Example for Configuring IP-based Multi-Field Classification on an MPLS Interface
This section provides an example for configuring IP-based multi-field (MF) classification on an MPLS interface.
Networking Requirements
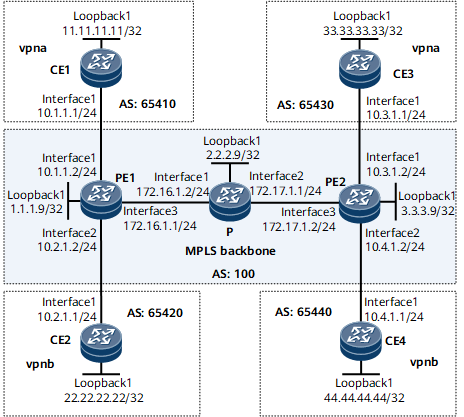
As shown in Figure 1, PE1, P, and PE2 are routers on an MPLS backbone network. CE1, CE2, CE3, and CE4 are access routers on the edge of the backbone network. Use PE1 as an example. You can configure IP-based MF classification on the public network interface (interface 3) of PE1 to implement traffic control on the public network side and verify the packet sending and receiving through traffic statistics.

Interfaces 1 through 3 in this example are GE 0/1/0, GE 0/1/8, and GE 0/1/16, respectively.
Configuration Roadmap
The configuration roadmap is as follows:
Configure basic MPLS functions.
Configure IP-based MF classification for outgoing or incoming packets on the public network interface.
Configure an ACL rule.
Configure a traffic classifier.
Configure a traffic behavior.
Configure a traffic policy.
Apply the traffic policy.
Data Preparation
To complete the configuration, you need the following data:
ACL number
Names of the traffic classifier, traffic behavior, and traffic policy, and number of the interface to which the traffic policy is applied
Procedure
- Configure basic MPLS functions.
For details about how to configure basic MPLS functions, see Example for Configuring BGP/MPLS IP VPN in HUAWEI NetEngine 8000 F Series Configuration Guide - VPN - BGP/MPLS IP VPN Configuration.
- Configure IP-based MF classification for outgoing or incoming packets on the public network interface.
<HUAWEI> system-view [~HUAWEI] sysname PE1 [*HUAWEI] commit [~PE1] slot 1 [~PE1-slot-1] traffic-policy match-ip-layer mpls-pop [*PE1-slot-1] traffic-policy match-ip-layer mpls-push [*PE1-slot-1] commit [~PE1-slot-1] quit
- Configure an ACL rule.
[~PE1] acl number 3333 [*PE1-acl-advance-3333] rule 5 permit ip source 11.11.11.11 0 destination 33.33.33.33 0 [*PE1-acl-advance-3333] rule 10 permit ip source 33.33.33.33 0 destination 11.11.11.11 0 [*PE1-acl-advance-3333] commit [~PE1-acl-advance-3333] quit
- Configure a traffic classifier.
[~PE1] traffic classifier c1 [*PE1-classifier-c1] if-match acl 3333 [*PE1-classifier-c1] commit [~PE1-classifier-c1] quit
- Configure a traffic behavior.
[~PE1] traffic behavior b1 [*PE1-behavior-b1] permit [*PE1-behavior-b1] commit [~PE1-behavior-b1] quit
- Configure a traffic policy.
[~PE1] traffic policy p1 [*PE1-trafficpolicy-p1] classifier c1 behavior b1 [*PE1-trafficpolicy-p1] share-mode [*PE1-trafficpolicy-p1] statistic enable [*PE1-trafficpolicy-p1] commit [~PE1-trafficpolicy-p1] quit
- Apply the traffic policy.
[~PE1] interface gigabitethernet 0/1/16 [~PE1-GigabitEthernet0/1/16] traffic-policy p1 inbound [*PE1-GigabitEthernet0/1/16] traffic-policy p1 outbound [*PE1-GigabitEthernet0/1/16] commit [~PE1-GigabitEthernet0/1/16] quit
- Verify the configuration.
After completing the configurations, run the ping 33.33.33.33 command on CE1 to ping CE3, and run the display traffic policy statistics command on PE1 to view statistics about traffic exchanged between CE3 and CE1.
[~PE1] display traffic policy statistics interface gigabitethernet 0/1/16 inbound Info: The statistics is shared because the policy is shared. Interface: GigabitEthernet0/1/16 Traffic policy inbound: p1 Traffic policy applied at 2017-08-30 18:30:20 Statistics enabled at 2017-08-30 18:30:20 Statistics last cleared: Never Rule number: 1 IPv4, 0 IPv6 Current status: OK! Item Packets Bytes ------------------------------------------------------------------- Matched 5 500 +--Passed 4 400 +--Dropped 1 100 Missed 0 0 Last 30 seconds rate Item pps bps ------------------------------------------------------------------- Matched 5 500 +--Passed 4 400 +--Dropped 1 100 Missed 0 0
Configuration Files on PE1
# sysname PE1 # slot 1 traffic-policy match-ip-layer mpls-pop mpls-push # acl number 3333 rule 5 permit ip source 11.11.11.11 0 destination 33.33.33.33 0 rule 10 permit ip source 33.33.33.33 0 destination 11.11.11.11 0 # traffic classifier c1 operator or if-match acl 3333 # traffic behavior b1 # traffic policy p1 share-mode statistic enable classifier c1 behavior b1 precedence 1 # interface GigabitEthernet0/1/16 undo shutdown traffic-policy p1 inbound traffic-policy p1 outbound # return