Basic Concepts of 802.1X Port-based Authentication
802.1X Port-based Authentication Architecture
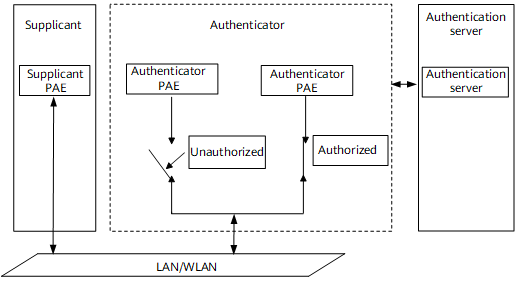
As shown in Figure 1, the three major components of the 802.1x authentication system are the supplicant, authenticator, and authentication server.
The supplicant is a user terminal that requests access to a local area network (LAN), and is authenticated by an authenticator in the LAN. A user initiates 802.1X authentication by starting the supplicant software. The supplicant must support the Extensible Authentication Protocol over LAN (EAPOL).
The authenticator is a network device that controls supplicant access to the LAN. It is located between the supplicant and the authentication server. It provides a port for the supplicant to access the LAN and authenticates the connected supplicant through the interaction with the authentication server.
The authentication server undertakes authentication, authorization, and accounting for users. You are recommended to use a RADIUS server as the authentication server.
Access Authorization Mode
When deploying 802.1X port-based authentication, configure an access authorization mode on the NetEngine 8000 F to determine whether to authenticate users on a port before they can access network resources. The NetEngine 8000 F supports the following access authorization modes:
- Automatic identification: The port is initially in the unauthorized state and allows only users' EAPOL packets to pass through. It does not allow users to access network resources. After the users pass 802.1X authentication, the port switches to the authorized state, and the users can access network resources.
- Forcible authorization: The port remains in the authorized state and allows users to access network resources without being authenticated or authorized.
- Forcible unauthorization: The port remains in the unauthorized state and prohibits users from accessing network resources. This mode applies to scenarios where all users connected to a port need to be disabled from accessing network resources due to security considerations.
Port Authorization State
The Port Access Entity (PAE) of the authenticator determines the authorized or unauthorized state of a controlled port according to the instruction (Accept or Reject) of the RADIUS server. As shown in Figure 1, the access rights of the controlled port depends on its authorization state.
- Authorized: After a user or device passes the 802.1X authentication, the port to which the user or device is connected is in the authorized state. In the authorized state, other data of the user or device can also pass through the Ethernet interface. This mechanism improves network security by allowing only authorized users or devices to access the network.
- Unauthorized: Before a user or device passes the 802.1X authentication, the port to which the user or device is connected is in the unauthorized state. Controlled ports in the unauthorized state will deny the user or device access. Before authentication is successful, only EAPOL packets are allowed to pass through.
Access Control Mode
The NetEngine 8000 F supports the following access control modes for 802.1X port-based authentication.
- Port-based access control: After the first user is authenticated, subsequent users can pass the authentication or access the network without being authenticated. When the first user goes offline, other users are denied access to network resources. This authentication mode applies to group users.
MAC-based authentication: Every user accessing a port must be authenticated. If a user goes offline, other 802.1X authenticated users can still access the network.
This authentication mode applies to scattered users.