Example for Configuring IPsec Tunnels Between NetEngine 8000 Fs Using an IPsec Policy Template
You can use an IPsec policy template to configure IPsec tunnels for multiple mobile devices, thereby adding or reducing mobile devices conveniently. The IPsec policy template is configured on the NetEngine 8000 F to receive connections passively, and the IPsec policy is configured on the peer device to initiate connections.
Networking Requirements
As shown in Figure 1, network A, network B, and network C are connected to the Internet through Device A, Device B, and Device C, respectively. Device A, Device B, and Device C are routable to each other.

Interfaces 1 and 2 in this example represent GE 0/1/1 and GE 0/1/2, respectively.
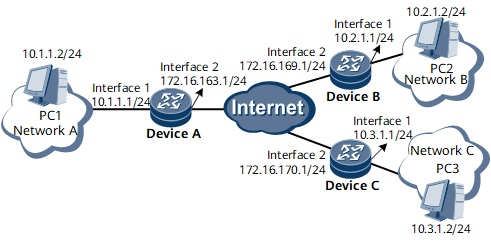
To ensure security, network A must be able to communicate with network B and network C, and network B and network C cannot communicate with each other.
Configuration Roadmap
The configuration roadmap is as follows:
Configure IP addresses for interfaces.
Configure an ACL to define the data flow to be protected.
Configure an IPsec proposal.
Configure an Internet Key Exchange (IKE) proposal.
Configure IKE peers.
Configure an IPsec policy template on Device A. Configure IPsec policies on Device B and Device C.
Configure an IPsec service instance group.
Create and configure a tunnel interface. Apply the IPsec policy to the tunnel interface.
Configure routes (static routes in most cases) on the public network.
Data Preparation
To complete the configuration, you need the following data:
- IP addresses of interfaces
- IP addresses of tunnel interfaces
- IP address segments
- Pre-shared key
- Security protocol, encryption algorithm, and authentication algorithm to be used by an IPsec proposal
- Authentication algorithm to be used by the IKE proposal
Procedure
- Configure device names and IP addresses for interfaces.
For configuration details, see the configuration files in this section.
- Define the data flow to be protected.
# Configure Device A.
[~DeviceA] acl 3000 [*DeviceA-acl-adv-3000] rule permit ip [*DeviceA-acl-adv-3000] quit [*DeviceA] commit

The ACL rule allows all IP packets to pass through, so that peer base stations can be added or removed conveniently. The ACL rule takes effect according to the generated route, therefore avoiding risks.
# Configure Device B.
[~DeviceB] acl 3000 [*DeviceB-acl-adv-3000] rule permit ip source 10.2.1.2 0.0.0.0 destination 10.1.1.2 0.0.0.0 [*DeviceB-acl-adv-3000] quit [*DeviceB] commit
# Configure Device C.
[~DeviceC] acl 3000 [*DeviceC-acl-adv-3000] rule permit ip source 10.3.1.2 0.0.0.0 destination 10.1.1.2 0.0.0.0 [*DeviceC-acl-adv-3000] quit [*DeviceC] commit
- Configure an IPsec proposal.
# Configure Device A.
[~DeviceA] ipsec proposal tran1 [*DeviceA-ipsec-proposal-tran1] encapsulation-mode tunnel [*DeviceA-ipsec-proposal-tran1] transform esp [*DeviceA-ipsec-proposal-tran1] esp authentication-algorithm sha2-256 [*DeviceA-ipsec-proposal-tran1] esp encryption-algorithm aes 256 [*DeviceA-ipsec-proposal-tran1] quit [*DeviceA] commit
# Configure Device B.
[~DeviceB] ipsec proposal tran1 [*DeviceB-ipsec-proposal-tran1] encapsulation-mode tunnel [*DeviceB-ipsec-proposal-tran1] transform esp [*DeviceB-ipsec-proposal-tran1] esp authentication-algorithm sha2-256 [*DeviceB-ipsec-proposal-tran1] esp encryption-algorithm aes 256 [*DeviceB-ipsec-proposal-tran1] quit [*DeviceB] commit
# Configure Device C.
[~DeviceC] ipsec proposal tran1 [*DeviceC-ipsec-proposal-tran1] encapsulation-mode tunnel [*DeviceC-ipsec-proposal-tran1] transform esp [*DeviceC-ipsec-proposal-tran1] esp authentication-algorithm sha2-256 [*DeviceC-ipsec-proposal-tran1] esp encryption-algorithm aes 256 [*DeviceC-ipsec-proposal-tran1] quit [*DeviceC] commit

ESP is the default security protocol, and the tunnel mode is the default encapsulation mode. They do not need to be configured.
- Configure an IKE proposal.
# Configure Device A.
[~DeviceA] ike proposal 10 [*DeviceA-ike-proposal-10] authentication-method pre-share [*DeviceA-ike-proposal-10] authentication-algorithm sha2-256 [*DeviceA-ike-proposal-10] dh group14 [*DeviceA-ike-proposal-10] quit [*DeviceA] commit
# Configure Device B.
[~DeviceB] ike proposal 10 [*DeviceB-ike-proposal-10] authentication-method pre-share [*DeviceB-ike-proposal-10] authentication-algorithm sha2-256 [*DeviceB-ike-proposal-10] dh group14 [*DeviceB-ike-proposal-10] quit [*DeviceB] commit
# Configure Device C.
[~DeviceC] ike proposal 10 [*DeviceC-ike-proposal-10] authentication-method pre-share [*DeviceC-ike-proposal-10] authentication-algorithm sha2-256 [*DeviceC-ike-proposal-10] dh group14 [*DeviceC-ike-proposal-10] quit [*DeviceC] commit

Pre-shared key is the default authentication method and does not need to be configured.
- Configure IKE peers.

- The setting of the pre-shared key should be identical with that on the peer device.
# Configure Device A.
[~DeviceA] ike peer p1 [*DeviceA-ike-peer-p1] ike-proposal 10 [*DeviceA-ike-peer-p1] pre-shared-key abcde [*DeviceA-ike-peer-p1] quit [*DeviceA] commit
# Configure Device B.
[~DeviceB] ike peer a [*DeviceB-ike-peer-a] ike-proposal 10 [*DeviceB-ike-peer-a] remote-address 192.168.1.1 [*DeviceB-ike-peer-a] pre-shared-key abcde [*DeviceB-ike-peer-a] quit [*DeviceB] commit
# Configure Device C.
[~DeviceC] ike peer a [*DeviceC-ike-peer-a] ike-proposal 10 [*DeviceC-ike-peer-a] remote-address 192.168.1.1 [*DeviceC-ike-peer-a] pre-shared-key abcde [*DeviceC-ike-peer-a] quit [*DeviceC] commit
- Configure peer keepalive detection.
# Configure Device A.
[~DeviceA] ike dpd interval 10 10 [*DeviceA] commit
# Configure Device B.
[~DeviceB] ike dpd interval 10 10 [*DeviceB] commit
# Configure Device C.
[~DeviceC] ike dpd interval 10 10 [*DeviceC] commit
- Configure an IPsec policy template and IPsec policy.
# Configure an IPsec policy template on Device A and reference the IPsec policy template in the IPsec policy.
[~DeviceA] ipsec policy-template map_temp 1 [*DeviceA-ipsec-policy-templet-map_temp-1] security acl 3000 [*DeviceA-ipsec-policy-templet-map_temp-1] proposal tran1 [*DeviceA-ipsec-policy-templet-map_temp-1] ike-peer p1 [*DeviceA-ipsec-policy-templet-map_temp-1] quit [*DeviceA] commit [~DeviceA] ipsec policy map1 10 isakmp template map_temp [*DeviceA] commit

The name of the IPsec policy cannot be the same as that of the referenced policy template.
# Configure an IPsec policy on Device B.
[~DeviceB] ipsec policy map1 10 isakmp [*DeviceB-ipsec-policy-isakmp-map1-10] security acl 3000 [*DeviceB-ipsec-policy-isakmp-map1-10] proposal tran1 [*DeviceB-ipsec-policy-isakmp-map1-10] ike-peer a [*DeviceB-ipsec-policy-isakmp-map1-10] quit [*DeviceB] commit
# Configure an IPsec policy on Device C.
[~DeviceC] ipsec policy map1 10 isakmp [*DeviceC-ipsec-policy-isakmp-map1-10] security acl 3000 [*DeviceC-ipsec-policy-isakmp-map1-10] proposal tran1 [*DeviceC-ipsec-policy-isakmp-map1-10] ike-peer a [*DeviceC-ipsec-policy-isakmp-map1-10] quit [*DeviceC] commit
- Configure an IPsec service instance group.
# Configure Device A.
[~DeviceA] service-location 1 [*DeviceA-service-location-1] location slot 1 [*DeviceA-service-location-1] commit [~DeviceA-service-location-1] quit [~DeviceA] service-instance-group group1 [*DeviceA-service-instance-group-group1] service-location 1 [*DeviceA-service-instance-group-group1] commit [~DeviceA-service-instance-group-group1] quit# Configure Device B.
[~DeviceB] service-location 1 [*DeviceB-service-location-1] location slot 1 [*DeviceB-service-location-1] commit [~DeviceB-service-location-1] quit [~DeviceB] service-instance-group group1 [*DeviceB-service-instance-group-group1] service-location 1 [*DeviceB-service-instance-group-group1] commit [~DeviceB-service-instance-group-group1] quit# Configure Device C.
[~DeviceC] service-location 1 [*DeviceC-service-location-1] location slot 1 [*DeviceC-service-location-1] commit [~DeviceC-service-location-1] quit [~DeviceC] service-instance-group group1 [*DeviceC-service-instance-group-group1] service-location 1 [*DeviceC-service-instance-group-group1] commit [~DeviceC-service-instance-group-group1] quit - Create a tunnel interface and configure attributes for the tunnel interface.
# Configure Device A.
[~DeviceA] interface Tunnel 10 [*DeviceA-Tunnel10] tunnel-protocol ipsec [*DeviceA-Tunnel10] ip address 192.168.1.1 32 [~DeviceA-Tunnel10] ipsec policy map1 service-instance-group group1 [*DeviceA-Tunnel10] quit [*DeviceA] commit
# Configure Device B.
[~DeviceB] interface Tunnel 10 [*DeviceB-Tunnel10] tunnel-protocol ipsec [*DeviceB-Tunnel10] ip address 192.168.2.1 32 [~DeviceB-Tunnel10] ipsec policy map1 service-instance-group group1 [*DeviceB-Tunnel10] quit [*DeviceB] commit
# Configure Device C.
[~DeviceC] interface Tunnel 10 [*DeviceC-Tunnel10] tunnel-protocol ipsec [*DeviceC-Tunnel10] ip address 192.168.3.1 32 [~DeviceC-Tunnel10] ipsec policy map1 service-instance-group group1 [*DeviceC-Tunnel10] quit [*DeviceC] commit
- Configure static routes.
Static routes are used to import data traffic to the IPsec tunnel.
# Configure Device A. Assume that the next hop IP address of Device A is 172.16.163.2.
[~DeviceA] ip route-static 0.0.0.0 0.0.0.0 172.16.163.2 [*DeviceA] commit
# Configure Device B. Assume that the next hop IP address of Device B is 172.16.169.2.
[~DeviceB] ip route-static 10.1.1.0 255.255.255.0 Tunnel 10 192.168.1.1 [*DeviceB] ip route-static 192.168.1.1 255.255.255.255 172.16.169.2 [*DeviceB] commit
# Configure Device C. Assume that the next hop IP address of Device C is 172.16.170.2.
[~DeviceC] ip route-static 10.1.1.0 255.255.255.0 Tunnel 10 192.168.1.1 [*DeviceC] ip route-static 192.168.1.1 255.255.255.255 172.16.170.2 [*DeviceC] commit
Configuration Files
Device A configuration file
# sysname DeviceA # ike dpd interval 10 10 # acl number 3000 rule 5 permit ip # ike proposal 10 encryption-algorithm aes-cbc 256 dh group14 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256 # ike peer p1 pre-shared-key cipher %^%#.EJ~F"jURXr&0--*9[2(uLl^I@0_]XBJe;=-0x,V%^%# ike-proposal 10 # ipsec proposal tran1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes 256 # ipsec policy-template map_temp 1 security acl 3000 ike-peer p1 proposal tran1 # service-location 1 location slot 1 # service-instance-group group1 service-location 1 # ipsec policy map1 10 isakmp template map_temp # interface GigabitEthernet0/1/1 undo shutdown ip address 10.1.1.1 255.255.255.0 # interface GigabitEthernet0/1/2 undo shutdown ip address 172.16.163.1 255.255.255.0 # interface Tunnel10 ip address 192.168.1.1 255.255.255.0 tunnel-protocol ipsec ipsec policy map1 service-instance-group group1 # ip route-static 0.0.0.0 0.0.0.0 172.16.163.2 # return
Device B configuration file
# sysname DeviceB # ike dpd interval 10 10 # acl number 3000 rule 5 permit ip source 10.1.2.2 0 destination 10.1.1.2 0 # ike proposal 10 encryption-algorithm aes-cbc 256 dh group14 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256 # ike peer a pre-shared-key cipher %^%#.EJ~F"jURXr&0--*9[2(uLl^I@0_]XBJe;=-0x,V%^%# ike-proposal 10 remote-address 192.168.1.1 # service-location 1 location slot 1 # service-instance-group group1 service-location 1 # ipsec proposal tran1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes 256 # ipsec policy map1 10 isakmp security acl 3000 ike-peer a proposal tran1 # interface GigabitEthernet0/1/1 undo shutdown ip address 10.1.2.1 255.255.255.0 # interface GigabitEthernet0/1/2 undo shutdown ip address 172.16.169.1 255.255.255.0 # interface Tunnel10 ip address 192.168.1.2 255.255.255.255 tunnel-protocol ipsec ipsec policy map1 service-instance-group group1 # ip route-static 10.1.1.0 255.255.255.0 Tunnel 10 192.168.1.1 ip route-static 192.168.1.1 255.255.255.255 172.16.169.2 # return
Device C configuration file.
# sysname DeviceC # ike dpd interval 10 10 # acl number 3000 rule 5 permit ip source 10.1.3.2 0 destination 10.1.1.2 0 # ike proposal 10 encryption-algorithm aes-cbc 256 dh group14 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256 # ike peer a pre-shared-key cipher %^%#.EJ~F"jURXr&0--*9[2(uLl^I@0_]XBJe;=-0x,V%^%# ike-proposal 10 remote-address 192.168.1.1 # service-location 1 location slot 1 # service-instance-group group1 service-location 1 # ipsec proposal tran1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes 256 # ipsec policy map1 10 isakmp security acl 3000 ike-peer a proposal tran1 # interface GigabitEthernet0/1/1 undo shutdown ip address 10.1.3.1 255.255.255.0 # interface GigabitEthernet0/1/2 undo shutdown ip address 172.16.170.1 255.255.255.0 # interface Tunnel10 ip address 192.168.1.3 255.255.255.255 tunnel-protocol ipsec ipsec policy map1 service-instance-group group1 # ip route-static 10.1.1.0 255.255.255.0 Tunnel 10 192.168.1.1 ip route-static 192.168.1.1 255.255.255.255 172.16.170.2 # return