Application of Bit-Error-Triggered Protection Switching in a Scenario in Which TE Tunnels Carry an IP RAN
Networking Description
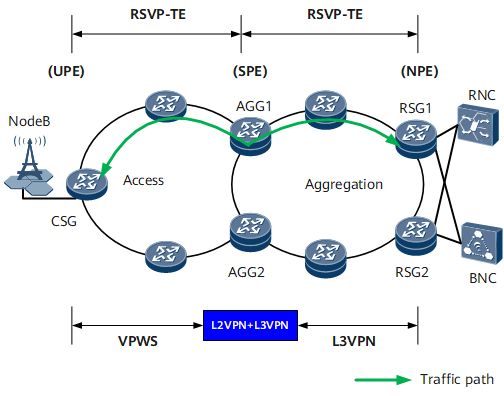
Figure 1 shows typical L2VPN+L3VPN networking in an IP RAN application. A VPWS based on an RSVP-TE tunnel is deployed at the access layer, an L3VPN based on an RSVP-TE tunnel is deployed at the aggregation layer, and L2VPN access to L3VPN is configured on the AGGs. To ensure reliability, deploy PW redundancy for the VPWS, configure VPN FRR protection for the L3VPN, and configure hot-standby protection for the RSVP-TE tunnels.
Feature Deployment
To prevent the impact of bit errors on services, deploy bit-error-triggered RSVP-TE tunnel switching, bit-error-triggered PW switching, and bit-error-triggered L3VPN route switching in the scenario shown in Figure 1. The deployment process is as follows:
Enable trigger-LSP bit error detection on each interface.
Bit-error-triggered RSVP-TE tunnel switching: Enable bit-error-triggered protection switching on the RSVP-TE tunnel interfaces of the CSG and AGG1, and configure thresholds for bit-error-triggered RSVP-TE tunnel switching.
Bit-error-triggered PW switching: Enable bit-error-triggered PW switching on the interfaces that connect the CSG and AGG1 and the interfaces that connect the CSG and AGG2.
Bit-error-triggered L3VPN route switching: Configure bit-error-triggered L3VPN route switching in the VPNv4 view of AGG1.
Bit-Error-Triggered Protection Switching Scenarios
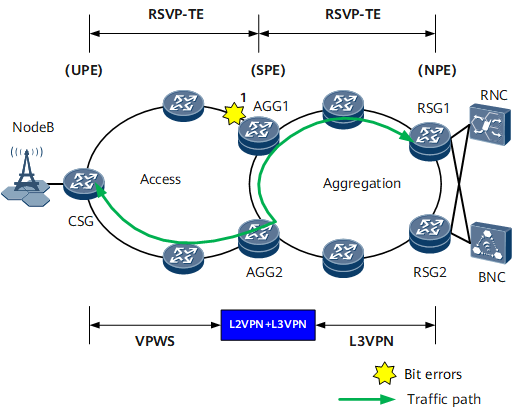
Scenario 1
On the network shown in Figure 2, if bit errors occur on location 1, the RSVP-TE tunnel between the CSG and AGG1 detects the bit errors, triggering dual-ended switching. Both upstream and downstream traffic are switched to the hot-standby path, preventing traffic from passing through the link with bit errors.
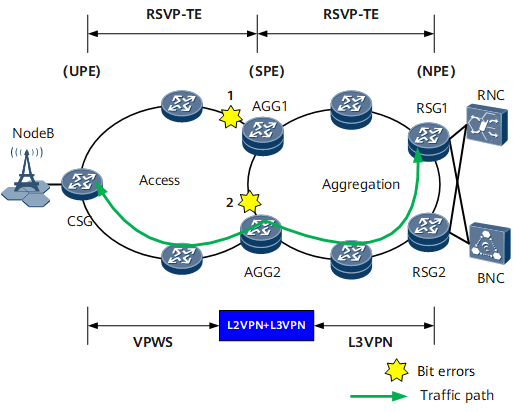
Scenario 2
On the network shown in Figure 3, if bit errors occur on both locations 1 and 2, both the primary and secondary links of the RSVP-TE tunnel between the CSG and AGG1 detect the bit errors. In this case, bit-error-triggered RSVP-TE tunnel switching cannot protect services against bit errors. The bit errors further trigger PW and L3VPN route switching.
After detecting the bit errors, the CSG performs a primary/secondary PW switchover and switches upstream traffic to AGG2.
After detecting the bit errors, AGG1 reduces the priority of VPNv4 routes advertised to RSG1, so that RSG1 preferentially selects VPNv4 routes advertised by AGG2. Downstream traffic is then switched to AGG2.