Example for Configuring IPv4 NFVI Distributed Gateway
This section provides an example for configuring IPv4 NFVI distributed gateway in a typical usage scenario.
Networking Requirements
Huawei's NFVI telecommunications (telco) cloud is a networking solution that incorporates Data Center Interconnect (DCI) and data center network (DCN) technologies. Mobile phone IPv4 traffic enters the DCN and accesses its virtualized unified gateway (vUGW) and virtual multiservice engine (vMSE). After being processed by these, the phone traffic is forwarded over the Internet through the DCN to the destination devices. Equally, response traffic sent over the Internet from the destination devices to the mobile phones also undergoes this process. For this to take place and to ensure that the traffic is balanced within the DCN, you need to deploy the NFVI distributed gateway function on the DCN.

Interfaces 1 through 5 in this example represent GE 0/1/1, GE 0/1/2, GE 0/1/3, GE 0/1/4, and GE 0/1/5, respectively.
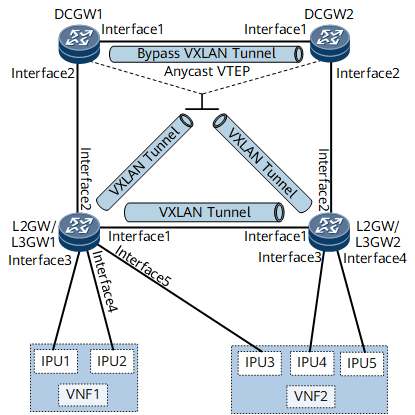
Figure 1 shows the network on which the NFVI distributed gateway function is deployed. DCGW1 and DCGW2 are the DCN's border gateways. The DCGWs exchange Internet routes with the external network. L2GW/L3GW1 and L2GW/L3GW2 access the virtualized network functions (VNFs). As virtualized NEs, VNF1 and VNF2 can be deployed separately to implement the functions of the vUGW and vMSE. VNF1 and VNF2 are connected to L2GW/L3GW1 and L2GW/L3GW2 through respective interface process units (IPUs).
The EVPN VXLAN active-active gateway function is deployed on DCGW1 and DCGW2. Specifically, a bypass VXLAN tunnel is set up between DCGW1 and DCGW2. In addition, they use a virtual anycast VTEP address to establish VXLAN tunnels with L2GW/L3GW1 and L2GW/L3GW2.
The distributed gateway function is deployed on L2GW/L3GW1 and L2GW/L3GW2, and a VXLAN tunnel is established between them.
The NetEngine 8000 F can be deployed as a DCGW and L2GW/L3GW in this networking.
Device |
Interface |
IP Address and Mask |
|---|---|---|
DCGW1 |
GE 0/1/1 |
10.6.1.1/24 |
GE 0/1/2 |
10.6.2.1/24 |
|
Loopback 0 |
9.9.9.9/32 |
|
Loopback1 |
3.3.3.3/32 |
|
Loopback2 |
33.33.33.33/32 |
|
DCGW2 |
GE 0/1/1 |
10.6.1.2/24 |
GE 0/1/2 |
10.6.3.1/24 |
|
Loopback0 |
9.9.9.9/32 |
|
Loopback1 |
4.4.4.4/32 |
|
Loopback2 |
44.44.44.44/32 |
|
L2GW/L3GW1 |
GE 0/1/1 |
10.6.4.1/24 |
GE 0/1/2 |
10.6.2.2/24 |
|
GE 0/1/3 |
- |
|
GE 0/1/4 |
- |
|
GE 0/1/5 |
- |
|
Loopback1 |
1.1.1.1/32 |
|
L2GW/L3GW2 |
GE 0/1/1 |
10.6.4.2/24 |
GE 0/1/2 |
10.6.3.2/24 |
|
GE 0/1/3 |
- |
|
GE 0/1/4 |
- |
|
Loopback1 |
2.2.2.2/32 |
Configuration Roadmap
The configuration roadmap is as follows:
- Configure a routing protocol on each DCGW and each L2GW/L3GW to ensure Layer 3 communication. OSPF is used in this example.
- Configure an EVPN instance and bind it to a BD on each DCGW and each L2GW/L3GW.
- Configure an L3VPN instance and bind it to a VBDIF interface on each DCGW and each L2GW/L3GW.
- Configure BGP EVPN on each DCGW and each L2GW/L3GW.
- Configure a VXLAN tunnel on each DCGW and each L2GW/L3GW.
- On each L2GW/L3GW, configure a Layer 2 sub-interface that connects to a VNF and static VPN routes to the VNF.
- On each L2GW/L3GW, configure BGP EVPN to import static VPN routes, and configure a route policy for the L3VPN instance to keep the original next of the static VPN routes.
- On each DCGW, configure default static routes for the VPN instance and loopback routes used to establish a VPN BGP peer relationship with a VNF. Then configure a route policy for the L3VPN instance so that the DCGW can advertise only the default static routes and loopback routes through BGP EVPN.
- Configure each DCGW to establish a VPN BGP peer relationship with a VNF.
- Configure load balancing on each DCGW and each L2GW/L3GW.
Procedure
- Assign an IP address to each device interface, including the loopback interfaces.
For configuration details, see Configuration Files in this section.
- Configure a routing protocol on each DCGW and each L2GW/L3GW to ensure Layer 3 communication. OSPF is used in this example.
For configuration details, see Configuration Files in this section.
- Configure an EVPN instance and bind it to a BD on each DCGW and each L2GW/L3GW.
# Configure DCGW1.
[~DCGW1] evpn vpn-instance evrf1 bd-mode [*DCGW1-evpn-instance-evrf1] route-distinguisher 1:1 [*DCGW1-evpn-instance-evrf1] vpn-target 1:1 [*DCGW1-evpn-instance-evrf1] quit [*DCGW1] evpn vpn-instance evrf2 bd-mode [*DCGW1-evpn-instance-evrf2] route-distinguisher 2:2 [*DCGW1-evpn-instance-evrf2] vpn-target 2:2 [*DCGW1-evpn-instance-evrf2] quit [*DCGW1] evpn vpn-instance evrf3 bd-mode [*DCGW1-evpn-instance-evrf3] route-distinguisher 3:3 [*DCGW1-evpn-instance-evrf3] vpn-target 3:3 [*DCGW1-evpn-instance-evrf3] quit [*DCGW1] evpn vpn-instance evrf4 bd-mode [*DCGW1-evpn-instance-evrf4] route-distinguisher 4:4 [*DCGW1-evpn-instance-evrf4] vpn-target 4:4 [*DCGW1-evpn-instance-evrf4] quit [*DCGW1] bridge-domain 10 [*DCGW1-bd10] vxlan vni 100 split-horizon-mode [*DCGW1-bd10] evpn binding vpn-instance evrf1 [*DCGW1-bd10] quit [*DCGW1] bridge-domain 20 [*DCGW1-bd20] vxlan vni 110 split-horizon-mode [*DCGW1-bd20] evpn binding vpn-instance evrf2 [*DCGW1-bd20] quit [*DCGW1] bridge-domain 30 [*DCGW1-bd30] vxlan vni 120 split-horizon-mode [*DCGW1-bd30] evpn binding vpn-instance evrf3 [*DCGW1-bd30] quit [*DCGW1] bridge-domain 40 [*DCGW1-bd40] vxlan vni 130 split-horizon-mode [*DCGW1-bd40] evpn binding vpn-instance evrf4 [*DCGW1-bd40] quit [*DCGW1] commit
Repeat this step for DCGW2 and each L2GW/L3GW. For configuration details, see Configuration Files in this section.
- Configure an L3VPN instance on each DCGW and each L2GW/L3GW.
# Configure DCGW1.
[~DCGW1] ip vpn-instance vpn1 [*DCGW1-vpn-instance-vpn1] vxlan vni 200 [*DCGW1-vpn-instance-vpn1] ipv4-family [*DCGW1-vpn-instance-vpn1-af-ipv4] route-distinguisher 11:11 [*DCGW1-vpn-instance-vpn1-af-ipv4] vpn-target 11:1 evpn [*DCGW1-vpn-instance-vpn1-af-ipv4] quit [*DCGW1-vpn-instance-vpn1] quit [*DCGW1] interface vbdif10 [*DCGW1-Vbdif10] ip binding vpn-instance vpn1 [*DCGW1-Vbdif10] ip address 10.1.1.1 24 [*DCGW1-Vbdif10] arp generate-rd-table enable [*DCGW1-Vbdif10] vxlan anycast-gateway enable [*DCGW1-Vbdif10] mac-address 00e0-fc00-0002 [*DCGW1-Vbdif10] quit [*DCGW1] interface vbdif20 [*DCGW1-Vbdif20] ip binding vpn-instance vpn1 [*DCGW1-Vbdif20] ip address 10.2.1.1 24 [*DCGW1-Vbdif20] arp generate-rd-table enable [*DCGW1-Vbdif20] vxlan anycast-gateway enable [*DCGW1-Vbdif20] mac-address 00e0-fc00-0003 [*DCGW1-Vbdif20] quit [*DCGW1] interface vbdif30 [*DCGW1-Vbdif30] ip binding vpn-instance vpn1 [*DCGW1-Vbdif30] ip address 10.3.1.1 24 [*DCGW1-Vbdif30] arp generate-rd-table enable [*DCGW1-Vbdif30] vxlan anycast-gateway enable [*DCGW1-Vbdif30] mac-address 00e0-fc00-0001 [*DCGW1-Vbdif30] quit [*DCGW1] interface vbdif40 [*DCGW1-Vbdif40] ip binding vpn-instance vpn1 [*DCGW1-Vbdif40] ip address 10.4.1.1 24 [*DCGW1-Vbdif40] arp generate-rd-table enable [*DCGW1-Vbdif40] vxlan anycast-gateway enable [*DCGW1-Vbdif40] mac-address 00e0-fc00-0004 [*DCGW1-Vbdif40] quit [*DCGW1] commit
Repeat this step for DCGW2 and each L2GW/L3GW. For configuration details, see Configuration Files in this section.
- Configure BGP EVPN on each DCGW and each L2GW/L3GW.
# Configure DCGW1.
[~DCGW1] ip ip-prefix uIP index 10 permit 10.10.10.10 32 [*DCGW1] route-policy stopuIP deny node 10 [*DCGW1-route-policy] if-match ip-prefix uIP [*DCGW1-route-policy] quit [*DCGW1] route-policy stopuIP permit node 20 [*DCGW1-route-policy] quit [*DCGW1] bgp 100 [*DCGW1-bgp] peer 1.1.1.1 as-number 100 [*DCGW1-bgp] peer 1.1.1.1 connect-interface LoopBack 1 [*DCGW1-bgp] peer 2.2.2.2 as-number 100 [*DCGW1-bgp] peer 2.2.2.2 connect-interface LoopBack 1 [*DCGW1-bgp] peer 4.4.4.4 as-number 100 [*DCGW1-bgp] peer 4.4.4.4 connect-interface LoopBack 1 [*DCGW1-bgp] l2vpn-family evpn [*DCGW1-bgp-af-evpn] peer 1.1.1.1 enable [*DCGW1-bgp-af-evpn] peer 1.1.1.1 advertise encap-type vxlan [*DCGW1-bgp-af-evpn] peer 2.2.2.2 enable [*DCGW1-bgp-af-evpn] peer 2.2.2.2 advertise encap-type vxlan [*DCGW1-bgp-af-evpn] peer 4.4.4.4 enable [*DCGW1-bgp-af-evpn] peer 4.4.4.4 advertise encap-type vxlan [*DCGW1-bgp-af-evpn] peer 4.4.4.4 route-policy stopuIP export [*DCGW1-bgp-af-evpn] quit [*DCGW1-bgp] quit [*DCGW1] commit
Repeat this step for DCGW2. For configuration details, see Configuration Files in this section.
# Configure L2GW/L3GW1.
[~L2GW/L3GW1] bgp 100 [*L2GW/L3GW1-bgp] peer 2.2.2.2 as-number 100 [*L2GW/L3GW1-bgp] peer 2.2.2.2 connect-interface LoopBack 1 [*L2GW/L3GW1-bgp] peer 3.3.3.3 as-number 100 [*L2GW/L3GW1-bgp] peer 3.3.3.3 connect-interface LoopBack 1 [*L2GW/L3GW1-bgp] peer 4.4.4.4 as-number 100 [*L2GW/L3GW1-bgp] peer 4.4.4.4 connect-interface LoopBack 1 [*L2GW/L3GW1-bgp] l2vpn-family evpn [*L2GW/L3GW1-bgp-af-evpn] peer 2.2.2.2 enable [*L2GW/L3GW1-bgp-af-evpn] peer 2.2.2.2 advertise encap-type vxlan [*L2GW/L3GW1-bgp-af-evpn] peer 2.2.2.2 advertise arp [*L2GW/L3GW1-bgp-af-evpn] peer 3.3.3.3 enable [*L2GW/L3GW1-bgp-af-evpn] peer 3.3.3.3 advertise encap-type vxlan [*L2GW/L3GW1-bgp-af-evpn] peer 3.3.3.3 advertise arp [*L2GW/L3GW1-bgp-af-evpn] peer 4.4.4.4 enable [*L2GW/L3GW1-bgp-af-evpn] peer 4.4.4.4 advertise encap-type vxlan [*L2GW/L3GW1-bgp-af-evpn] peer 4.4.4.4 advertise arp [*L2GW/L3GW1-bgp-af-evpn] quit [*L2GW/L3GW1-bgp] quit [*L2GW/L3GW1] commit
Repeat this step for L2GW/L3GW2. For configuration details, see Configuration Files in this section.
- Configure a VXLAN tunnel on each DCGW and each L2GW/L3GW.
# Configure DCGW1.
[~DCGW1] evpn [*DCGW1-evpn] bypass-vxlan enable [*DCGW1-evpn] quit [*DCGW1] interface nve 1 [*DCGW1-Nve1] source 9.9.9.9 [*DCGW1-Nve1] bypass source 3.3.3.3 [*DCGW1-Nve1] mac-address 00e0-fc00-0009 [*DCGW1-Nve1] vni 100 head-end peer-list protocol bgp [*DCGW1-Nve1] vni 110 head-end peer-list protocol bgp [*DCGW1-Nve1] vni 120 head-end peer-list protocol bgp [*DCGW1-Nve1] vni 130 head-end peer-list protocol bgp [*DCGW1-Nve1] quit [*DCGW1] commit
Repeat this step for DCGW2. For configuration details, see Configuration Files in this section.
# Configure L2GW/L3GW1.
[~L2GW/L3GW1] interface nve 1 [*L2GW/L3GW1-Nve1] source 1.1.1.1 [*L2GW/L3GW1-Nve1] vni 100 head-end peer-list protocol bgp [*L2GW/L3GW1-Nve1] vni 110 head-end peer-list protocol bgp [*L2GW/L3GW1-Nve1] vni 120 head-end peer-list protocol bgp [*L2GW/L3GW1-Nve1] vni 130 head-end peer-list protocol bgp [*L2GW/L3GW1-Nve1] quit [*L2GW/L3GW1] commit
Repeat this step for L2GW/L3GW2. For configuration details, see Configuration Files in this section.
- On each L2GW/L3GW, configure a Layer 2 sub-interface that connects to a VNF and static VPN routes to the VNF.
# Configure L2GW/L3GW1.
[~L2GW/L3GW1] interface GigabitEthernet0/1/3.1 mode l2 [*L2GW/L3GW1-GigabitEthernet0/1/3.1] encapsulation dot1q vid 10 [*L2GW/L3GW1-GigabitEthernet0/1/3.1] rewrite pop single [*L2GW/L3GW1-GigabitEthernet0/1/3.1] bridge-domain 10 [*L2GW/L3GW1-GigabitEthernet0/1/3.1] quit [*L2GW/L3GW1] interface GigabitEthernet0/1/4.1 mode l2 [*L2GW/L3GW1-GigabitEthernet0/1/4.1] encapsulation dot1q vid 20 [*L2GW/L3GW1-GigabitEthernet0/1/4.1] rewrite pop single [*L2GW/L3GW1-GigabitEthernet0/1/4.1] bridge-domain 20 [*L2GW/L3GW1-GigabitEthernet0/1/4.1] quit [*L2GW/L3GW1] interface GigabitEthernet0/1/5.1 mode l2 [*L2GW/L3GW1-GigabitEthernet0/1/5.1] encapsulation dot1q vid 10 [*L2GW/L3GW1-GigabitEthernet0/1/5.1] rewrite pop single [*L2GW/L3GW1-GigabitEthernet0/1/5.1] bridge-domain 10 [*L2GW/L3GW1-GigabitEthernet0/1/5.1] quit [*L2GW/L3GW1] ip route-static vpn-instance vpn1 5.5.5.5 255.255.255.255 10.1.1.2 tag 1000 [*L2GW/L3GW1] ip route-static vpn-instance vpn1 5.5.5.5 255.255.255.255 10.2.1.2 tag 1000 [*L2GW/L3GW1] ip route-static vpn-instance vpn1 6.6.6.6 255.255.255.255 10.1.1.3 tag 1000 [*L2GW/L3GW1] commit
Repeat this step for L2GW/L3GW2. For configuration details, see Configuration Files in this section.
- On each L2GW/L3GW, configure BGP EVPN to import static VPN routes, and configure a route policy for the L3VPN instance to keep the original next of the static VPN routes.
# Configure L2GW/L3GW1.
[~L2GW/L3GW1] bgp 100 [*L2GW/L3GW1-bgp] ipv4-family vpn-instance vpn1 [*L2GW/L3GW1-bgp-vpn1] import-route static [*L2GW/L3GW1-bgp-vpn1] advertise l2vpn evpn import-route-multipath [*L2GW/L3GW1-bgp-vpn1] quit [*L2GW/L3GW1-bgp] quit [*L2GW/L3GW1] route-policy sp permit node 10 [*L2GW/L3GW1-route-policy] if-match tag 1000 [*L2GW/L3GW1-route-policy] apply gateway-ip origin-nexthop [*L2GW/L3GW1-route-policy] quit [*L2GW/L3GW1] route-policy sp deny node 20 [*L2GW/L3GW1-route-policy] quit [*L2GW/L3GW1] ip vpn-instance vpn1 [*L2GW/L3GW1-vpn-instance-vpn1] export route-policy sp evpn [*L2GW/L3GW1-vpn-instance-vpn1] quit [*L2GW/L3GW1] commit
Repeat this step for L2GW/L3GW2. For configuration details, see Configuration Files in this section.
- On each DCGW, configure default static routes for the VPN instance and loopback routes used to establish a VPN BGP peer relationship with a VNF. Then configure a route policy for the L3VPN instance so that the DCGW can advertise only the default static routes and loopback routes through BGP EVPN.
# Configure DCGW1.
[~DCGW1] ip route-static vpn-instance vpn1 0.0.0.0 0.0.0.0 NULL0 tag 2000 [*DCGW1] interface LoopBack2 [*DCGW1-LoopBack2] ip binding vpn-instance vpn1 [*DCGW1-LoopBack2] ip address 33.33.33.33 255.255.255.255 [*DCGW1-LoopBack2] quit [*DCGW1] bgp 100 [*DCGW1-bgp] ipv4-family vpn-instance vpn1 [*DCGW1-bgp-vpn1] advertise l2vpn evpn [*DCGW1-bgp-vpn1] import-route direct [*DCGW1-bgp-vpn1] network 0.0.0.0 0 [*DCGW1-bgp-vpn1] quit [*DCGW1-bgp] quit [*DCGW1] ip ip-prefix lp index 10 permit 33.33.33.33 32 [*DCGW1] route-policy dp permit node 10 [*DCGW1-route-policy] if-match tag 2000 [*DCGW1-route-policy] quit [*DCGW1] route-policy dp permit node 15 [*DCGW1-route-policy] if-match ip-prefix lp [*DCGW1-route-policy] quit [*DCGW1] route-policy dp deny node 20 [*DCGW1-route-policy] quit [*DCGW1] ip vpn-instance vpn1 [*DCGW1-vpn-instance-vpn1] export route-policy dp evpn [*DCGW1-vpn-instance-vpn1] quit [*DCGW1] commit
Repeat this step for DCGW2. For configuration details, see Configuration Files in this section.
- Configure each DCGW to establish a VPN BGP peer relationship with a VNF.
# Configure DCGW1.
[~DCGW1] route-policy p1 deny node 10 [*DCGW1-route-policy] quit [*DCGW1] bgp 100 [*DCGW1-bgp] ipv4-family vpn-instance vpn1 [*DCGW1-bgp-vpn1] peer 5.5.5.5 as-number 100 [*DCGW1-bgp-vpn1] peer 5.5.5.5 connect-interface LoopBack2 [*DCGW1-bgp-vpn1] peer 5.5.5.5 route-policy p1 export [*DCGW1-bgp-vpn1] peer 6.6.6.6 as-number 100 [*DCGW1-bgp-vpn1] peer 6.6.6.6 connect-interface LoopBack2 [*DCGW1-bgp-vpn1] peer 6.6.6.6 route-policy p1 export [*DCGW1-bgp-vpn1] quit [*DCGW1-bgp] quit [*DCGW1] commit
# Configure DCGW2.
[~DCGW2] route-policy p1 deny node 10 [*DCGW2-route-policy] quit [*DCGW2] bgp 100 [*DCGW2-bgp] ipv4-family vpn-instance vpn1 [*DCGW2-bgp-vpn1] peer 5.5.5.5 as-number 100 [*DCGW2-bgp-vpn1] peer 5.5.5.5 connect-interface LoopBack2 [*DCGW2-bgp-vpn1] peer 5.5.5.5 route-policy p1 export [*DCGW2-bgp-vpn1] peer 6.6.6.6 as-number 100 [*DCGW2-bgp-vpn1] peer 6.6.6.6 connect-interface LoopBack2 [*DCGW2-bgp-vpn1] peer 6.6.6.6 route-policy p1 export [*DCGW2-bgp-vpn1] quit [*DCGW2-bgp] quit [*DCGW2] commit
- Configure load balancing on each DCGW and each L2GW/L3GW.
# Configure DCGW1.
[~DCGW1] bgp 100 [*DCGW1-bgp] ipv4-family vpn-instance vpn1 [*DCGW1-bgp-vpn1] maximum load-balancing 16 [*DCGW1-bgp-vpn1] quit [*DCGW1-bgp] l2vpn-family evpn [*DCGW1-bgp-af-evpn] peer 1.1.1.1 capability-advertise add-path both [*DCGW1-bgp-af-evpn] peer 1.1.1.1 advertise add-path path-number 16 [*DCGW1-bgp-af-evpn] peer 2.2.2.2 capability-advertise add-path both [*DCGW1-bgp-af-evpn] peer 2.2.2.2 advertise add-path path-number 16 [*DCGW1-bgp-af-evpn] quit [*DCGW1-bgp] quit [*DCGW1] commit
Repeat this step for DCGW2. For configuration details, see Configuration Files in this section.
# Configure L2GW/L3GW1.
[~L2GW/L3GW1] bgp 100 [*L2GW/L3GW1-bgp] ipv4-family vpn-instance vpn1 [*L2GW/L3GW1-bgp-vpn1] maximum load-balancing 16 [*L2GW/L3GW1-bgp-vpn1] quit [*L2GW/L3GW1-bgp] l2vpn-family evpn [*L2GW/L3GW1-bgp-af-evpn] bestroute add-path path-number 16 [*L2GW/L3GW1-bgp-af-evpn] peer 3.3.3.3 capability-advertise add-path both [*L2GW/L3GW1-bgp-af-evpn] peer 3.3.3.3 advertise add-path path-number 16 [*L2GW/L3GW1-bgp-af-evpn] peer 4.4.4.4 capability-advertise add-path both [*L2GW/L3GW1-bgp-af-evpn] peer 4.4.4.4 advertise add-path path-number 16 [*L2GW/L3GW1-bgp-af-evpn] quit [*L2GW/L3GW1-bgp] quit [*L2GW/L3GW1] commit
Repeat this step for L2GW/L3GW2. For configuration details, see Configuration Files in this section.
- Verify the configuration.
Run the display bgp vpnv4 vpn-instance vpn1 peer command on each DCGW. The command output shows that the VPN BGP peer relationship between the DCGW and VNF is in Established state. The following example uses the command output on DCGW1:
[~DCGW1] display bgp vpnv4 vpn-instance vpn1 peer BGP local router ID : 10.6.1.1 Local AS number : 100 VPN-Instance vpn1, Router ID 10.6.1.1: Total number of peers : 2 Peers in established state : 2 Peer V AS MsgRcvd MsgSent OutQ Up/Down State PrefRcv 5.5.5.5 4 100 8136 8135 0 0118h05m Established 4 6.6.6.6 4 100 8140 8167 0 0118h07m Established 0Run the display bgp vpnv4 vpn-instance vpn1 routing-table command on each DCGW. The command output shows that the DCGW has received the mobile phone route (destined for 10.10.10.10 in this example) from the VNF and the next hop of the route is the VNF IP address. The following example uses the command output on DCGW1:
[~DCGW1] display bgp vpnv4 vpn-instance vpn1 routing-table BGP Local router ID is 10.6.1.1 Status codes: * - valid, > - best, d - damped, x - best external, a - add path, h - history, i - internal, s - suppressed, S - Stale Origin : i - IGP, e - EGP, ? - incomplete RPKI validation codes: V - valid, I - invalid, N - not-found VPN-Instance vpn1, Router ID 10.6.1.1: Total Number of Routes: 20 Network NextHop MED LocPrf PrefVal Path/Ogn *>i 5.5.5.5/32 1.1.1.1 0 100 0 ? * i 1.1.1.1 0 100 0 ? i 5.5.5.5 0 100 0 ? *>i 6.6.6.6/32 1.1.1.1 0 100 0 ? * i 2.2.2.2 0 100 0 ? * i 2.2.2.2 0 100 0 ? *> 10.1.1.0/24 0.0.0.0 0 0 ? * i 5.5.5.5 0 100 0 ? *> 10.1.1.1/32 0.0.0.0 0 0 ? *> 10.2.1.0/24 0.0.0.0 0 0 ? * i 5.5.5.5 0 100 0 ? *> 10.2.1.1/32 0.0.0.0 0 0 ? *> 10.3.1.0/24 0.0.0.0 0 0 ? *> 10.3.1.1/32 0.0.0.0 0 0 ? *> 10.4.1.0/24 0.0.0.0 0 0 ? *> 10.4.1.1/32 0.0.0.0 0 0 ? *>i 10.10.10.10/32 5.5.5.5 0 100 0 ? *> 33.33.33.33/32 0.0.0.0 0 0 ? *>i 44.44.44.44/32 9.9.9.9 0 100 0 ? *> 127.0.0.0/8 0.0.0.0 0 0 ?Run the display ip routing-table vpn-instance vpn1 command on each DCGW. The command output shows the mobile phone routes in the VPN routing table on the DCGW and the outbound interfaces of the routes are VBDIF interfaces.
[~DCGW1] display ip routing-table vpn-instance vpn1 Route Flags: R - relay, D - download to fib, T - to vpn-instance, B - black hole route ------------------------------------------------------------------------------ Routing Table : vpn1 Destinations : 20 Routes : 23 Destination/Mask Proto Pre Cost Flags NextHop Interface 0.0.0.0/0 Static 60 0 DB 0.0.0.0 NULL0 5.5.5.5/32 IBGP 255 0 RD 10.2.1.2 Vbdif20 IBGP 255 0 RD 10.1.1.2 Vbdif10 6.6.6.6/32 IBGP 255 0 RD 10.1.1.3 Vbdif10 IBGP 255 0 RD 10.3.1.2 Vbdif30 IBGP 255 0 RD 10.4.1.2 Vbdif40 10.1.1.0/24 Direct 0 0 D 10.1.1.1 Vbdif10 10.1.1.1/32 Direct 0 0 D 127.0.0.1 Vbdif10 10.1.1.255/32 Direct 0 0 D 127.0.0.1 Vbdif10 10.2.1.0/24 Direct 0 0 D 10.2.1.1 Vbdif20 10.2.1.1/32 Direct 0 0 D 127.0.0.1 Vbdif20 10.2.1.255/32 Direct 0 0 D 127.0.0.1 Vbdif20 10.3.1.0/24 Direct 0 0 D 10.3.1.1 Vbdif30 10.3.1.1/32 Direct 0 0 D 127.0.0.1 Vbdif30 10.3.1.255/32 Direct 0 0 D 127.0.0.1 Vbdif30 10.4.1.0/24 Direct 0 0 D 10.4.1.1 Vbdif40 10.4.1.1/32 Direct 0 0 D 127.0.0.1 Vbdif40 10.4.1.255/32 Direct 0 0 D 127.0.0.1 Vbdif40 10.10.10.10/32 IBGP 255 0 RD 5.5.5.5 Vbdif20 IBGP 255 0 RD 5.5.5.5 Vbdif10 33.33.33.33/32 Direct 0 0 D 127.0.0.1 LoopBack2 44.44.44.44/32 IBGP 255 0 RD 4.4.4.4 VXLAN 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 255.255.255.255/32 Direct 0 0 D 127.0.0.1 InLoopBack0
Configuration Files
DCGW1 configuration file
# sysname DCGW1 # evpn bypass-vxlan enable # evpn vpn-instance evrf1 bd-mode route-distinguisher 1:1 vpn-target 1:1 export-extcommunity vpn-target 1:1 import-extcommunity # evpn vpn-instance evrf2 bd-mode route-distinguisher 2:2 vpn-target 2:2 export-extcommunity vpn-target 2:2 import-extcommunity # evpn vpn-instance evrf3 bd-mode route-distinguisher 3:3 vpn-target 3:3 export-extcommunity vpn-target 3:3 import-extcommunity # evpn vpn-instance evrf4 bd-mode route-distinguisher 4:4 vpn-target 4:4 export-extcommunity vpn-target 4:4 import-extcommunity # ip vpn-instance vpn1 ipv4-family route-distinguisher 11:11 apply-label per-instance export route-policy dp evpn vpn-target 11:1 export-extcommunity evpn vpn-target 11:1 import-extcommunity evpn vxlan vni 200 # bridge-domain 10 vxlan vni 100 split-horizon-mode evpn binding vpn-instance evrf1 # bridge-domain 20 vxlan vni 110 split-horizon-mode evpn binding vpn-instance evrf2 # bridge-domain 30 vxlan vni 120 split-horizon-mode evpn binding vpn-instance evrf3 # bridge-domain 40 vxlan vni 130 split-horizon-mode evpn binding vpn-instance evrf4 # interface Vbdif10 ip binding vpn-instance vpn1 ip address 10.1.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0002 vxlan anycast-gateway enable # interface Vbdif20 ip binding vpn-instance vpn1 ip address 10.2.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0003 vxlan anycast-gateway enable # interface Vbdif30 ip binding vpn-instance vpn1 ip address 10.3.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0001 vxlan anycast-gateway enable # interface Vbdif40 ip binding vpn-instance vpn1 ip address 10.4.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0004 vxlan anycast-gateway enable # interface GigabitEthernet0/1/1 undo shutdown ip address 10.6.1.1 255.255.255.0 # interface GigabitEthernet0/1/2 undo shutdown ip address 10.6.2.1 255.255.255.0 # interface LoopBack0 ip address 9.9.9.9 255.255.255.255 # interface LoopBack1 ip address 3.3.3.3 255.255.255.255 # interface LoopBack2 ip binding vpn-instance vpn1 ip address 33.33.33.33 255.255.255.255 # interface Nve1 source 9.9.9.9 bypass source 3.3.3.3 mac-address 00e0-fc00-0009 vni 100 head-end peer-list protocol bgp vni 110 head-end peer-list protocol bgp vni 120 head-end peer-list protocol bgp vni 130 head-end peer-list protocol bgp # bgp 100 peer 1.1.1.1 as-number 100 peer 1.1.1.1 connect-interface LoopBack1 peer 2.2.2.2 as-number 100 peer 2.2.2.2 connect-interface LoopBack1 peer 4.4.4.4 as-number 100 peer 4.4.4.4 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 1.1.1.1 enable peer 2.2.2.2 enable peer 4.4.4.4 enable # ipv4-family vpn-instance vpn1 network 0.0.0.0 0 import-route direct maximum load-balancing 16 advertise l2vpn evpn peer 5.5.5.5 as-number 100 peer 5.5.5.5 connect-interface LoopBack2 peer 5.5.5.5 route-policy p1 export peer 6.6.6.6 as-number 100 peer 6.6.6.6 connect-interface LoopBack2 peer 6.6.6.6 route-policy p1 export # l2vpn-family evpn undo policy vpn-target peer 1.1.1.1 enable peer 1.1.1.1 capability-advertise add-path both peer 1.1.1.1 advertise add-path path-number 16 peer 1.1.1.1 advertise encap-type vxlan peer 2.2.2.2 enable peer 2.2.2.2 capability-advertise add-path both peer 2.2.2.2 advertise add-path path-number 16 peer 2.2.2.2 advertise encap-type vxlan peer 4.4.4.4 enable peer 4.4.4.4 advertise encap-type vxlan peer 4.4.4.4 route-policy stopuIP export # ospf 1 area 0.0.0.0 network 3.3.3.3 0.0.0.0 network 9.9.9.9 0.0.0.0 network 10.6.1.0 0.0.0.255 network 10.6.2.0 0.0.0.255 # route-policy dp permit node 10 if-match tag 2000 # route-policy dp permit node 15 if-match ip-prefix lp # route-policy dp deny node 20 # route-policy p1 deny node 10 # route-policy stopuIP deny node 10 if-match ip-prefix uIP # route-policy stopuIP permit node 20 # ip ip-prefix lp index 10 permit 33.33.33.33 32 ip ip-prefix uIP index 10 permit 10.10.10.10 32 # ip route-static vpn-instance vpn1 0.0.0.0 0.0.0.0 NULL0 tag 2000 # return
DCGW2 configuration file
# sysname DCGW2 # evpn bypass-vxlan enable # evpn vpn-instance evrf1 bd-mode route-distinguisher 1:1 vpn-target 1:1 export-extcommunity vpn-target 1:1 import-extcommunity # evpn vpn-instance evrf2 bd-mode route-distinguisher 2:2 vpn-target 2:2 export-extcommunity vpn-target 2:2 import-extcommunity # evpn vpn-instance evrf3 bd-mode route-distinguisher 3:3 vpn-target 3:3 export-extcommunity vpn-target 3:3 import-extcommunity # evpn vpn-instance evrf4 bd-mode route-distinguisher 4:4 vpn-target 4:4 export-extcommunity vpn-target 4:4 import-extcommunity # ip vpn-instance vpn1 ipv4-family route-distinguisher 22:22 apply-label per-instance export route-policy dp evpn vpn-target 11:1 export-extcommunity evpn vpn-target 11:1 import-extcommunity evpn vxlan vni 200 # bridge-domain 10 vxlan vni 100 split-horizon-mode evpn binding vpn-instance evrf1 # bridge-domain 20 vxlan vni 110 split-horizon-mode evpn binding vpn-instance evrf2 # bridge-domain 30 vxlan vni 120 split-horizon-mode evpn binding vpn-instance evrf3 # bridge-domain 40 vxlan vni 130 split-horizon-mode evpn binding vpn-instance evrf4 # interface Vbdif10 ip binding vpn-instance vpn1 ip address 10.1.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0002 vxlan anycast-gateway enable # interface Vbdif20 ip binding vpn-instance vpn1 ip address 10.2.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0003 vxlan anycast-gateway enable # interface Vbdif30 ip binding vpn-instance vpn1 ip address 10.3.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0001 vxlan anycast-gateway enable # interface Vbdif40 ip binding vpn-instance vpn1 ip address 10.4.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0004 vxlan anycast-gateway enable # interface GigabitEthernet0/1/1 undo shutdown ip address 10.6.1.2 255.255.255.0 # interface GigabitEthernet0/1/2 undo shutdown ip address 10.6.3.1 255.255.255.0 # interface LoopBack0 ip address 9.9.9.9 255.255.255.255 # interface LoopBack1 ip address 4.4.4.4 255.255.255.255 # interface LoopBack2 ip binding vpn-instance vpn1 ip address 44.44.44.44 255.255.255.255 # interface Nve1 source 9.9.9.9 bypass source 4.4.4.4 mac-address 00e0-fc00-0009 vni 100 head-end peer-list protocol bgp vni 110 head-end peer-list protocol bgp vni 120 head-end peer-list protocol bgp vni 130 head-end peer-list protocol bgp # bgp 100 peer 1.1.1.1 as-number 100 peer 1.1.1.1 connect-interface LoopBack1 peer 2.2.2.2 as-number 100 peer 2.2.2.2 connect-interface LoopBack1 peer 3.3.3.3 as-number 100 peer 3.3.3.3 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 1.1.1.1 enable peer 2.2.2.2 enable peer 3.3.3.3 enable # ipv4-family vpn-instance vpn1 network 0.0.0.0 0 import-route direct maximum load-balancing 16 advertise l2vpn evpn peer 5.5.5.5 as-number 100 peer 5.5.5.5 connect-interface LoopBack2 peer 5.5.5.5 route-policy p1 export peer 6.6.6.6 as-number 100 peer 6.6.6.6 connect-interface LoopBack2 peer 6.6.6.6 route-policy p1 export # l2vpn-family evpn undo policy vpn-target peer 1.1.1.1 enable peer 1.1.1.1 capability-advertise add-path both peer 1.1.1.1 advertise add-path path-number 16 peer 1.1.1.1 advertise encap-type vxlan peer 2.2.2.2 enable peer 2.2.2.2 capability-advertise add-path both peer 2.2.2.2 advertise add-path path-number 16 peer 2.2.2.2 advertise encap-type vxlan peer 3.3.3.3 enable peer 3.3.3.3 advertise encap-type vxlan peer 3.3.3.3 route-policy stopuIP export # ospf 1 area 0.0.0.0 network 4.4.4.4 0.0.0.0 network 9.9.9.9 0.0.0.0 network 10.6.1.0 0.0.0.255 network 10.6.3.0 0.0.0.255 # route-policy dp permit node 10 if-match tag 2000 # route-policy dp permit node 15 if-match ip-prefix lp # route-policy dp deny node 20 # route-policy p1 deny node 10 # route-policy stopuIP deny node 10 if-match ip-prefix uIP # route-policy stopuIP permit node 20 # ip ip-prefix lp index 10 permit 44.44.44.44 32 ip ip-prefix uIP index 10 permit 10.10.10.10 32 # ip route-static vpn-instance vpn1 0.0.0.0 0.0.0.0 NULL0 tag 2000 # return
L2GW/L3GW1 configuration file
# sysname L2GW/L3GW1 # evpn vpn-instance evrf1 bd-mode route-distinguisher 1:1 vpn-target 1:1 export-extcommunity vpn-target 1:1 import-extcommunity # evpn vpn-instance evrf2 bd-mode route-distinguisher 2:2 vpn-target 2:2 export-extcommunity vpn-target 2:2 import-extcommunity # evpn vpn-instance evrf3 bd-mode route-distinguisher 3:3 vpn-target 3:3 export-extcommunity vpn-target 3:3 import-extcommunity # evpn vpn-instance evrf4 bd-mode route-distinguisher 4:4 vpn-target 4:4 export-extcommunity vpn-target 4:4 import-extcommunity # ip vpn-instance vpn1 ipv4-family route-distinguisher 33:33 apply-label per-instance export route-policy sp evpn vpn-target 11:1 export-extcommunity evpn vpn-target 11:1 import-extcommunity evpn vxlan vni 200 # bridge-domain 10 vxlan vni 100 split-horizon-mode evpn binding vpn-instance evrf1 # bridge-domain 20 vxlan vni 110 split-horizon-mode evpn binding vpn-instance evrf2 # bridge-domain 30 vxlan vni 120 split-horizon-mode evpn binding vpn-instance evrf3 # bridge-domain 40 vxlan vni 130 split-horizon-mode evpn binding vpn-instance evrf4 # interface Vbdif10 ip binding vpn-instance vpn1 ip address 10.1.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0002 vxlan anycast-gateway enable arp collect host enable # interface Vbdif20 ip binding vpn-instance vpn1 ip address 10.2.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0003 vxlan anycast-gateway enable arp collect host enable # interface Vbdif30 ip binding vpn-instance vpn1 ip address 10.3.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0001 vxlan anycast-gateway enable arp collect host enable # interface Vbdif40 ip binding vpn-instance vpn1 ip address 10.4.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0004 vxlan anycast-gateway enable arp collect host enable # interface GigabitEthernet0/1/1 undo shutdown ip address 10.6.4.1 255.255.255.0 # interface GigabitEthernet0/1/2 undo shutdown ip address 10.6.2.2 255.255.255.0 # interface GigabitEthernet0/1/3.1 mode l2 encapsulation dot1q vid 10 rewrite pop single bridge-domain 10 # interface GigabitEthernet0/1/4.1 mode l2 encapsulation dot1q vid 20 rewrite pop single bridge-domain 20 # interface GigabitEthernet0/1/5.1 mode l2 encapsulation dot1q vid 10 rewrite pop single bridge-domain 10 # interface LoopBack1 ip address 1.1.1.1 255.255.255.255 # interface Nve1 source 1.1.1.1 vni 100 head-end peer-list protocol bgp vni 110 head-end peer-list protocol bgp vni 120 head-end peer-list protocol bgp vni 130 head-end peer-list protocol bgp # bgp 100 peer 2.2.2.2 as-number 100 peer 2.2.2.2 connect-interface LoopBack1 peer 3.3.3.3 as-number 100 peer 3.3.3.3 connect-interface LoopBack1 peer 4.4.4.4 as-number 100 peer 4.4.4.4 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 2.2.2.2 enable peer 3.3.3.3 enable peer 4.4.4.4 enable # ipv4-family vpn-instance vpn1 import-route static maximum load-balancing 16 advertise l2vpn evpn import-route-multipath # l2vpn-family evpn undo policy vpn-target bestroute add-path path-number 16 peer 2.2.2.2 enable peer 2.2.2.2 advertise arp peer 2.2.2.2 advertise encap-type vxlan peer 3.3.3.3 enable peer 3.3.3.3 advertise arp peer 3.3.3.3 capability-advertise add-path both peer 3.3.3.3 advertise add-path path-number 16 peer 3.3.3.3 advertise encap-type vxlan peer 4.4.4.4 enable peer 4.4.4.4 advertise arp peer 4.4.4.4 capability-advertise add-path both peer 4.4.4.4 advertise add-path path-number 16 peer 4.4.4.4 advertise encap-type vxlan # ospf 1 area 0.0.0.0 network 1.1.1.1 0.0.0.0 network 10.6.2.0 0.0.0.255 network 10.6.4.0 0.0.0.255 # route-policy sp permit node 10 if-match tag 1000 apply gateway-ip origin-nexthop # route-policy sp deny node 20 # ip route-static vpn-instance vpn1 5.5.5.5 255.255.255.255 10.1.1.2 tag 1000 ip route-static vpn-instance vpn1 5.5.5.5 255.255.255.255 10.2.1.2 tag 1000 ip route-static vpn-instance vpn1 6.6.6.6 255.255.255.255 10.1.1.3 tag 1000 # return
L2GW/L3GW2 configuration file
# sysname L2GW/L3GW2 # evpn vpn-instance evrf1 bd-mode route-distinguisher 1:1 vpn-target 1:1 export-extcommunity vpn-target 1:1 import-extcommunity # evpn vpn-instance evrf2 bd-mode route-distinguisher 2:2 vpn-target 2:2 export-extcommunity vpn-target 2:2 import-extcommunity # evpn vpn-instance evrf3 bd-mode route-distinguisher 3:3 vpn-target 3:3 export-extcommunity vpn-target 3:3 import-extcommunity # evpn vpn-instance evrf4 bd-mode route-distinguisher 4:4 vpn-target 4:4 export-extcommunity vpn-target 4:4 import-extcommunity # ip vpn-instance vpn1 ipv4-family route-distinguisher 44:44 apply-label per-instance export route-policy sp evpn vpn-target 11:1 export-extcommunity evpn vpn-target 11:1 import-extcommunity evpn vxlan vni 200 # bridge-domain 10 vxlan vni 100 split-horizon-mode evpn binding vpn-instance evrf1 # bridge-domain 20 vxlan vni 110 split-horizon-mode evpn binding vpn-instance evrf2 # bridge-domain 30 vxlan vni 120 split-horizon-mode evpn binding vpn-instance evrf3 # bridge-domain 40 vxlan vni 130 split-horizon-mode evpn binding vpn-instance evrf4 # interface Vbdif10 ip binding vpn-instance vpn1 ip address 10.1.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0002 vxlan anycast-gateway enable arp collect host enable # interface Vbdif20 ip binding vpn-instance vpn1 ip address 10.2.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0003 vxlan anycast-gateway enable arp collect host enable # interface Vbdif30 ip binding vpn-instance vpn1 ip address 10.3.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0001 vxlan anycast-gateway enable arp collect host enable # interface Vbdif40 ip binding vpn-instance vpn1 ip address 10.4.1.1 255.255.255.0 arp generate-rd-table enable mac-address 00e0-fc00-0004 vxlan anycast-gateway enable arp collect host enable # interface GigabitEthernet0/1/1 undo shutdown ip address 10.6.4.2 255.255.255.0 # interface GigabitEthernet0/1/2 undo shutdown ip address 10.6.3.2 255.255.255.0 # interface GigabitEthernet0/1/3.1 mode l2 encapsulation dot1q vid 30 rewrite pop single bridge-domain 30 # interface GigabitEthernet0/1/4.1 mode l2 encapsulation dot1q vid 40 rewrite pop single bridge-domain 40 # interface LoopBack1 ip address 2.2.2.2 255.255.255.255 # interface Nve1 source 2.2.2.2 vni 100 head-end peer-list protocol bgp vni 110 head-end peer-list protocol bgp vni 120 head-end peer-list protocol bgp vni 130 head-end peer-list protocol bgp # bgp 100 peer 1.1.1.1 as-number 100 peer 1.1.1.1 connect-interface LoopBack1 peer 3.3.3.3 as-number 100 peer 3.3.3.3 connect-interface LoopBack1 peer 4.4.4.4 as-number 100 peer 4.4.4.4 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 1.1.1.1 enable peer 3.3.3.3 enable peer 4.4.4.4 enable # ipv4-family vpn-instance vpn1 import-route static maximum load-balancing 16 advertise l2vpn evpn import-route-multipath # l2vpn-family evpn undo policy vpn-target bestroute add-path path-number 16 peer 1.1.1.1 enable peer 1.1.1.1 advertise arp peer 1.1.1.1 advertise encap-type vxlan peer 3.3.3.3 enable peer 3.3.3.3 advertise arp peer 3.3.3.3 capability-advertise add-path both peer 3.3.3.3 advertise add-path path-number 16 peer 3.3.3.3 advertise encap-type vxlan peer 4.4.4.4 enable peer 4.4.4.4 advertise arp peer 4.4.4.4 capability-advertise add-path both peer 4.4.4.4 advertise add-path path-number 16 peer 4.4.4.4 advertise encap-type vxlan # ospf 1 area 0.0.0.0 network 2.2.2.2 0.0.0.0 network 10.6.3.0 0.0.0.255 network 10.6.4.0 0.0.0.255 # route-policy sp permit node 10 if-match tag 1000 apply gateway-ip origin-nexthop # route-policy sp deny node 20 # ip route-static vpn-instance vpn1 6.6.6.6 255.255.255.255 10.3.1.2 tag 1000 ip route-static vpn-instance vpn1 6.6.6.6 255.255.255.255 10.4.1.2 tag 1000 # return
VNF1 configuration file
For details, see the configuration file of a specific device model.
VNF2 configuration file
For details, see the configuration file of a specific device model.