Overview of MAC Flapping-based Loop Detection
This section describes the MAC flapping-based loop detection application on a virtual private LAN service (VPLS) network in terms of background, introduction, and basic concepts.
Background
Generally, redundant links are used on an Ethernet network to provide link backup and enhance network reliability. Redundant links, however, may produce loops and cause broadcast storms and MAC address entry flapping. As a result, the communication quality deteriorates, and communication services may even be interrupted. To eliminate loops on the network, the spanning tree protocols or Layer 2 loop detection technology was introduced. If you want to apply a spanning tree protocol, the protocol must be supported and you need to configure it on each user network device. If you want to apply the Layer 2 loop detection technology, user network devices must allow Layer 2 loop detection packets to pass. Therefore, the spanning tree protocols or the Layer 2 loop detection technology cannot be used to eliminate loops on user networks with unknown connections or user networks that do not support the spanning tree protocols or Layer 2 loop detection technology.
MAC flapping-based loop detection is introduced to address this problem. It does not require protocol packet negotiation between devices. A device independently checks whether a loop occurs on the network based on MAC address entry flapping.
Introduction
Devices can block redundant links based on the frequency of MAC address entry flapping to eliminate loops on the network.
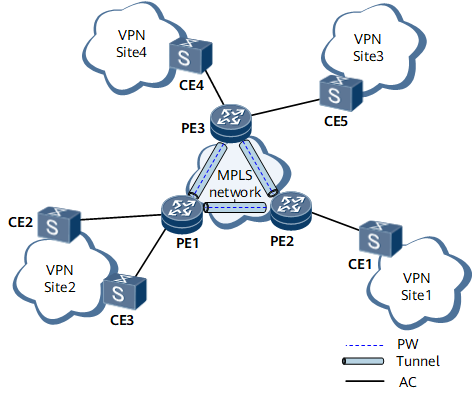
On the virtual private LAN service (VPLS) network shown in Figure 1, pseudo wires (PWs) are established over Multiprotocol Label Switching (MPLS) tunnels between virtual private network (VPN) sites to transparently transmit Layer 2 packets. When forwarding packets, the provider edges (PEs) learn the source MAC addresses of the packets, create MAC address entries, and establish mapping between the MAC addresses and AC interfaces and mapping between the MAC addresses and PWs.
- Blocking interfaces based on their blocking priorities: If a device detects a loop, it blocks the interface with a lower blocking priority.
- Blocking interfaces based on their trusted or untrusted states: If a device detects a loop, it blocks the untrusted interface.
MAC flapping-based loop detection can also detect PW-side loops. The principles of blocking PWs are similar to those of blocking AC interfaces.

After MAC flapping-based loop detection is configured on a device and the device receives packets with fake source MAC addresses from attackers, the device may mistakenly conclude that a loop has occurred and block an interface based on the configured blocking policy. Therefore, key user traffic may be blocked. It is recommended that you disable MAC flapping-based loop detection on properly running devices. If you have to use MAC flapping-based loop detection to detect whether links operate properly during site deployment, be sure to disable this function after this stage.
Basic Concepts
-
If a device detects a specified number of MAC address entry flaps within a detection cycle, the device concludes that a loop has occurred. The detection cycle is configurable.
-
If a device concludes that a loop has occurred, it blocks an interface or PW for a specified period of time.
-
After an interface or a PW is blocked and then unblocked, if the total number of times that loops occur exceeds the configured maximum number, the interface or PW is permanently blocked.
An interface or PW that is permanently blocked can be unblocked only manually.
-
MAC flapping-based loop detection has the following blocking policies:
Blocking interfaces based on their blocking priorities
The blocking priority of an interface can be configured. When detecting a loop, a device blocks the interface with a lower blocking priority.
Blocking interfaces based on their trusted or untrusted states (accurate blocking)
If a dynamic MAC address entry remains the same in the MAC address table within a specified period and is not deleted, the outbound interface in the MAC address entry is trusted. When detecting a loop, a device blocks an interface that is not trusted.
A device on which MAC flapping-based loop detection is deployed blocks PWs based only on the blocking priorities of the PWs. If the device detects a loop, it blocks the PW with a lower blocking priority.
-
After MAC flapping-based loop detection is deployed on a device and the device detects a loop, the device blocks an AC interface with a lower blocking priority by default. However, MAC address entries of interfaces without loops may change due to the impact from a remote loop, and traffic over the interfaces with lower blocking priorities is interrupted. To address this problem, deploy accurate blocking of MAC flapping-based loop detection. Accurate blocking determines trusted and untrusted interfaces by analyzing the frequency of MAC address entry flapping. When a MAC address entry changes repeatedly, accurate blocking can accurately locate and block the interface with a loop, which is an untrusted interface.