Example for Configuring Bidirectional NAT
This section provides an example for configuring bidirectional NAT on an enterprise network. This function protects data within the enterprise network and translates both the source and destination, without exposing internal server data. A configuration networking diagram is provided to help you understand the configuration procedure.
Networking Requirements
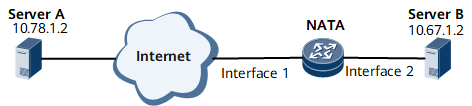
In Figure 1, the router translates private IP address of servers A and B to public IP addresses before the servers communicate with the Internet. When server A attempts to access server B, server A sends a packet with a private source IP address of 10.78.1.2 and the destination IP address of 11.11.11.1 (server B's public address). When server B attempts to access server A, server B sends a packet with a private source IP address of 10.67.1.2 and the destination IP address of 11.11.11.2 (server A's public address).
Configuration Roadmap
- Create a NAT instance and associate a service board with the NAT instance.
- Configure a mapping between the NAT address pool, internal servers' private IP addresses, and public addresses.
- Configure an outbound NAT traffic diversion policy.
Data Preparation
Service-location group index: 1
Service-instance group name: group1
NAT instance names and indexes: nata with index 1; natb with index 2
NATA's address pools: address-groupa and address-groupb
Server public IP address: 11.11.11.2 for server A and 11.11.11.1 for server B
ACL numbers: 2464 and 2465
Names and IP addresses of interfaces to which an outbound NAT traffic diversion policy applies: GE 0/1/1 with IP address 10.78.1.1/24 and GE 0/1/0 with IP address 10.67.1.1/24
Procedure
- Create a NAT instance and associate a service board with the NAT instance.
<HUAWEI> system-view [~HUAWEI] sysname NATA [*HUAWEI] commit [~NATA] service-location 1 [*NATA-service-location-1] location slot 1 [*NATA-service-location-1] commit [~NATA-service-location-1] quit [~NATA] service-instance-group group1 [*NATA-service-instance-group-group1] service-location 1 [*NATA-service-instance-group-group1] commit [~NATA-service-instance-group-group1] quit [~NATA] nat instance nata id 1 [*NATA-nat-instance-nata] service-instance-group group1 [*NATA-nat-instance-nata] commit [~NATA-nat-instance-nata] quit [~NATA] nat instance natb id 2 [*NATA-nat-instance-natb] service-instance-group group1 [*NATA-nat-instance-natb] commit [~NATA-nat-instance-natb] quit
- Configure a mapping between the NAT address pool, internal servers' private IP addresses, and public addresses.
# In the view of a NAT instance named nata, configure an IP address pool named address-groupa with an IP address segment ranging from 11.1.1.1 to 11.1.1.10 and map the NAT-A's private IP address of 10.78.1.2 to a public IP address of 11.11.11.2.
[~NATA] nat instance nata [~NATA-nat-instance-nata] nat address-group address-groupa group-id 111 11.1.1.1 11.1.1.10 [*NATA-nat-instance-nata] nat server protocol udp global 11.11.11.2 inside 10.78.1.2 [*NATA-nat-instance-nata] commit [~NATA-nat-instance-nata] quit
# In the view of a NAT instance named natb, configure an IP address pool named address-groupb with an IP address segment ranging from 11.1.1.11 to 11.1.1.20 and map the NAT-B's private IP address of 10.67.1.2 to a public IP address of 11.11.11.1.
[~NATA] nat instance natb [~NATA-nat-instance-natb] nat address-group address-groupb group-id 112 11.1.1.11 11.1.1.20 [*NATA-nat-instance-natb] nat server protocol udp global 11.11.11.1 inside 10.67.1.2 [*NATA-nat-instance-natb] commit [~NATA-nat-instance-natb] quit
- Configure an outbound NAT traffic policy.
- Verify the configuration.
# View NAT user information.
[~NATA] display nat instance nat instance nata id 1 service-instance-group group1 nat address-group address-groupa group-id 111 11.1.1.1 11.1.1.10 nat server protocol udp global 11.11.11.2 inside 10.78.1.2 nat instance natb id 2 service-instance-group group1 nat address-group address-groupb group-id 112 11.1.1.11 11.1.1.20 nat server protocol udp global 11.11.11.1 inside 10.67.1.2# Check server mapping entries of all users.
[~NATA] display nat server-map This operation will take a few minutes. Press 'Ctrl+C' to break ... Slot: 1 Total number: 4. NAT Instance: nata Protocol:UDP, VPN:--->- Server:10.78.1.2[11.11.11.2]->ANY Tag:0x0, TTL:-, Left-Time:- CPE IP:10.78.1.2 NAT Instance: nata Protocol:UDP, VPN:--->- Server reverse:ANY->11.11.11.2[10.78.1.2] Tag:0x0, TTL:-, Left-Time:- CPE IP:10.78.1.2 NAT Instance: natb Protocol:UDP, VPN:--->- Server:10.67.1.2[11.11.11.1]->ANY Tag:0x0, TTL:-, Left-Time:- CPE IP:10.67.1.2 NAT Instance: natb Protocol:UDP, VPN:--->- Server reverse:ANY->11.11.11.1[10.67.1.2] Tag:0x0, TTL:-, Left-Time:- CPE IP:10.67.1.2
Configuration Files
NATA configuration file
# sysname NATA # service-location 1 location slot 1 # service-instance-group group1 service-location 1 # nat instance nata id 1 service-instance-group group1 nat address-group address-groupa group-id 111 11.1.1.1 11.1.1.10 nat server protocol udp global 11.11.11.2 inside 10.78.1.2 nat instance natb id 2 service-instance-group group1 nat address-group address-groupb group-id 112 11.1.1.11 11.1.1.20 nat server protocol udp global 11.11.11.1 inside 10.67.1.2 # acl number 2464 rule 5 permit source 10.78.1.0 0.0.0.255 # acl number 2465 rule 5 permit source 10.67.1.0 0.0.0.255 # interface GigabitEthernet0/1/1 undo shutdown ip address 10.78.1.1 255.255.255.0 undo dcn nat bind acl 2465 instance natb # interface GigabitEthernet0/1/0 undo shutdown ip address 10.67.1.1 255.255.255.0 undo dcn nat bind acl 2464 instance nata # return