Example for Configuring RUI+EDSG in Shared Address Pool Mode
This section provides an example for configuring Redundancy User Information (RUI)+enhanced dynamic service gateway (EDSG) in shared address pool mode.
Usage Scenario
High reliability is a basic requirement for carrier-class devices. An NetEngine 8000 F that functions as a service aggregation router carries multiple services, such as HSI, VoIP, and IPTV. It connects to a core network to implement Layer 3 routing functions and to the aggregation layer to terminate Layer 2 user packets for user access. The NetEngine 8000 F therefore must have high reliability. Although the NetEngine 8000 F can ensure non-stop data flow forwarding, this does not guarantee interruption-free user services. If a network node or link fails and user information is not synchronized to a backup device, user services will be interrupted. To prevent this problem, dual-device hot backup is introduced.
Requirements on Hardware
User access boards are installed.
Requirements on Interconnected Devices
- Upstream device: a CR (generally) that must be able to perform route switching and support MPLS and MPLS L3VPN. It is recommended that the upstream device also be able to provide MPLS L2VPN capabilities. In dual-device hot backup scenarios, MPLS tunnels are best suited to function as protection tunnels. This is because an MPLS protection tunnel can be established from the IP core network if a direct link cannot be deployed between NetEngine 8000 Fs.
- Downstream device: an aggregation switch that must be able to learn MAC addresses from VLAN packets.
Solution Limitations
- In shared address pool mode, an address pool (an IP network segment) is planned based on services. Each service (for example, Internet access or VoIP service) corresponds to a domain's configuration. If terminals that go online through different access links have the same service (for example, Internet access service), the terminals share address pool resources in a domain. This mode is called multi-link address pool sharing.
- In actual deployment, address pools are divided based on authentication domains, which allows an address pool on the NetEngine 8000 F to be shared between links or backup groups. In this situation, forwarding control cannot be performed by advertising or withdrawing a network segment route of an address pool. To implement forwarding control, using a shared address pool and tunnel protection is recommended.
Networking Requirements
Carriers can divide networks into different subnets based on traffic destination addresses. When different users access the subnets, different rate limit and accounting are performed for the users. EDSG implements subnet division, rate limit, and accounting management on NetEngine 8000 Fs. As applications accessed by users become diversified, high reliability is required for EDSG services. To meet this requirement, deploy RUI so that EDSG service traffic is smoothly switched to the backup device if the master device fails. RUI ensures normal traffic accounting without the need of users' re-dialup.
On the network shown in Figure 1, the user goes online from Device A (master device) through PPPoE dialup. Device A and Device B implement RUI over VRRP and BFD. Device A backs up EDSG services to Device B (backup device). If Device A fails, service traffic is switched to Device B. Traffic statistics on Device A and Device B remain consistent.

Interfaces 1 through 3 in this example represent GE 0/1/0, GE 0/1/8, and GE 0/1/16, respectively.
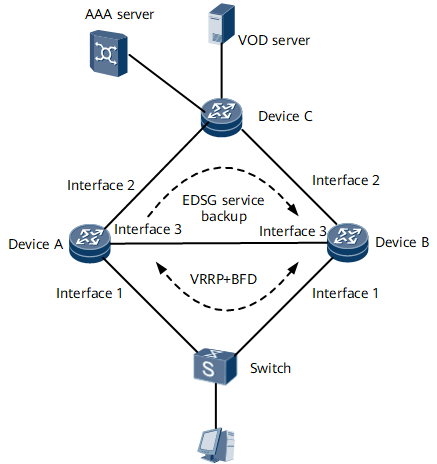
Device |
Interface |
IP Address |
Device A |
GE 0/1/0 |
10.0.1.1/24 |
Device A |
GE 0/1/8 |
10.0.0.1/24 |
Device A |
GE 0/1/16 |
10.1.1.6/24 |
Device A |
Loopback 0 |
1.1.1.1/32 |
Device A |
Loopback 1 |
22.22.22.22/32 |
Device B |
GE 0/1/0 |
10.0.1.2/24 |
Device B |
GE 0/1/8 |
10.0.2.1/24 |
Device B |
GE 0/1/16 |
10.1.1.7/24 |
Device B |
Loopback 0 |
2.2.2.2/32 |
Device B |
Loopback 1 |
88.88.88.88/32 |
Configuration Roadmap
The configuration roadmap is as follows:
Configure basic user access functions and ensure that the two NetEngine 8000 Fs have the same configuration. For details, see HUAWEI NetEngine 8000 F Series Router Configuration Guide - User Access.
Configure routes to ensure IP connectivity between devices. For details, see HUAWEI NetEngine 8000 F Series Router Configuration Guide - IP Routing.
Establish a dual-device backup platform.
Configure an RBS, address pools, and an RBP.
Configure a protection path for returned network-side traffic.
Bind an RBP to an interface from which the user goes online.
- Configure EDSG services on Device A and Device B. For details, see HUAWEI NetEngine 8000 F Series Router Multiservice Control Gateway Configuration Guide - Value-added Service.
Data Preparation
To complete the configuration, you need the following data:
VRRP ID
Interface IP addresses of routers that back up each other
Backup ID, which is used together with an RBS to identify the RBP to which the user belongs
Address pool names
EDSG-related parameters
Procedure
- Establish a dual-device backup platform. The configuration on Device A is used as an example. The configuration on Device B is similar to that on Device A.

In this example, only RUI-related configuration is described.
# Configure a BFD session on the access side to rapidly detect faults in interfaces or links and trigger a master/backup VRRP switchover. 10.0.1.2 is the IP address of GE 0/1/0.2 on Device B.
[*DeviceA] bfd [*DeviceA] commit [~DeviceA-bfd] quit [*DeviceA] bfd bfd bind peer-ip 10.0.1.2 [*DeviceA-bfd-session-bfd] discriminator local 1 [*DeviceA-bfd-session-bfd] discriminator remote 2 [*DeviceA-bfd-session-bfd] commit [~DeviceA-bfd-session-bfd] quit
# Configure a VRRP group on GE 0/1/0.2, and configure the VRRP group to track the BFD session and network-side interface.
[*DeviceA] interface gigabitethernet 0/1/0.2 [*DeviceA-GigabitEthernet0/1/0.2] vlan-type dot1q 200 [*DeviceA-GigabitEthernet0/1/0.2] ip address 10.0.1.1 255.255.255.0 [*DeviceA-GigabitEthernet0/1/0.2] vrrp vrid 1 virtual-ip 10.0.1.100 [*DeviceA-GigabitEthernet0/1/0.2] admin-vrrp vrid 1 [*DeviceA-GigabitEthernet0/1/0.2] vrrp vrid 1 priority 120 [*DeviceA-GigabitEthernet0/1/0.2] vrrp vrid 1 preempt-mode timer delay 600 [*DeviceA-GigabitEthernet0/1/0.2] vrrp vrid 1 track bfd-session 1 peer [*DeviceA-GigabitEthernet0/1/0.2] vrrp vrid 1 track interface gigabitethernet 2/0/0 reduced 50 [*DeviceA-GigabitEthernet0/1/0.2] vrrp recover-delay 20 [*DeviceA-GigabitEthernet0/1/0.2] commit [~DeviceA-GigabitEthernet0/1/0.2] quit

Different priorities must be configured for devices in a VRRP group. The device with a higher priority is the master device.
- Configure an RBS, address pools, and an RBP.
# Configure an RBS.
[*DeviceA] remote-backup-service service1 [*DeviceA-rm-backup-srv-service1] peer 88.88.88.88 source 22.22.22.22 port 2046 [*DeviceA-rm-backup-srv-service1] track interface gigabitethernet 0/1/8 [*DeviceA-rm-backup-srv-service1] commit [~DeviceA-rm-backup-srv-service1] quit

You can run the track bfd-session command in the RBS view to track the peer BFD sessions established on the network side of the master and backup devices, achieving rapid peer status detection. For configuration details, see the corresponding command reference.
# Configure a primary address pool named hsi and a backup address pool named hsi-main-bak on Device A (master device).[*DeviceA] ip pool hsi bas local [*DeviceA-ip-pool-hsi] gateway 1.1.1.1 24 [*DeviceA-ip-pool-hsi] section 0 1.1.1.2 1.1.1.254 [*DeviceA-ip-pool-hsi] commit [~DeviceA-ip-pool-hsi] quit [*DeviceA] ip pool hsi-main-bak bas local [*DeviceA-ip-pool-hsi-main-bak] gateway 2.2.2.2 24 [*DeviceA-ip-pool-hsi-main-bak] section 0 2.2.2.3 2.2.2.254 [*DeviceA-ip-pool-hsi-main-bak] commit [~DeviceA-ip-pool-hsi-main-bak] quit
# Configure a primary address pool named hsi-main and a backup address pool named hsi-bak on Device B.
[*DeviceB] ip pool hsi-main bas local [*DeviceB-ip-pool-hsi-main] gateway 2.2.2.2 24 [*DeviceB-ip-pool-hsi-main] section 0 2.2.2.3 2.2.2.254 [*DeviceB-ip-pool-hsi-main] commit [~DeviceB-ip-pool-hsi-main] quit [*DeviceB] ip pool hsi-bak bas local rui-slave [*DeviceB-ip-pool-hsi-bak] gateway 1.1.1.1 24 [*DeviceB-ip-pool-hsi-bak] section 0 1.1.1.2 1.1.1.254 [*DeviceB-ip-pool-hsi-bak] commit [~DeviceB-ip-pool-hsi-bak] quit
# Configure an RBP on Device A and Device B.
[*DeviceA] remote-backup-profile profile1 [*DeviceA-rm-backup-prf-profile1] peer-backup hot [*DeviceA-rm-backup-prf-profile1] vrrp-id 1 interface gigabitethernet 0/1/0.2 [*DeviceA-rm-backup-prf-profile1] backup-id 10 remote-backup-service service1 [*DeviceA-rm-backup-prf-profile1] service-type bras [*DeviceA-rm-backup-prf-profile1] commit [~DeviceA-rm-backup-prf-profile1] quit
[*DeviceB] remote-backup-profile profile1
[*DeviceB-rm-backup-prf-profile1] peer-backup hot
[*DeviceB-rm-backup-prf-profile1] vrrp-id 1 interface gigabitethernet 0/1/0.2
[*DeviceB-rm-backup-prf-profile1] backup-id 10 remote-backup-service service1
[*DeviceB-rm-backup-prf-profile1] service-type bras
[*DeviceB-rm-backup-prf-profile1] ip-pool hsi include hsi-bak node 5
[*DeviceB-rm-backup-prf-profile1] ip-pool hsi-main include hsi-main-bak node 10
[*DeviceB-rm-backup-prf-profile1] commit
[~DeviceB-rm-backup-prf-profile1] quit
- Bind the configured address pools to the RBS and configure a protection path for returned network-side traffic.
[*DeviceA] remote-backup-service service1 [*DeviceA-rm-backup-srv-service1] ip-pool hsi [*DeviceA-rm-backup-srv-service1] ip-pool hsi-bak [*DeviceA-rm-backup-srv-service1] protect redirect ip-nexthop 10.1.1.7 interface gigabitethernet 0/1/16 [*DeviceA-rm-backup-srv-service1] commit
[*DeviceB] remote-backup-service service1
[*DeviceB-rm-backup-srv-service1] ip-pool hsi-main
[*DeviceB-rm-backup-srv-service1] ip-pool hsi-bak
[*DeviceB-rm-backup-srv-service1] protect redirect ip-nexthop 10.1.1.6 interface gigabitethernet 0/1/16
[*DeviceA-rm-backup-srv-service1] commit
- Bind the RBP to GE 0/1/0.1 from which users go online. The configuration on Device A is used as an example. The configuration on Device B is similar to that on Device A.
[~DeviceA] interface gigabitethernet 0/1/0 [*A-GigabitEthernet0/1/0.1] remote-backup-profile profile1 [*DeviceA-rm-backup-srv-service1] commit [~A-GigabitEthernet0/1/0.1] quit
- Configure EDSG services.
- Verify the configuration.
After successfully configuring the RBP, run the display remote-backup-profile command. According to the command output, the RBS type is bras, the RBP named profile1 is bound to GigabitEthernet 0/1/0.1 from which users go online, and Device A is in the Master state.
<~DeviceA> display remote-backup-profile profile1 ----------------------------------------------- Profile-Index : 0x803 Profile-Name : profile1 Service : bras Remote-backup-service: service1 Backup-ID : 10 track protocol : VRRP VRRP-ID : 1 VRRP-Interface : GigabitEthernet0/1/0.2 Interface : GigabitEthernet0/1/0.1 State : Master Peer-state : Slave Backup mode : hot Slot-Number : 1 Card-Number : 0 Port-Number : 0 IP-Pool : hsi Traffic threshold : 50(MB) Traffic interval : 10(minutes) <~DeviceB> display remote-backup-profile profile1 ----------------------------------------------- Profile-Index : 0x803 Profile-Name : profile1 Service : bras Remote-backup-service: service1 Backup-ID : 10 track protocol : VRRP VRRP-ID : 1 VRRP-Interface : GigabitEthernet0/1/0.2 Interface : GigabitEthernet0/1/0.1 State : Slave Peer-state : Master Backup mode : hot Slot-Number : 1 Card-Number : 0 Port-Number : 0 IP-Pool : hsi Traffic threshold : 50(MB) Traffic interval : 10(minutes)
After successfully configuring the RBS, run the display remote-backup-service command. According to the command output, the TCP connection is in the Connected state.
<~DeviceA> display remote-backup-service service1 ---------------------------------------------------------- Service-Index : 0 Service-Name : service1 TCP-State : Connected Peer-ip : 88.88.88.88 Source-ip : 22.22.22.22 TCP-Port : 2046 Track-BFD : -- Track-interface0 : GigabitEthernet0/1/8 Track-interface1 : -- ---------------------------------------------------------- ip pool: hsi metric 10 hsi-bak metric 10 ipv6 pool: NAT instance : nat1 ---------------------------------------------------------- Rbs-ID : 0 Protect-type : ip-redirect Next-hop : 10.1.1.7 Vlanid : 0 Peer-ip : 10.1.1.7 Vrfid : 0 Tunnel-index : 0x0 Tunnel-state : UP Tunnel-OperFlag: NORMAL Spec-interface : GigabitEthernet0/1/16 Out-interface : GigabitEthernet0/1/16 User-number : 0
After users go online, run the display backup-user command to view user information that is backed up.
<~DeviceA> display backup-user Remote-backup-service: service1 Total Users Numer: 10 ------------------------------------------------------------------------ 100 101 102 103 104 105 106 107 108 109 ------------------------------------------------------------------------
Run the display access-user interface command to view online user information on a specified interface.
<~DeviceA> display access-user interface GigabitEthernet 0/1/0.1 ------------------------------------------------------------------------------ UserID Username Interface IP address MAC Vlan IPv6 address Access type ------------------------------------------------------------------------------ 120 user@lsh GE0/1/0.1 2.2.2.10 00e0-fc12-0101 50/- - IPoE 101 user@lsh GE0/1/0.1 2.2.2.9 00e0-fc12-0102 - 50/- - IPoE 102 user@lsh GE0/1/0.1 2.2.2.8 00e0-fc12-0103 - 50/- - IPoE 103 user@lsh GE0/1/0.1 2.2.2.7 00e0-fc12-0104 - 50/- - IPoE 104 user@lsh GE0/1/0.1 2.2.2.6 00e0-fc12-0105 - 50/- - IPoE 105 user@lsh GE0/1/0.1 2.2.2.5 00e0-fc12-0106 - 50/- - IPoE 106 user@lsh GE0/1/0.1 2.2.2.4 00e0-fc12-0107 - 50/- - IPoE 107 user@lsh GE0/1/0.1 2.2.2.3 00e0-fc12-0108 - 50/- - IPoE 108 user@lsh GE0/1/0.1 2.2.2.2 00e0-fc12-0109 - 50/- - IPoE 109 user@lsh GE0/1/0.1 2.2.2.11 00e0-fc12-0110 - 50/- - IPoE -------------------------------------------------------------------------- Normal users : 0 RUI Local users : 10 RUI Remote users : 0 Total users : 10
View the configuration of the EDSG service policy on Device A.
<DeviceA> display service-policy configuration name service_edsg1 ------------------------------------------------ Service-policy-index : 0 Service-policy-name : service1 Service-policy-type : EDSG Policy-storage-type : configuration Reference-count : 0 Service-class-inbound :ef Service-class-outbound :ef Authentication-scheme-name : - Accounting-scheme-name : default1 Radius-server-template : template1 Service-group-name : - Service-group-priority : - Inbound-cir : 100(kbps) Inbound-pir : 100(kbps) Inbound-cbs : 100(bytes) Inbound-pbs : 3000(bytes) Outbound-cir : 10000(kbps) Outbound-pir : - Outbound-cbs : - Outbound-pbs : - Prepaid-profile-name : - Diameter monitor key : - Inbound-match-usergroup : no Outbound-match-usergroup : no ------------------------------------------------
Configuration Files
Device A configuration file
# sysname DeviceA # ip pool hsi bas local gateway 1.1.1.1 255.255.255.0 section 0 1.1.1.2 1.1.1.254 # ip pool hsi-main-bak bas local rui-slave gateway 2.2.2.2 255.255.255.0 section 0 2.2.2.3 2.2.2.254 # aaa domain userdomain1 authentication-scheme default0 accounting-scheme default0 ip-pool hsi ip-pool hsi-main-bak # bfd bfd bind peer-ip 10.0.1.2 discriminator local 1 discriminator remote 2 commit # interface gigabitethernet 0/1/0.2 vlan-type dot1q 200 ip address 10.0.1.1 255.255.255.0 vrrp vrid 1 virtual-ip 10.0.1.100 admin-vrrp vrid 1 vrrp vrid 1 priority 120 vrrp vrid 1 preempt-mode timer delay 600 vrrp vrid 1 track bfd-session 1 peer vrrp vrid 1 track interface gigabitethernet 0/1/8 reduced 50 vrrp recover-delay 20 # remote-backup-service service1 peer 88.88.88.88 source 22.22.22.22 port 2046 track interface gigabitethernet 0/1/8 ip-pool hsi ip-pool hsi-main-bak protect redirect ip-nexthop 10.1.1.7 interface gigabitethernet 0/1/16 # remote-backup-profile profile1 service-type bras backup-id 10 remote-backup-service service1 peer-backup hot vrrp-id 1 interface gigabitethernet 0/1/0.2 # interface gigabitethernet 0/1/0.1 user-vlan 50 remote-backup-profile profile1 bas access-type layer2-subscriber authentication-method web vlan-type dot1q 1 ip address 192.168.100.1 255.255.255.0 # interface gigabitethernet 0/1/16 undo shutdown ip address 10.1.1.6 255.255.255.0 # value-added-service enable # radius-server group rad_group1 radius-server authentication 10.10.10.2 1812 weight 0 radius-server accounting 10.10.10.2 1813 weight 0 radius-server shared-key-cipher %^%#x*CgITP4C~;q,*+DEW'JBWe#)"Q&|7bX]b:Y<{w'%^%# # ip pool edsg_pool bas local gateway 172.32.0.0 255.255.0.0 section 0 172.32.0.0 172.32.255.255 # aaa authentication-scheme auth1 authentication-scheme radius accounting-scheme acct1 accounting-mode radius domain domain1 ip-pool edsg_pool radius-server group rad_group1 # service-group s_1m service-group s_2m # acl number 6020 rule 10 permit ip source service-group s_1m destination ip-address 192.168.100.0 0.0.0.255 rule 20 permit ip source ip-address 192.168.100.0 0.0.0.255 destination service-group s_1m # acl number 6021 rule 15 permit ip source service-group s_2m destination ip-address 192.168.200.0 0.0.0.255 rule 25 permit ip source ip-address 192.168.200.0 0.0.0.255 destination service-group s_2m # traffic classifier c1 operator or if-match acl 6020 # traffic classifier c2 operator or if-match acl 6021 # traffic behavior b1 # traffic behavior b2 # traffic policy traffic_policy_edsg share-mode classifier c1 behavior b1 classifier c2 behavior b2 # traffic-policy traffic_policy_edsg inbound traffic-policy traffic_policy_edsg outbound # aaa authentication-scheme auth1 # accounting-scheme acct1 # # http-redirect-profile http_redirect_profile web-server url http://www.sample.com web-server mode post # prepaid-profile prepaid1 password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81fv"uMoKKZ.1k"`AO!X2K2N.b~'NB^V!!!!!!!!!!1!!!!o/4J(q"J1F.!K9%M!6x8%@%# authentication-scheme auth1 accounting-scheme acct1 radius-server group rad_group1 threshold time 60 seconds threshold volume 10 mbytes # prepaid-profile prepaid2 password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81fv"uMoKKZ.1k"`AO!X2K2N.b~'NB^V!!!!!!!!!!1!!!!o/4J(q"J1F.!K9%M!6x8%@%# authentication-scheme auth1 accounting-scheme acct1 radius-server group rad_group1 threshold time 300 seconds threshold volume 20 mbytes quota-out redirect http_redirect_profile # service-policy download local radius rad_group1 password cipher huawei_123 # service-policy name service_edsg1 edsg radius-server group rad_group1 service-group s_1m authentication-scheme auth1 accounting-scheme acct1 rate-limit cir 1000 inbound rate-limit cir 1000 outbound prepaid-profile prepaid1 # service-policy name service_edsg2 edsg radius-server group rad_group1 service-group s_2m authentication-scheme auth1 accounting-scheme acct1 rate-limit cir 2000 inbound rate-limit cir 2000 outbound prepaid-profile prepaid2 # interface GigabitEthernet0/1/2.1 user-vlan 1000 2000 user-vlan 1 1000 qinq 100 bas # access-type layer2-subscriber default-domain pre-authentication domain1 authentication-method ppp web # return
Device B configuration file
# sysname DeviceB # ip pool hsi-main bas local gateway 2.2.2.2 255.255.255.0 section 0 2.2.2.3 2.2.2.253 # ip pool hsi-bak bas local rui-slave gateway 1.1.1.1 255.255.255.0 # LOCAL section 0 1.1.1.2 1.1.1.253 # REMOTE dhcp-server group gm1 # aaa domain userdomain1 authentication-scheme default0 accounting-scheme default0 # bfd bfd bind peer-ip 10.0.1.1 discriminator local 2 discriminator remote 1 commit # interface gigabitethernet 0/1/0.2 vlan-type dot1q 200 ip address 10.0.1.2 255.255.255.0 vrrp vrid 1 virtual-ip 10.0.1.100 admin-vrrp vrid 1 vrrp vrid 1 track bfd-session 2 peer vrrp vrid 1 track interface gigabitethernet 0/1/8 reduced 50 # remote-backup-service service1 peer 22.22.22.22 source 88.88.88.88 port 2046 track interface gigabitethernet 0/1/8 ip-pool hsi-main ip-pool hsi-bak protect redirect ip-nexthop 10.1.1.6 interface gigabitethernet 0/1/16 # remote-backup-profile profile1 peer-backup hot service-type bras backup-id 10 remote-backup-service service1 peer-backup hot vrrp-id 1 interface gigabitethernet 0/1/0.2 ip-pool hsi include hsi-main node 5 ip-pool hsi include hsi-bak node 10 # interface gigabitethernet 0/1/0.1 user-vlan 50 remote-backup-profile profile1 bas access-type layer2-subscriber authentication-method web vlan-type dot1q 1 ip address 192.168.100.1 255.255.255.0 # interface gigabitethernet 0/1/16 undo shutdown ip address 10.1.1.7 255.255.255.0 # value-added-service enable # radius-server group rad_group1 radius-server authentication 10.10.10.2 1812 weight 0 radius-server accounting 10.10.10.2 1813 weight 0 radius-server shared-key-cipher %^%#x*CgITP4C~;q,*+DEW'JBWe#)"Q&|7bX]b:Y<{w'%^%# # ip pool edsg_pool bas local gateway 172.32.0.0 255.255.0.0 section 0 172.32.0.0 172.32.255.255 # aaa authentication-scheme auth1 authentication-scheme radius accounting-scheme acct1 accounting-mode radius domain domain1 ip-pool edsg_pool radius-server group rad_group1 # service-group s_1m service-group s_2m # acl number 6020 rule 10 permit ip source service-group s_1m destination ip-address 192.168.100.0 0.0.0.255 rule 20 permit ip source ip-address 192.168.100.0 0.0.0.255 destination service-group s_1m # acl number 6021 rule 15 permit ip source service-group s_2m destination ip-address 192.168.200.0 0.0.0.255 rule 25 permit ip source ip-address 192.168.200.0 0.0.0.255 destination service-group s_2m # traffic classifier c1 operator or if-match acl 6020 # traffic classifier c2 operator or if-match acl 6021 # traffic behavior b1 # traffic behavior b2 # traffic policy traffic_policy_edsg share-mode classifier c1 behavior b1 classifier c2 behavior b2 # traffic-policy traffic_policy_edsg inbound traffic-policy traffic_policy_edsg outbound # aaa authentication-scheme auth1 # accounting-scheme acct1 # # http-redirect-profile http_redirect_profile web-server url http://www.sample.com web-server mode post # prepaid-profile prepaid1 password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81fv"uMoKKZ.1k"`AO!X2K2N.b~'NB^V!!!!!!!!!!1!!!!o/4J(q"J1F.!K9%M!6x8%@%# authentication-scheme auth1 accounting-scheme acct1 radius-server group rad_group1 threshold time 60 seconds threshold volume 10 mbytes # prepaid-profile prepaid2 password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81fv"uMoKKZ.1k"`AO!X2K2N.b~'NB^V!!!!!!!!!!1!!!!o/4J(q"J1F.!K9%M!6x8%@%# authentication-scheme auth1 accounting-scheme acct1 radius-server group rad_group1 threshold time 300 seconds threshold volume 20 mbytes quota-out redirect http_redirect_profile # service-policy download local radius rad_group1 password cipher %@%##!!!!!!!!!"!!!!"!!!!(!!!!1];16qfZ81fv"uMoKKZ.1k"`AO!X2K2N.b~'NB^V!!!!!!!!!!1!!!!o/4J(q"J1F.!K9%M!6x8%@%# # service-policy name service_edsg1 edsg radius-server group rad_group1 service-group s_1m authentication-scheme auth1 accounting-scheme acct1 rate-limit cir 1000 inbound rate-limit cir 1000 outbound prepaid-profile prepaid1 # service-policy name service_edsg2 edsg radius-server group rad_group1 service-group s_2m authentication-scheme auth1 accounting-scheme acct1 rate-limit cir 2000 inbound rate-limit cir 2000 outbound prepaid-profile prepaid2 # interface GigabitEthernet0/1/2.1 user-vlan 1000 2000 user-vlan 1 1000 qinq 100 bas # access-type layer2-subscriber default-domain pre-authentication domain1 authentication-method ppp web # return