VLL/PWE3 Scenario
VLL/PWE3 Typical Topology
Figure 1 VLL/PWE3 typical topology
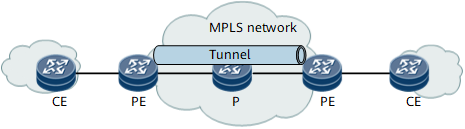

- PE (provider edge): an edge device on the provider network, which is directly connected to the CE. The PE receives traffic from the CE and then encapsulates the traffic with MPLS header, and then sends the traffic to P. The PE also receives traffic from the P and then remove the MPLS header from the traffic, and then sends the traffic to CE.
- P (Provider): a backbone device on the provider network, which is not directly connected to the CE. Ps perform basic MPLS forwarding.
- CE (customer edge): an edge device on the private network.
Suitable Scenario 1: Load Balance on Ingress PE of VLL/PWE3
Figure 2 Route load balance on ingress PE
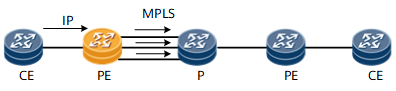

Figure 3 Trunk load balance on ingress PE
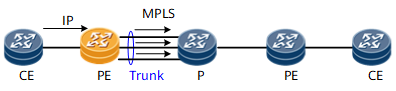

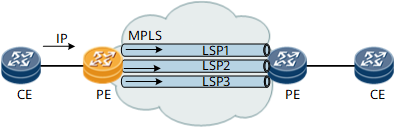
Figure 4 Tunnel load balance on ingress PE

The hash algorithm is performed based on the packet format of the inbound traffic from AC interface.
- IP traffic: the hash factors can be IP 5-tuple or IP 2-tuple. The result of the load balancing depends on the discreteness of the private IP addresses or TCP/UDP ports of the packets.
- Ethernet carrying Non-IP traffic, the hash factors can be MAC 2-tuple. The result of the load balancing depends on the discreteness of the MAC addresses of the packets.
- Non-Ethernet traffic: the hash factor is VC label in most boards.
Suitable Scenario 2: Load Balance on P Nodes
Figure 5 Route load balance on P
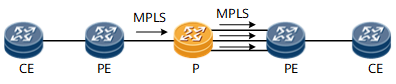

Figure 6 Trunk load balance on P
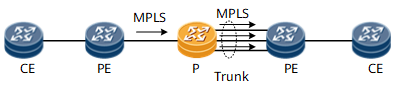

The hash algorithm on P node is performed based on the packet
format of the inbound MPLS traffic.
- If the number of labels in the packet is less than four, the hash factors can be IP 5-tuple or IP 2-tuple. The result of the load balancing depends on the discreteness of the private IP addresses or TCP/UDP ports of the packets.
- In the complex scenarios such as inter-AS VPN, FRR and LDP over TE, the number of the labels may be four or more. In these scenarios, the hash factors are the fourth or fifth label from the top. The result of the load balancing depends on the discreteness of the fourth or fifth label from the top.
Suitable Scenario 3: Load Balance on Egress PE of VLL/PWE3
Figure 7 Load Balance on Egress PE of VLL/PWE3
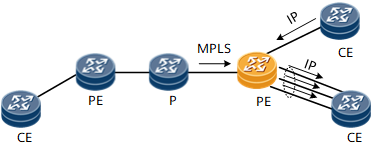

Egress PE of VLL/PWE3 only supports Trunk load balancing because the virtual circuit (VC) of VLL/PWE3 is P2P.
- If the traffic is from AC to AC, the hash algorithm is the same as Scenario 1.
- If the traffic is from MPLS to AC, the hash factors can be IP 5-tuple, IP 2-tuple or VC label. The hash factors may be different in different board-types.
Suitable Scenario 4: Load Balancing Among the L2 Outbound Interfaces in the Access of L2VPN to L3VPN Scenarios
Figure 8 Load Balancing Among the L2 Outbound Interfaces in the Access
of L2VPN to L3VPN Scenarios
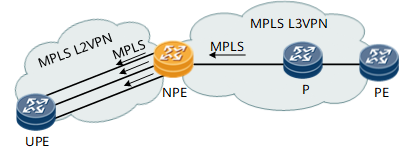

In access of L2VPN to L3VPN scenarios, the hash algorithm is the same as Scenario 1.