAT address pool name for NATA: address-group1; NAT address pool ID: 1; IP address segment: 11.11.11.101 to 11.11.11.105
ACL name: 3001
Number and IP address of the interface to which the NAT traffic diversion policy is applied
Procedure
- Configure basic NAT functions.
- Configure a NAT traffic diversion policy.
Apply a NAT traffic diversion policy on either an inbound or outbound interface as required.

A NAT traffic diversion policy on an inbound interface and that on an outbound interface cannot be configured simultaneously on a device.
- Apply the NAT traffic policy to the inbound interface.
- Configure an ACL numbered 3001 and an ACL rule numbered 1 to allow only hosts on the network segment 192.168.10.0/24 to access the Internet.
[~NATA] acl 3001 [*NATA-acl4-advance-3001] rule 1 permit ip source 192.168.10.0 0.0.0.255 [*NATA-acl4-advance-3001] commit [~NATA-acl4-advance-3001] quit
- Configure a traffic classifier.
[~NATA] traffic classifier classifier1 [*NATA-classifier-classifier1] if-match acl 3001 [*NATA-classifier-classifier1] commit [~NATA-classifier-classifier1] quit
- Define a traffic behavior behavior1 and bind it to the NAT instance nat1.
[~NATA] traffic behavior behavior1 [*NATA-behavior-behavior1] nat bind instance nat1 [*NATA-behavior-behavior1] commit [~NATA-behavior-behavior1] quit
- Define a NAT traffic policy named policy1 to associate the traffic classifier with the traffic behavior.
[~NATA] traffic policy policy1 [*NATA-trafficpolicy-policy1] classifier classifier1 behavior behavior1 [*NATA-trafficpolicy-policy1] commit [~NATA-trafficpolicy-policy1] quit
- Apply the NAT traffic diversion policy in the GE 0/1/0 interface view.
[~NATA] interface gigabitEthernet 0/1/0 [~NATA-GigabitEthernet0/1/0] ip address 192.168.10.1 24 [*NATA-GigabitEthernet0/1/0] traffic-policy policy1 inbound [*NATA-GigabitEthernet0/1/0] commit [~NATA-GigabitEthernet0/1/0] quit
- Configure a NAT traffic diversion policy on an outbound interface.
- Configure an ACL numbered 3001 and an ACL rule numbered 1 to allow only hosts on the network segment 192.168.10.0/24 to access the Internet.
[~NATA] acl 3001 [*NATA-acl4-advance-3001] rule 1 permit ip source 192.168.10.0 0.0.0.255 [*NATA-acl4-advance-3001] commit [~NATA-acl4-advance-3001] quit
- Bind ACL 3001 to NAT instance nat1 in the view of GE 0/1/1.
[~NATA] interface gigabitEthernet 0/1/1 [~NATA-GigabitEthernet0/1/1] ip address 1.1.1.1 24 [*NATA-GigabitEthernet0/1/1] nat bind acl 3001 instance nat1 [*NATA-GigabitEthernet0/1/1] commit [~NATA-GigabitEthernet0/1/1] quit
- Configure an IP address for GE 0/1/0.
[~NATA] interface gigabitEthernet 0/1/0 [~NATA-GigabitEthernet0/1/0] ip address 192.168.10.1 24 [*NATA-GigabitEthernet0/1/0] commit [~NATA-GigabitEthernet0/1/0] quit
- Verify the configuration.
# Verify NAT user information.
[~NATA] display nat user-information slot 1 verbose This operation will take a few minutes. Press 'Ctrl+C' to break ... Slot: 1 Total number: 1. --------------------------------------------------------------------------- User Type : NAT444 CPE IP : 192.168.10.100 User ID : - VPN Instance : - Address Group : address-group1 NoPAT Address Group : - NAT Instance : nat1 Public IP : 11.11.11.102 NoPAT Public IP : - Total/TCP/UDP/ICMP Session Limit : 8192/10240/10240/512 Total/TCP/UDP/ICMP Session Current : 1/0/1/0 Total/TCP/UDP/ICMP Rev Session Limit : 8192/10240/10240/512 Total/TCP/UDP/ICMP Rev Session Current: 0/0/0/0 Nat ALG Enable : NULL Aging Time(s) : - Left Time(s) : - Session Limit Discard Count : 0 -->Transmit Packets : 1046632 -->Transmit Bytes : 90409306 -->Drop Packets : 0 <--Transmit Packets : 0 <--Transmit Bytes : 0 <--Drop Packets : 0 ---------------------------------------------------------------------------
Configuration Files
NATA configuration file when a NAT traffic diversion policy is used on an inbound interface
# sysname NATA # service-location 1 location slot 1 # service-instance-group group1 service-location 1 # nat instance nat1 id 1 service-instance-group group1 nat address-group address-group1 group-id 1 section 1 11.11.11.101 11.11.11.105 # acl number 3001 rule 1 permit ip source 192.168.10.0 0.0.0.255 # traffic classifier classifier1 if-match acl 3001 # traffic behavior behavior1 nat bind instance nat1 # traffic policy policy1 classifier classifier1 behavior behavior1 # interface GigabitEthernet 0/1/0 undo shutdown ip address 192.168.10.1 255.255.255.0 traffic-policy policy1 inbound # interface GigabitEthernet 0/1/1 undo shutdown ip address 1.1.1.1 255.255.255.0 # return
NATA configuration file when a NAT traffic diversion policy is used on an outbound interface
# sysname NATA # service-location 1 location slot 1 # service-instance-group group1 service-location 1 # nat instance nat1 id 1 service-instance-group group1 nat address-group address-group1 group-id 1 section 1 11.11.11.101 11.11.11.105 # acl number 3001 rule 1 permit ip source 192.168.10.0 0.0.0.255 # interface GigabitEthernet 0/1/0 undo shutdown ip address 192.168.10.1 255.255.255.0 # interface GigabitEthernet 0/1/1 undo shutdown ip address 1.1.1.1 255.255.255.0 nat bind acl 3001 instance nat1 # return