Example for Configuring Simplified NAT
This section provides an example for configuring the simplified NAT function to implement multiple-to-multiple IP address translation between private and public networks and allow PCs on a specified network segment to access the Internet.
Networking Requirements
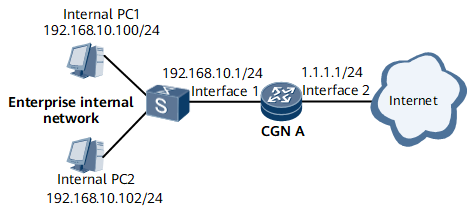
In Figure 1, the router performs the NAT function to help PCs within an enterprise network access the Internet. The router uses GE 0/1/8 to connect to the enterprise network. The router's GE 0/1/9 is connected to the Internet. The enterprise is assigned public IP addresses of 11.11.11.101/32 through 11.11.11.105/32.
- PCs only on the network segment of 192.168.10.0/24 can access the Internet.
- Multiple-to-multiple NAT is performed for IP addresses between private and public networks.
Configuration Roadmap
The configuration roadmap is as follows:
- Configure simplified basic NAT functions.
- Configure a simplified NAT traffic diversion policy.
Data Preparation
NAT instance name (nat1) and index (1)
NATA's NAT address pool name (address-group1), address pool number (1), a range of public IP addresses (11.11.11.101 through 11.11.11.105)
ACL number: 3001
Name and IP address of each interface to which a NAT traffic diversion policy is applied
Procedure
- Configure basic NAT functions.
- Configure a NAT traffic diversion policy. Simplified NAT supports only outbound interface-based traffic diversion.
- Verify the configuration.
# Run the display nat user-information slot command to view NAT user information.
[~NATA] display nat user-information slot 1 verbose This operation will take a few minutes. Press 'Ctrl+C' to break ... Slot: 1 Total number: 1. --------------------------------------------------------------------------- User Type : NAT444 CPE IP : 192.168.10.100 User ID : - VPN Instance : - Address Group : address-group1 NAT Instance : nat1 Public IP : 11.11.11.101 Total/TCP/UDP/ICMP Session Limit : 8192/10240/10240/512 Total/TCP/UDP/ICMP Session Current : 1/0/1/0 Total/TCP/UDP/ICMP Rev Session Limit : 8192/10240/10240/512 Total/TCP/UDP/ICMP Rev Session Current: 0/0/0/0 Nat ALG Enable : NULL Aging Time(s) : - Left Time(s) : - Session Limit Discard Count : 0 -->Transmit Packets : 9753259 -->Transmit Bytes : 1111770864 -->Drop Packets : 0 <--Transmit Packets : 0 <--Transmit Bytes : 0 <--Drop Packets : 0 ---------------------------------------------------------------------------
# Run the display nat simple-configuration address-group command to view simplified NAT address pool information.
[~HUAWEI] display nat simple-configuration address-group 2019-02-19 10:21:03.156 nat address-group address-group1 group-id 1 11.11.11.101 11.11.11.105
Configuration Files
NATA configuration file when a NAT traffic diversion policy is used on an outbound interface (In this configuration file, the traffic diversion policy is bound to the NAT address pool.)
# sysname NATA # nat instance nat1 id 1 simple-configuration # nat address-group address-group1 group-id 1 11.11.11.101 11.11.11.105 # acl number 3001 rule 1 permit ip source 192.168.10.0 0.0.0.255 # interface GigabitEthernet 0/1/9 undo shutdown ip address 1.1.1.1 255.255.255.0 nat bind acl 3001 address-group address-group1 # interface GigabitEthernet 0/1/8 undo shutdown ip address 192.168.10.1 255.255.255.0 # return