IPv4 Management Plane Access Control
Security Policy
Management Plane Access Control (MPAC) enhances system security by protecting devices against Denial of Service (DoS) attacks.
In a common deployment scenario, the router may run multiple services at the same time, such as Layer 2 services MSTP, RRPP, routing services OSPF and BGP, MPLS services LDP and RSVP, system service TFTP server, and diagnostic functions ping and tracert.
This enables attackers to send various attack packets to the router. Unless protective features such as MPAC are enabled, the router sends packets destined for its interfaces (including the loopback interface) directly to the CPU without any filtering. As a result, CPU and system resources are wasted and the system comes under DoS attacks.
To prevent such attacks, define an MPAC policy to filter packets.
The NetEngine 8000 F supports definitions of Management Plane Access Control (MPAC) policies that can be applied to sub-interfaces, to interfaces, or globally on the NetEngine 8000 F.
After you define the rules for an MPAC policy, the NetEngine 8000 F filters packets destined for the CPU. If no such policy is defined, the CPU remains vulnerable to attacks.
Attack Modes
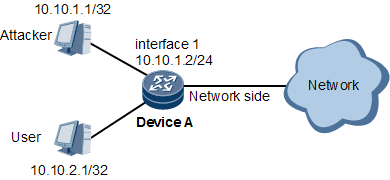
To prevent an attacker from sending various types of TCP/IP attack packets to paralyze Device A, MPAC is deployed on Device A, as shown in Figure 1.
Configuration and Maintenance Methods
Configure IPv4 MPAC on Device A.
<DeviceA> system-view [~DeviceA] service-security policy ipv4 test [*DeviceA-service-sec-test] rule 10 deny protocol ip source-ip 10.10.1.1 0 [*DeviceA-service-sec-test] step 10 [*DeviceA-service-sec-test] description rule 10 is deny ip packet which from 10.10.1.1 [*DeviceA-service-sec-test] commit [~DeviceA-service-sec-test] quit [~DeviceA] service-security global-binding ipv4 test [*DeviceA] commit [~DeviceA] interface gigabitethernet 0/1/0 [~DeviceA-GigabitEthernet0/1/0] service-security binding ipv4 test [*DeviceA-GigabitEthernet0/1/0] commit
Configuration and Maintenance Suggestions
None.