IP MTU Fragmentation
IP MTU Fragmentation Implementation
Among the headers of TCP/IP protocols, MTU-related fragmentation fields exist only in the IPv4 header and IPv6 extension header. The NetEngine 8000 F supports MTU fragmentation only in the following situations.
MTU Fragmentation Related Processes |
Process Location |
Notes |
|---|---|---|
Original IPv4 packet sending |
Control plane |
Original IPv4 packets indicate the protocol packets sent from control plane of local device. The source IP address of these IPv4 packets is the local device. Border Gateway Protocol (BGP) packets, Internet Control Message Protocol (ICMP) messages, and bidirectional forwarding detection (BFD) control packets, belong to protocol packets. When the ping command is run on a device, the device sends ICMP request messages. |
Original IPv6 packet sending |
Control plane |
Original IPv6 packets indicate the protocol packets sent from control plane of local device. The source IPv6 address of these IPv6 packets is the local device. When the ping ipv6 command is run on a device, the device sends ICMPv6 request messages. |
IPv4 packet forwarding |
Forwarding plane |
IP fragmentation occurs when the device sends packet, but not when the device receives packet. For NetEngine 8000 F device, the MTU configured in the interface (also called interface MTU) is IP MTU. IP MTU is a layer 3 definition. Therefore, interface MTU only takes effect on Layer 3 traffic, but not on Layer 2 traffic. Even when IP header + IP payload of L2 frame exceeds interface MTU, the L2 frame will not be fragmented. |
NOTE:
Generally, only the source and destination nodes need to analyze the IPv6 extension headers. So fragmentation only occurs on the source node, which is different from IPv4. |
||
Force-fragment
By default, when the IPv4 packet's length is larger than the interface MTU,
- If DF=0, the packet is fragmented.
- If DF=1, the packet cannot be fragmented, and the device drops the packet and return a Packet-too-big message.
NetEngine 8000 F supports force-fragment function. If force-fragment is enabled, the board ignoring DF-bit all IPv4 large packets (size> MTU) will be cut into packets and be forwarded with DF=0.
To enable force-fragment function, run the ipv4 force-fragment enable command.
Force-fragment function is enabled only for IPv4 packets, not for other type packets.
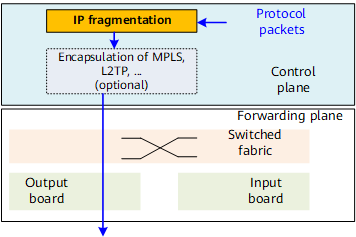
Fragmentation in Control Plane
As shown in Figure 1, the control plane fragments IP packets and then encapsulates them with tunnel headers (such as MPLS and L2TP) if needed before sending the packets to the forwarding plane. Control plane fragmentation is implemented by software. Therefore, the fragmentation rules are the same in different board types.
- If the DF field is set to 0 in a packet, the packet is fragmented. The size of each fragment is less than or equal to the interface MTU.
- If the DF field is set to 1 in a packet, the packet is discarded.
- If the DF field is set to 1 in a packet and the outbound interface is enabled with forcible-fragmentation, the packet is fragmented. Each fragment is forwarded with DF=0. (By default, forcible-fragmentation is not enabled for control plane. To enable forcible-fragmentation for control plane, run the clear ip df command on the outbound interface).
For the information about the fragmentation for MPLS packet, see the chapter MPLS MTU Fragmentation.
- the device is implementing PMTU discover, such as IPv6 PMTU discover, or LDP/RSVP-TE PMTU negotiation.
- the ping -f command is running on the local device.
Fragmentation in Forwarding Plane
Fragmentation in forwarding plane takes effort only on forwarding traffic. Forwarding traffic indicates the traffic passes through the local device, without being sent to the control plane. Forwarding traffic does not include the traffic sent from control plane.
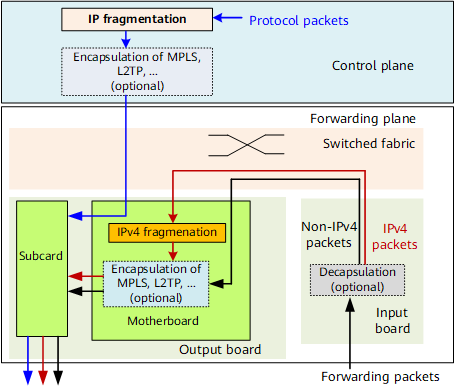
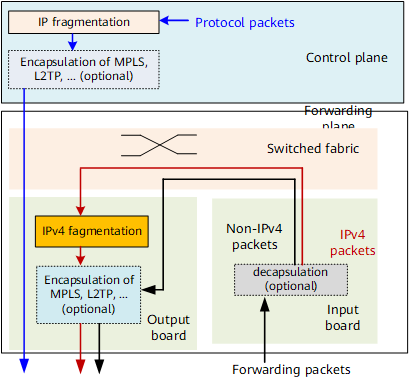
Fragmentation on motherboards or integrated boards:
The fragmentation works only towards the IPv4 traffic to be forwarded (including the IPv4 traffic to be forwarded after decapsulation).
For example, MPLS L3VPN traffic is MPLS-encapsulated before being forwarded from a Network-to-Network Interface (NNI) to a User-to-Network Interface (UNI) on a provider edge (PE) node. PE fragments the traffic after removing MPLS labels.
For another example, in L3VPN and high-speed Internet (HSI) scenarios, if a customer premises equipment (CPE) uses a Dot1q or QinQ termination sub-interface to access a PE, the packet sent from CPE to PE is VLAN tagged. In these scenarios, the packet is also fragmented on the PE after the VLAN tags are removed.
- Fragmentation does not occur during L2 or MPLS forwarding behavior.
- Fragmentation does not occur during IPv6 forwarding.
- Force-fragment (ipv4 force-fragment enable command): By default, when the IPv4 packet's length is larger than the interface MTU, if DF=1, the packet cannot be fragmented, and the device drops the packet and return a Packet-too-big message. If force-fragment is enabled, the board ignoring DF-bit all IPv4 large packets (size> MTU) will be cut into packets and be forwarded with DF=0. Force-fragment function is enabled only for IPv4 packets, not for other type packets.