Example for Configuring Inter-Board LDP over GRE over IPsec
Context

Interfaces 1 and 2 in this example represent GE 0/1/0 and GE 0/1/1, respectively.
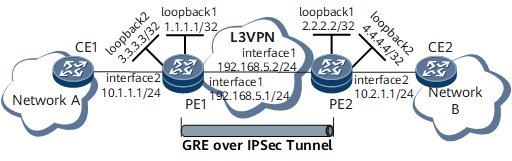
The networking is described as follows:
Interface GE 0/1/0 of PE1 on the public network side is connected to PE2, and interface GE 0/1/1 on the private network side is connected to CE1.
Interface GE 0/1/0 of PE2 on the public network side is connected to PE1, and interface GE 0/1/1 on the private network side is connected to CE2.
To improve communication security between PE1 and PE2, configure a GRE over IPsec tunnel between PE1 and PE2.
Configuration Roadmap
This section uses IPsec in IKE mode as an example to describe how to configure LDP over GRE over IPsec. The tunnel mode is used for encapsulation. The configuration roadmap is as follows:
Allocate IP addresses to interfaces.
Configure a loopback interface and configure GRE for the loopback interface.
Create a tunnel interface and configure GRE for the tunnel interface.
- Configure IPsec. The following steps are involved:
Configure an ACL to define the data flow to be protected.
(Recommended) Configure the DPD.
Configure an IKE proposal.
Configure IKE peers.
Configure an IPsec proposal.
Configure an IPsec policy.
Configure an IPsec service instance group.
Create a tunnel interface and configure attributes for the tunnel interface.
Apply the IPsec policy to the tunnel interface.
Configure a static route to divert IPsec traffic.
Create a loopback interface and configure IS-IS for the loopback interface and GRE-enabled tunnel interface.
Establish an IBGP peer relationship between PE1 and PE2.
Enable MPLS and MPLS LDP.
Configure VPN instances.
Data Preparation
To complete the configuration, you need the following data:
- IP addresses of interfaces
- IPsec-related data, mainly including:
DPD data
ACL number
IP address segments
Pre-shared key
Authentication algorithm used by the IKE proposal
Security protocol, encryption algorithm, and authentication algorithm to be used by an IPsec proposal
IP addresses of tunnel interfaces
- L3VPN data, including the IS-IS system-ID, MPLS LSR ID, VPN instance name, RD, and VPN target
Procedure
- Configure PE1 and PE2 as follows:
Item
PE1
PE2
1. Configure interface IP addresses.
interface GigabitEthernet0/1/0 undo shutdown ip address 192.168.5.1 255.255.255.0 # interface LoopBack1 ip address 1.1.1.1 255.255.255.255 # interface LoopBack2 ip address 3.3.3.3 255.255.255.255interface GigabitEthernet0/1/0 undo shutdown ip address 192.168.5.2 255.255.255.0 # interface LoopBack1 ip address 2.2.2.2 255.255.255.255 # interface LoopBack2 ip address 4.4.4.4 255.255.255.2552. Configure the GRE tunnel interfaces.
interface LoopBack1 binding tunnel gre # interface Tunnel 802 ip address 172.16.5.1 255.255.255.0 //This address has no actual meaning. It is used to enable the interface to enter the Up state. tunnel-protocol gre source LoopBack1 destination 2.2.2.2
interface LoopBack1 binding tunnel gre # interface Tunnel 502 ip address 172.16.5.2 255.255.255.0 //This address has no actual meaning. It is used to enable the interface to enter the Up state. tunnel-protocol gre source LoopBack1 destination 1.1.1.1
4. Enable DPD.
ike dpd interval 10 10 //You are suggested to deploy the DPD function.
ike dpd interval 10 10 //You are suggested to deploy the DPD function.
5. Configure an ACL to define the data flow to be protected.
acl number 3100 rule 5 permit gre source 1.1.1.1 0 destination 2.2.2.2 0
acl number 3100 rule 5 permit gre source 2.2.2.2 0 destination 1.1.1.1 0
6. Configure the IKE proposal and IKE peer.
ike proposal 1 encryption-algorithm aes-cbc 256 dh group2 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256 # ike peer pe pre-shared-key %$%$0\WT%.iDi6%K-f)_^mQ6,.2n%$%$ //Configure the PSK as 1234567890 in ciphertext. ike-proposal 1 remote-address 172.17.5.2
ike proposal 1 encryption-algorithm aes-cbc 256 dh group2 authentication-algorithm sha2-256 integrity-algorithm hmac-sha2-256 # ike peer pe pre-shared-key %$%$0\WT%.iDi6%K-f)_^mQ6,.2n%$%$ //Configure the PSK as 1234567890 in ciphertext. ike-proposal 1 remote-address 172.17.5.1
7. Configure Service-instance-group.
service-location 1 location slot 1 # service-instance-group group1 service-location 1service-location 1 location slot 1 # service-instance-group group1 service-location 18. Configure the IPsec tunnel.
ipsec proposal zh //Configure the IPsec proposal. esp authentication-algorithm sha1 esp encryption-algorithm aes 256 # ipsec policy zh 10 isakmp //Configure the IPsec policy. security acl 3100 ike-peer pe proposal zh # interface Tunnel 5 //Configure the IPsec tunnel. ip address 172.17.5.1 255.255.255.0 tunnel-protocol ipsec ipsec policy zh service-instance-group 1ipsec proposal zh //Configure the IPsec proposal. esp authentication-algorithm sha1 esp encryption-algorithm aes 256 # ipsec policy zh 10 isakmp //Configure the IPsec policy. security acl 3100 ike-peer pe proposal zh # interface Tunnel 5 //Configure the IPsec tunnel. ip address 172.17.5.2 255.255.255.0 tunnel-protocol ipsec ipsec policy zh service-instance-group 19. Configure the diversion routes.
ip route-static 2.2.2.2 255.255.255.255 Tunnel5 172.17.5.2 //Divert traffic to the IPsec tunnel for encryption. ip route-static 172.17.5.2 255.255.255.255 GigabitEthernet0/1/0 192.168.5.2 //Divert the traffic encrypted by IPsec to the actual physical outbound interface.ip route-static 1.1.1.1 255.255.255.255 Tunnel5 172.17.5.1 //Divert traffic to the IPsec tunnel for encryption. ip route-static 172.17.5.1 255.255.255.255 GigabitEthernet0/1/0 192.168.5.1 //Divert the traffic encrypted by IPsec to the actual physical outbound interface.10. Configure IS-IS.
isis 1 is-level level-2 network-entity 01.0000.0000.0003.00 # interface LoopBack2 isis enable 1 # interface Tunnel802 isis enable 1
isis 1 is-level level-2 network-entity 01.0000.0000.0005.00 # interface LoopBack2 isis enable 1 # interface Tunnel502 isis enable 1
11. Configure VPNs.
ip vpn-instance ipsec_vpn ipv4-family route-distinguisher 100:100 vpn-target 200:200 export-extcommunity vpn-target 200:200 import-extcommunity # interface GigabitEthernet0/1/1 undo shutdown ip binding vpn-instance ipsec_vpn ip address 10.1.1.1 255.255.255.0ip vpn-instance ipsec_vpn ipv4-family route-distinguisher 100:100 vpn-target 200:200 export-extcommunity vpn-target 200:200 import-extcommunity # interface GigabitEthernet0/1/1 undo shutdown ip binding vpn-instance ipsec_vpn ip address 10.2.1.1 255.255.255.012. Configure BGP.
bgp 100 peer 4.4.4.4 as-number 100 peer 4.4.4.4 connect-interface LoopBack2 # ipv4-family unicast undo synchronization peer 4.4.4.4 enable # ipv4-family vpnv4 policy vpn-target peer 4.4.4.4 enable # ipv4-family vpn-instance ipsec_vpn import-route direct
bgp 100 peer 3.3.3.3 as-number 100 peer 3.3.3.3 connect-interface LoopBack2 # ipv4-family unicast undo synchronization peer 3.3.3.3 enable # ipv4-family vpnv4 policy vpn-target peer 3.3.3.3 enable # ipv4-family vpn-instance ipsec_vpn import-route direct
13. Configure the MPLS tunnel.
mpls lsr-id 3.3.3.3 mpls # mpls ldp # interface Tunnel802 //Enable MPLS LDP for the GRE tunnel interface. mpls mpls ldp
mpls lsr-id 4.4.4.4 mpls # mpls ldp # interface Tunnel502 //Enable MPLS LDP for the GRE tunnel interface. mpls mpls ldp