To establish an IPsec tunnel in IKE mode, you need to configure the necessary parameter for the IKE negotiation, and then the IKE negotiation automatically creates and maintains the SA.
Networking Requirements
As shown in Figure 1, network A and network B connect to the Internet through DeviceA and DeviceB respectively.
Figure 1 Typical networking of the gateway to gateway mode
Interfaces 1 and 2 in this example represent GE 0/1/1 and GE 0/1/2, respectively.
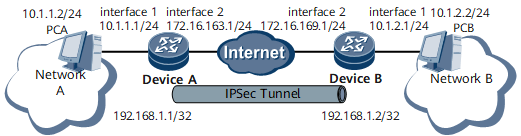
The network environment is as follows:
Network A is in the network segment of 10.1.1.0/24. This network connects to DeviceA through GE 0/1/1.
Network B is in the network segment of 10.1.2.0/24. This network connects to DeviceB through GE 0/1/1.
Routes between DeviceA and DeviceB are available.
The IPsec function of DeviceA and DeviceB reside in slot 1.
An IPsec tunnel needs to be configured to implement secure communication between PCA and PCB.
Configuration Notes
After an IPsec tunnel is configured, ensure that both ends of the tunnel are routable.
Configuration Roadmap
This example describes how to configure the IPsec tunnel through IKE in gateway to gateway networking mode. The encapsulation mode is the tunneling mode.
Set the IP addresses for the interfaces.
Create and configure the tunnel interface.
Configure the route of the Internet. Generally, static routes are configured.
Configure the ACL to define the data flows that need to be protected.
Configure the IPsec proposal.
Configure the IKE proposal.
Configure the IKE peer.
Configure the IPsec policy.
Configure the IPsec service instance group
Apply the IPsec policy to Tunnel interface.
Data Preparation
To complete the configuration, you need the following data:
- IP addresses of the interfaces
- IP addresses of the tunnel interfaces
- IP address segments of each network
- Pre-shared key
- Security protocol, encryption algorithm, and authentication algorithm adopted in an IPsec proposal
- Authentication algorithm adopted in an IKE proposal
Procedure
- Configure DeviceA.
- Set the IP addresses of interfaces.
Set the IP address of GE 0/1/1.
<DeviceA> system-view
[~DeviceA] interface GigabitEthernet 0/1/1
[~DeviceA-GigabitEthernet0/1/1] ip address 10.1.1.1 24
[*DeviceA-GigabitEthernet0/1/1] quit
[*DeviceA] commit
Set the IP address of GE 0/1/2
[~DeviceA] interface GigabitEthernet 0/1/2
[~DeviceA-GigabitEthernet0/1/2] ip address 172.16.163.1 24
[*DeviceA-GigabitEthernet0/1/2] quit
[*DeviceA] commit
- Create and configure the tunnel interface.
[~DeviceA] interface Tunnel 10
[*DeviceA-Tunnel10] tunnel-protocol ipsec
[*DeviceA-Tunnel10] ip address 192.168.1.1 32
[*DeviceA-Tunnel10] quit
[*DeviceA] commit
- Configure the static route to reach network B. The outbound interface is Tunnel 10 and the next hop to 192.168.1.2 (the IP address of the tunnel interface of the peer). Assume that the next hop of DeviceA is 172.16.163.2/24.
[~DeviceA] ip route-static 10.1.2.0 255.255.255.0 Tunnel 10 192.168.1.2
[*DeviceA] ip route-static 192.168.1.2 255.255.255.255 172.16.163.2
[*DeviceA] commit
- Configure advanced ACL 3000 to permit PCA to access PCB.
[~DeviceA] acl 3000
[*DeviceA-acl-adv-3000] rule permit ip source 10.1.1.2 0.0.0.0 destination 10.1.2.2 0.0.0.0
[*DeviceA-acl-adv-3000] quit
[*DeviceA] commit
- Configure the IPsec proposal with the name as tran1.
[~DeviceA] ipsec proposal tran1
[*DeviceA-ipsec-proposal-tran1] encapsulation-mode tunnel
[*DeviceA-ipsec-proposal-tran1] transform esp
[*DeviceA-ipsec-proposal-tran1] esp authentication-algorithm sha2-256
[*DeviceA-ipsec-proposal-tran1] esp encryption-algorithm aes 256
[*DeviceA-ipsec-proposal-tran1] quit
[*DeviceA] commit
- Configure the IKE proposal with the number as 10.
[~DeviceA] ike proposal 10
[*DeviceA-ike-proposal-10] authentication-method pre-share
[*DeviceA-ike-proposal-10] authentication-algorithm sha2-256
[*DeviceA-ike-proposal-10] dh group14
[*DeviceA-ike-proposal-10] quit
[*DeviceA] commit
- Configure the IKE peer with the name as b.

- The setting of the pre-shared key should be identical with that on the peer device.
[~DeviceA] ike peer b
[*DeviceA-ike-peer-b] ike-proposal 10
[*DeviceA-ike-peer-b] remote-address 192.168.1.2
[*DeviceA-ike-peer-b] pre-shared-key abcde
[*DeviceA-ike-peer-b] quit
[*DeviceA] commit
- Configure IKE DPD.
[~DeviceA] ike dpd 100
[*DeviceA] commit
- Configure the IPsec policy with the name being map1 and number being 10.
[~DeviceA] ipsec policy map1 10 isakmp
[*DeviceA-ipsec-policy-isakmp-map1-10] security acl 3000
[*DeviceA-ipsec-policy-isakmp-map1-10] proposal tran1
[*DeviceA-ipsec-policy-isakmp-map1-10] ike-peer b
[*DeviceA-ipsec-policy-isakmp-map1-10] quit
[*DeviceA] commit
- Configure the IPsec service instance group.
[~DeviceA] service-location 1
[*DeviceA-service-location-1] location slot 1
[*DeviceA-service-location-1] commit
[~DeviceA-service-location-1] quit
[~DeviceA] service-instance-group group1
[*DeviceA-service-instance-group-group1] service-location 1
[*DeviceA-service-instance-group-group1] commit
[~DeviceA-service-instance-group-group1] quit
- Apply IPsec policy map1 to Tunnel 10.
[~DeviceA] interface Tunnel 10
[~DeviceA-Tunnel10] ipsec policy map1 service-instance-group group1
[*DeviceA-Tunnel10] quit
[*DeviceA] commit
- Configure Device B.
- Set the IP addresses of interfaces.
Set the IP address of GE 0/1/1.
<DeviceB> system-view
[~DeviceB] interface gigabitethernet 0/1/1
[~DeviceB-GigabitEthernet0/1/1] ip address 10.1.2.1 24
[*DeviceB-GigabitEthernet0/1/1] quit
[*DeviceB] commit
Set the IP address of GE 0/1/2
[~DeviceB] interface gigabitethernet 0/1/2
[~DeviceB-GigabitEthernet0/1/2] ip address 172.16.169.1 24
[*DeviceB-GigabitEthernet0/1/2] quit
[*DeviceB] commit
- Create and configure the tunnel interface.
[~DeviceB] interface Tunnel 10
[~DeviceB-Tunnel10] tunnel-protocol ipsec
[*DeviceB-Tunnel10] ip address 192.168.1.2 32
[*DeviceB-Tunnel10] quit
[*DeviceB] commit
- Configure the static route to reach network A. The outbound interface is Tunnel 10 and the next hop to 192.168.1.1 (the IP address of the tunnel interface of the peer). Assume that the next hop of Device B is 172.16.169.2/24.

When configuring static routes to direct IPsec traffic into IPsec tunnels, specify an IPsec tunnel interface as the outbound interface of the static routes and specify a next hop address.
[~DeviceB] ip route-static 10.1.1.0 255.255.255.0 Tunnel 10 192.168.1.1
[*DeviceB] ip route-static 192.168.1.1 255.255.255.255 172.16.169.2
[*DeviceB] commit
- Configure advanced ACL 3000 to permit PCB to access PCA.
[~DeviceB] acl 3000
[*DeviceB-acl-adv-3000] rule permit ip source 10.1.2.2 0.0.0.0 destination 10.1.1.2 0.0.0.0
[*DeviceB-acl-adv-3000] quit
[*DeviceB] commit
- Configure the IPsec proposal with the name as tran1.
[~DeviceB] ipsec proposal tran1
[*DeviceB-ipsec-proposal-tran1] encapsulation-mode tunnel
[*DeviceB-ipsec-proposal-tran1] transform esp
[*DeviceB-ipsec-proposal-tran1] esp authentication-algorithm sha2-256
[*DeviceB-ipsec-proposal-tran1] esp encryption-algorithm aes 256
[*DeviceB-ipsec-proposal-tran1] quit
[*DeviceB] commit
- Configure the IKE proposal with the number as 10.
[~DeviceB] ike proposal 10
[*DeviceB-ike-proposal-10] authentication-method pre-share
[*DeviceB-ike-proposal-10] authentication-algorithm sha2-256
[*DeviceB-ike-proposal-10] dh group14
[*DeviceB-ike-proposal-10] quit
[*DeviceB] commit
- Configure the IKE peer with the name as a.
[~DeviceB] ike peer a
[*DeviceB-ike-peer-a] ike-proposal 10
[*DeviceB-ike-peer-a] remote-address 192.168.1.1
[*DeviceB-ike-peer-a] pre-shared-key abcde
[*DeviceB-ike-peer-a] quit
[*DeviceB] commit
- Configure IKE DPD.
[~DeviceB] ike dpd 100
[*DeviceB] commit
- Configure the IPsec policy with the name as map1 and number as 10.
[~DeviceB] ipsec policy map1 10 isakmp
[*DeviceB-ipsec-policy-isakmp-map1-10] security acl 3000
[*DeviceB-ipsec-policy-isakmp-map1-10] proposal tran1
[*DeviceB-ipsec-policy-isakmp-map1-10] ike-peer a
[*DeviceB-ipsec-policy-isakmp-map1-10] quit
[*DeviceB] commit
- Configure the IPsec service instance group.
[~DeviceB] service-location 1
[*DeviceB-service-location-1] location slot 1
[*DeviceB-service-location-1] commit
[~DeviceB-service-location-1] quit
[~DeviceB] service-instance-group group1
[*DeviceB-service-instance-group-group1] service-location 1
[*DeviceB-service-instance-group-group1] commit
[~DeviceB-service-instance-group-group1] quit
- Apply security policy map1 to Tunnel 10.
[~DeviceB] interface Tunnel10
[~DeviceB-Tunnel10] ipsec policy map1 service-instance-group group1
[*DeviceB-Tunnel10] quit
[*DeviceB] commit
Configuration Files
Device A configuration file
#
sysname DeviceA
#
ike dpd 100
#
acl number 3000
rule 5 permit ip source 10.1.1.2 0 destination 10.1.2.2 0
#
ike proposal 10
encryption-algorithm aes-cbc 256
dh group14
authentication-algorithm sha2-256
integrity-algorithm hmac-sha2-256
#
ike peer b
pre-shared-key cipher %^%#CScZ$9Z&w+@:5+7>\{;7UI~3"Wcx/P#,,FT<6t!8%^%#
ike-proposal 10
remote-address 192.168.1.2
#
service-location 1
location slot 1
#
service-instance-group group1
service-location 1
#
ipsec proposal tran1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes 256
#
ipsec policy map1 10 isakmp
security acl 3000
ike-peer b
proposal tran1
#
interface GigabitEthernet0/1/1
ip address 10.1.1.1 255.255.255.0
#
interface GigabitEthernet0/1/2
ip address 172.16.163.1 255.255.255.0
#
interface Tunnel10
ip address 192.168.1.1 255.255.255.255
tunnel-protocol ipsec
ipsec policy map1 service-instance-group group1
#
ip route-static 10.1.2.0 255.255.255.0 Tunnel 10 192.168.1.2
ip route-static 192.168.1.2 255.255.255.255 172.16.163.2
#
return
Device B configuration file
#
sysname DeviceB
#
ike dpd 100
#
acl number 3000
rule 5 permit ip source 10.1.2.2 0 destination 10.1.1.2 0
#
ike proposal 10
encryption-algorithm aes-cbc 256
dh group14
authentication-algorithm sha2-256
integrity-algorithm hmac-sha2-256
#
ike peer a
pre-shared-key cipher %^%#.EJ~F"jURXr&0--*9[2(uLl^I@0_]XBJe;=-0x,V%^%#
ike-proposal 10
remote-address 192.168.1.1
#
service-location 1
location slot 1
#
service-instance-group group1
service-location 1
#
ipsec proposal tran1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes 256
#
ipsec policy map1 10 isakmp
security acl 3000
ike-peer a
proposal tran1
#
interface GigabitEthernet0/1/1
ip address 10.1.2.1 255.255.255.0
#
interface GigabitEthernet0/1/2
ip address 172.16.169.1 255.255.255.0
#
interface Tunnel10
ip address 192.168.1.2 255.255.255.255
tunnel-protocol ipsec
ipsec policy map1 service-instance-group group1
#
ip route-static 10.1.1.0 255.255.255.0 Tunnel 10 192.168.1.1
ip route-static 192.168.1.1 255.255.255.255 172.16.169.2
#
return

