IGMP Policy Control
IGMP policy control restricts or extends IGMP actions, without affecting IGMP implementation. IGMP policy control can be implemented through IGMP-limit, source address-based IGMP message filtering, or group-policy.
-
IGMP-limit is configured on router interfaces connected to users to limit the maximum number of multicast groups, including source-specific multicast groups. This mechanism enables users who have successfully joined multicast groups to enjoy smoother multicast services.
Source address-based IGMP message filtering
This feature allows you to specify multicast source addresses used to filter IGMP messages. This feature prevents forged IGMP message attacks and enhances multicast network security.
-
Group-policy is configured on router interfaces to allow the router to set restrictions on specific multicast groups, so that entries will not be created for the restricted multicast groups. This mechanism improves IGMP security.
IGMP-Limit
When a large number of multicast users request multiple programs simultaneously, excessive bandwidth resources of the router will be exhausted, and the router' s performance will be degraded, deteriorating the multicast service quality.
To prevent this problem, configure IGMP-limit on the router interface to limit the maximum number of IGMP entries on the interface. When receiving an IGMP Report message from a user, the router interface first checks whether the configured maximum number of IGMP entries is reached. If the maximum number is reached, the router interface discards the IGMP Report message and rejects the user. If the maximum number is not reached, the router interface sets up an IGMP membership and forwards data flows of the requested multicast group to the user. This mechanism enables users who have successfully joined multicast groups to enjoy smoother multicast services.
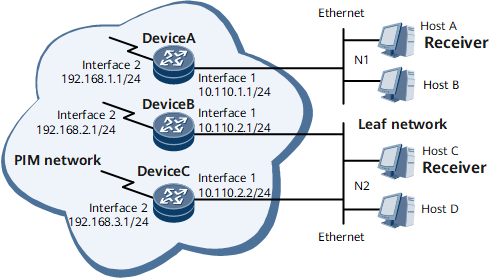
For example, on the network shown in Figure 1, if the maximum number of IGMP entries is set to 1 on Interface 1 of DeviceA, Interface 1 allows only one host to join a multicast group and creates an IGMP entry only for the permitted host.
IGMP-limit allows you to configure a maximum number of IGMP entries on the router interface. After receiving IGMP Report messages, the router interface limits the number of IGMP entries on the interface.
IGMP-limit allows you to configure an ACL on the router interface, so that the interface permits IGMP Report messages that contain a group address, including a source-specific group address, that is in the range specified in the ACL, regardless of whether the configured maximum number of IGMP entries is reached. An IGMP entry that contains a group address in the range specified in the ACL is not counted as one entry on an interface.
Each (*, G) entry is counted as one entry on an interface, and each (S, G) is counted as one entry on an interface.
SSM-mapping (*, G) entries are not counted as entries on an interface, and each (S, G) entry mapped using the SSM-mapping mechanism is counted as one entry on an interface.
Source address-based IGMP message filtering
- Source address-based IGMP message filtering for IGMP Report and Leave messages:
The device permits the message only if the message's source address is 0.0.0.0 or an address on the same network segment as the interface that receives the message.
If ACL rules are configured for filtering IGMP Report and Leave messages, the device determines whether to permit or discard an IGMP Report or Leave message based on the ACL configurations.
- Source address-based IGMP message filtering for IGMP Query messages: A device determines whether to permit or drop an IGMP Query message based on only the configured ACL rules.
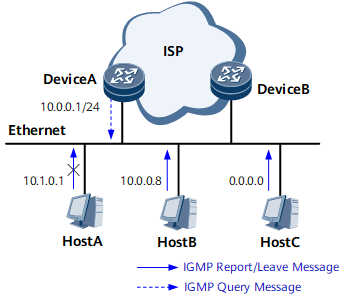
On the network shown in Figure 2, the IP address of DeviceA's interface connected to a user network is 10.0.0.1/24. Host A sends IGMP Report or Leave messages with the source address 11.0.0.1, Host B sends IGMP Report or Leave messages with the source address 10.0.0.8, and Host C sends IGMP Report or Leave messages with the source address 0.0.0.0. If no ACL rule is configured, DeviceA permits the messages received from Host B and Host C and denies the messages received from Host A. If ACL rules are configured, DeviceA determines whether to permit or deny IGMP Report or Leave messages received from Host B and Host C based on the ACL configurations. For example, if an ACL rule only permits IGMP Report or Leave messages with the source address 10.0.0.8, DeviceA permits the IGMP Report or Leave messages received from Host B and denies the IGMP Report or Leave messages received from Host C.
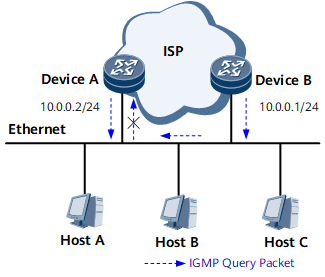
On the network shown in Figure 3, DeviceA is a querier that receives IGMP Report or Leave messages from hosts. If DeviceB constructs bogus IGMP Query messages that contain a source address (such as 10.0.0.1/24) lower than DeviceA's address, Device A will become a non-querier and fail to respond to IGMP Leave messages from hosts. However, DeviceA continues to forward multicast traffic to user hosts who have left, which wastes network resources. To resolve this problem, you can configure an ACL rule on DeviceA to deny the IGMP Query messages with the source address 10.0.0.1/24.
IGMP Group-Policy
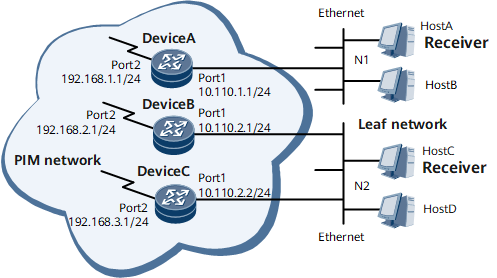
Group-policy is a filtering policy configured on router interfaces. For example, on the network shown in Figure 4, Host A and Host C request to join the multicast group 225.1.1.1. Host B and Host D request to join the multicast group 226.1.1.1. Group-policy is configured on routerA to permit join requests only for the multicast group 225.1.1.1. Then, routerA creates entries for Host A and Host C, but not for Host B or Host D.
To improve network security and facilitate network management, you can use group-policy to disable the router from receiving IGMP Report messages from or forwarding multicast data to specific multicast groups.
Group-policy is implemented through ACL configurations.