Architecture
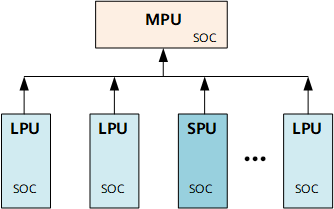
Each board on the NetEngine 8000 F has an independent Security Operating Center (SOC) that is responsible for collecting statistics and packet summaries on the board. Figure 1 shows the SOC deployment.
The SOC runs automatically when the system starts, intelligently monitors system security in real time, and traces and locates the source of attacks. After detecting an attack, the SOC outputs an attack report.
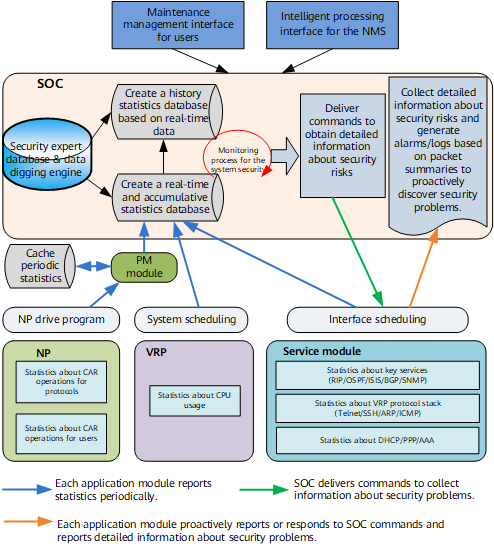
Figure 2 shows the SOC architecture.
As shown in Figure 2, the network processor (NP) implements traffic classification for packets sent to the CPU. Packets of different types enter different queues with different CAR parameters. The NP collects statistics about dropped packets and packets sent to the CPU. The PM module periodically reads all CP-CAR statistics and saves them in the buffer.
The SOC periodically reads the following information from the PM module:
- CP-CAR statistics
- CPU usage and statistics
- Service statistics
After detecting an attack, the SOC initially determines the attack source and then samples suspicious packets for analysis.
Based on the analysis, the SOC locates the source of the attack and identifies its cause, and outputs attack reports.
The SOC provides interfaces for other modules to report security problems. After detecting an attack, a module proactively outputs information to the SOC.