Configuring SRv6 SFC Reliability
This section describes how to configure SRv6 SFC reliability.
Context
SFC services are forwarded in serial mode, meaning that a single link or node failure causes SFC service interruptions. To improve service reliability, SRv6 SFC provides backup link protection and bypass link protection.
- In backup link protection, an SF is dual-homed to two SFFs, with one as the master and the other as the backup. The backup SFF is used to protect the primary SFF. If the primary SFF becomes unreachable, services are switched to the backup SFF for processing.
- In bypass link protection, if an SF is unreachable, SFC traffic is switched to the bypass service path, without being processed by the current SF. An SFF usually discards SFC packets if an SF is unreachable. After bypass protection is configured, SFC packets can continue to be forwarded as follows:
- If no bypass SF is available for the current SF, SRv6 forwarding for SFC packets is implemented.
- If the current SF has a bypass SF to provide protection, SFC packets are switched to the bypass SF for processing.
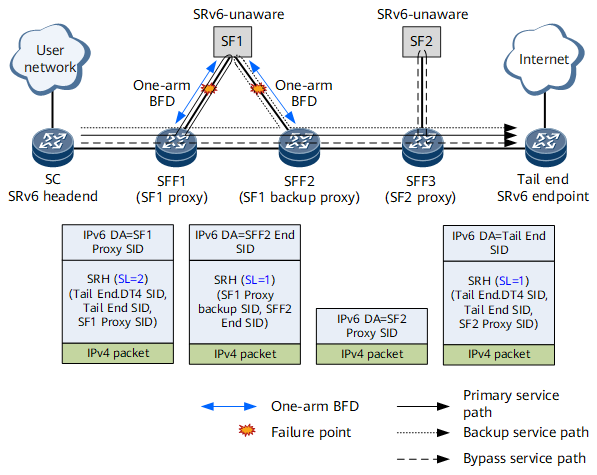
These protection schemes can be selected according to specific SFC networking scenarios. The following describes how to configure SRv6 SFC reliability, using the network shown in Figure 1 as an example. In Figure 1, SF1 is dual-homed to SFF1 and SFF2, and has a bypass SF – SF2.
Configuration roadmap:
- Configure a backup path for protection. Because SF1 is dual-homed to SFF1 and SFF2, SFF1 and SFF2 can provide protection for each other. Specifically, the same SF1 Proxy SID of the End.AS type needs to be configured on SFF1 and SFF2 to implement the anycast function. (For ease of description, the SF1 Proxy SID on SFF2 in Figure 1 is called SF1 Backup Proxy SID.) In addition, SFF1 and SFF2 need to be configured as peers of each other. The peer SID of SFF1 is the End SID of SFF2, and the peer SID of SFF2 is the End SID of SFF1.
- Configure a bypass service path by using SF2 to protect SF1. Specifically, configure a bypass protection SID for the SF1 Proxy SID, and configure the SF2 Proxy SID on SFF3.
- Configure one-arm BFD on SFF1 and SFF2 to detect SF1 reachability.
- If one-arm BFD on SFF1 detects that SF1 is unreachable, the SFC traffic is switched to the backup service path. SFF1 replaces the original SRv6 segment list with the SF1 Proxy Backup SID and SFF2 End SID, and forwards the SFC packet to SFF2. After receiving the packet, SFF2 identifies that both the SF1 Proxy Backup SID and SFF2 End SID are its own SIDs. SFF2 then forwards the packet to SF1 based on the SF1 Proxy Backup SID.
- SFC traffic is switched to SFF2 if one-arm BFD on SFF1 detects that SF1 is unreachable. If one-arm BFD on SFF2 also detects that SF1 is unreachable, the SFC traffic is switched to the bypass service path. SFF2 removes the SRH and searches the IPv6 routing table for packet forwarding, using the SF2 Proxy SID as the destination IPv6 address. After receiving the packet, SFF3 forwards the packet to SF2 based on the SF2 Proxy SID.
Procedure
- Configure SFF backup link protection.
In this example, SF1 is dual-homed to SFF1 and SFF2, which can back up each other. The configurations of SFF1 and SFF2 are symmetrical. In an SF single-homing scenario, backup link protection cannot be implemented.
- Configure SFF bypass protection.
- Configure one-arm BFD.
In this example, one-arm BFD needs to be configured on SFF1 and SFF2. BFD can detect only Layer 3 IP links. If Layer 2 forwarding is used from the SFFs to SFs, BFD cannot be used.
Verifying the Configuration
- Run the display bfd session { all | peer-ip peer-ip [ vpn-instance vpn-name ] } [ verbose ] command to check the BFD session information.