Anti-ARP Spoofing Application
Networking Description
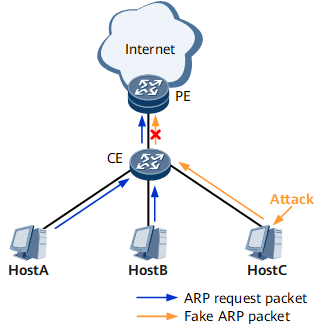
On the network in Figure 1, hosts A, B, and C access the Internet through a gateway provider edge (PE). In normal situations, host A, host B, host C, and the PE all exchange Address Resolution Protocol (ARP) packets so that they can generate ARP entries for each other. When host C is attacked and the attacker constructs bogus ARP packets, host C broadcasts bogus ARP packets to modify ARP entries on host A, host B, or the PE. As a result, attackers can steal information from hosts A and B and prevent hosts A and B from accessing the network normally.
Feature Deployment
Validity check of ARP packets
After validity check of ARP packets is configured on the PE and the PE receives an ARP packet, the PE checks whether the source and destination MAC addresses carried in the Data field match those carried in the Ethernet header. If they match, the PE considers the packet valid and allows the packet to pass through. If they do not match, the PE considers the packet an attack packet and discards it.