Configuring Basic SRv6 SFC Functions
This section describes how to configure basic Service Function Chaining (SFC) functions based on SRv6 TE Policy.
Prerequisites
Before configuring basic SRv6 SFC functions, complete the following task:
- Configure IS-IS to ensure IPv6 connectivity between the SC, SFFs, and tail end.
- (Optional) Configure VPN instances for SRv6 nodes as needed.
- Configure basic SRv6 functions on the network, a static End SID for each SRv6 node, and End.DT4 SIDs for the IPv4 public network instances or VPN instances on the SC and tail end.
Context
SFC logically connects services on network devices to provide an ordered service set for the application layer. By adding service function path (SFP) information in original packets, SFC enables packets to pass through service functions (SFs) along a specified path.
By using segment lists, an SRv6 TE Policy instructs network devices to forward traffic along a specified path. This mechanism is suitable for implementing SFC. Specifically, if a data packet is steered into an SRv6 TE Policy, the headend adds the segment lists of the SRv6 TE Policy to the data packet, and other devices on the network execute the instructions embedded in the segment lists.
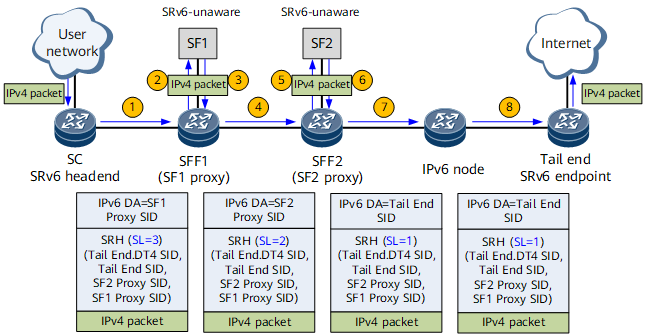
On the network shown in Figure 1, SF1 and SF2 are SRv6-unaware SFs. To implement SFC, SF proxy must be configured on SFF1 and SFF2, and SRv6 SIDs must be allocated to SF1 and SF2 proxies. On the SC, the SF1 Proxy SID, SF2 Proxy SID, and Tail End SID form a segment list of an SRv6 TE Policy. The SRv6 TE Policy functions as an SFP.
Procedure
- Manually configure an SRv6 TE Policy on the SC or use a controller to deliver an SRv6 TE Policy to the SC. The segment list of the SRv6 TE Policy consists of the SF1 Proxy SID, SF2 Proxy SID, and Tail-End SID.
- Configure a traffic policy on the SC to redirect traffic to the SRv6 TE Policy.
- Configure an SFF.
- Configure the tail end.
Verifying the Configuration
- Run the display segment-routing ipv6 local-sid end-as [ sid-value ] forwarding command to check the SRv6 local SID table containing End.AS SIDs.
- Run the display segment-routing ipv6 local-sid end-dt4 [ sid-value | vpn-instance vpn-name ] forwarding command to check the SRv6 local SID table containing End.DT4 SIDs.