Example for Configuring BGP Keychain Authentication
By configuring keychain authentication between BGP peers, you can enhance the security of BGP connections.
Networking Requirements
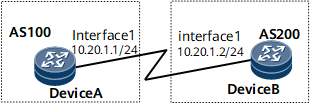
On the network shown in Figure 1, Device A belongs to AS 100, and Device B belongs to AS 200. BGP runs on the network, and BGP keychain authentication is used to protect EBGP connections against attacks.
Precautions
When configuring BGP keychain authentication, pay attention to the following:
You need to configure keychain authentication on both BGP peers, and ensure that encryption algorithms and passwords configured for keychain authentication on both peers are the same. Otherwise, TCP connections cannot be established between BGP peers, and BGP messages cannot be exchanged.
Configuration Roadmap
The configuration roadmap is as follows:
Establish an EBGP connection between Device A and Device B.
Configure keychain authentication on Device A and Device B.
Data Preparation
To complete the configuration, you need the following data:
Router IDs and AS numbers of Device A and Device B
Name of keychain authentication between Device A and Device B
Procedure
- Configure an IP address for each interface. For configuration details, see Configuration Files in this section.
- Establish an EBGP connection.
# Configure Device A.
[~DeviceA] bgp 100 [*DeviceA-bgp] router-id 1.1.1.1 [*DeviceA-bgp] peer 10.20.1.2 as-number 200 [*DeviceA-bgp] commit [~DeviceA-bgp] quit
# Configure Device B.
[~DeviceB] bgp 200 [*DeviceB-bgp] router-id 2.2.2.2 [*DeviceB-bgp] peer 10.20.1.1 as-number 100 [*DeviceB-bgp] commit [~DeviceB-bgp] quit
- Configure keychain authentication.
# Configure Device A.
[~DeviceA] keychain Huawei mode absolute [*DeviceA-keychain] tcp-kind 179 [*DeviceA-keychain] tcp-algorithm-id hmac-sha-256 17 [*DeviceA-keychain] receive-tolerance 100 [*DeviceA-keychain] key-id 1 [*DeviceA-keychain-keyid-1] algorithm hmac-sha-256 [*DeviceA-keychain-keyid-1] key-string hello [*DeviceA-keychain-keyid-1] send-time 11:00 2009-12-24 to 12:00 2009-12-24 [*DeviceA-keychain-keyid-1] receive-time 11:00 2009-12-24 to 12:00 2009-12-24 [*DeviceA-keychain-keyid-1] commit [~DeviceA-keychain-keyid-1] quit [~DeviceA-keychain] quit
# Configure Device B.
[~DeviceB] keychain Huawei mode absolute [*DeviceB-keychain] tcp-kind 179 [*DeviceB-keychain] tcp-algorithm-id hmac-sha-256 17 [*DeviceB-keychain] receive-tolerance 100 [*DeviceB-keychain] key-id 1 [*DeviceB-keychain-keyid-1] algorithm hmac-sha-256 [*DeviceB-keychain-keyid-1] key-string hello [*DeviceB-keychain-keyid-1] send-time 11:00 2009-12-24 to 12:00 2009-12-24 [*DeviceB-keychain-keyid-1] receive-time 11:00 2009-12-24 to 12:00 2009-12-24 [*DeviceB-keychain-keyid-1] commit [~DeviceB-keychain-keyid-1] quit [~DeviceB-keychain] quit
- Apply keychain authentication on the EBGP connection between Device A and Device B.
# Configure Device A.
[~DeviceA] bgp 100 [*DeviceA-bgp] peer 10.20.1.2 keychain Huawei [*DeviceA-bgp] commit [~DeviceA-bgp] quit
# Configure Device B.
[*DeviceB] bgp 200 [*DeviceB-bgp] peer 10.20.1.1 keychain Huawei [*DeviceB-bgp] commit [~DeviceB-bgp] quit
- Verify the configuration.
# On Device A, check the BGP connection status after keychain authentication is configured.
<DeviceA> display bgp peer BGP local router ID : 10.20.1.1 Local AS number : 100 Total number of peers : 1 Peers in established state : 1 Peer V AS MsgRcvd MsgSent OutQ Up/Down State PrefRcv 10.20.1.2 4 200 21 24 0 00:00:23 Established 0You can view that the status of the BGP connection is Established after keychain authentication is configured.
Configuration Files
Device A configuration file
# sysname DeviceA # keychain Huawei mode absolute receive-tolerance 100 tcp-kind 179 tcp-algorithm-id hmac-sha-256 17 # key-id 1 algorithm hmac-sha-256 key-string cipher %#%#e^1}%%w;/C[M)OQc7"j+,2)}%#%# send-time 11:00 2009-12-24 to 12:00 2009-12-24 receive-time 11:00 2009-12-24 to 12:00 2009-12-24 # interface GigabitEthernet0/1/0 undo shutdown ip address 10.20.1.1 255.255.255.0 # bgp 100 router-id 1.1.1.1 peer 10.20.1.2 as-number 200 peer 10.20.1.2 keychain Huawei # ipv4-family unicast undo synchronization peer 10.20.1.2 enable # return
Device B configuration file
# sysname DeviceB # keychain Huawei mode absolute receive-tolerance 100 tcp-kind 179 tcp-algorithm-id hmac-sha-256 17 # key-id 1 algorithm hmac-sha-256 key-string cipher %#%#ub(70WJ"^=i(kxPK@*fK,)}t%#%# send-time 11:00 2009-12-24 to 12:00 2009-12-24 receive-time 11:00 2009-12-24 to 12:00 2009-12-24 # interface GigabitEthernet0/1/0 undo shutdown ip address 10.20.1.2 255.255.255.0 # bgp 200 router-id 2.2.2.2 peer 10.20.1.1 as-number 100 peer 10.20.1.1 keychain Huawei # ipv4-family unicast undo synchronization peer 10.20.1.1 enable # return