SOC Processing
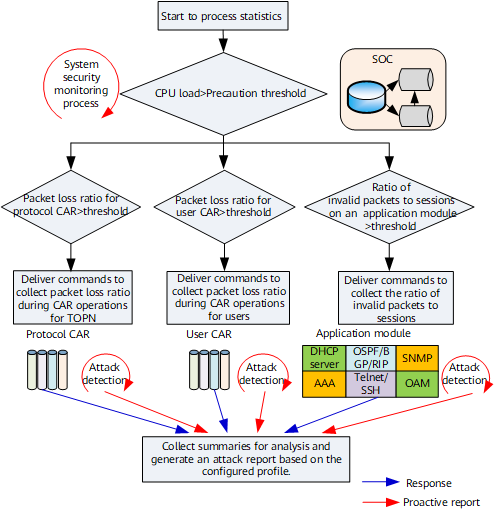
Figure 1 shows the attack detection and tracing process.
- The SOC periodically obtains security-related system statistics, including packet loss caused by CP-CAR, CPU load, and service availability on each application module.
- The SOC works with the attack detection module to determine whether the system is under attack. If there is no attack, the SOC continues to collect statistics. If there is an attack, the SOC starts the attack source tracing process to locate the source of the attack.
- The SOC outputs a preliminary conclusion about the attack source to the module collecting packet summaries. After this module discovers suspicious attack packets, the SOC saves information about these packets in the database.
- After sampling packets, the SOC analyzes statistics and outputs attack reports based on the configured profile that describes how to identify an attack.
- The SOC delivers a policy to isolate or defend the attack based on users' requirements.