Secure Boot
Background
Communication devices consist of multiple embedded computer systems. The software that runs on these devices may be vulnerable to viruses, modified by attackers, or implanted with Trojan horses.
The secure boot function prohibits system boot when system software is damaged, improving system security and reliability.
Related Concepts
Trusted system: A trusted system indicates that system hardware and software are running as designed. The prerequisite for a trusted system is that the system software integrity is high and free of intrusion or unauthorized modification.
Basic Principles
The secure boot function establishes an RoT for the secure boot platform based on the hardware capabilities of a device and an unchangeable initial boot code as well as a key.
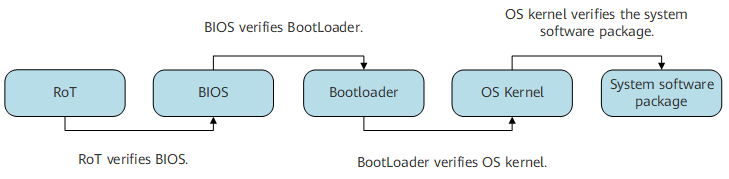
As shown in Figure 1, during system boot, the RoT, BIOS, BootLoader, OS kernel, and system software package are started in order, with each level verifying the file trustworthiness of the next level. If the file trustworthiness of one component fails the verification, the component cannot be started.
If the BIOS or RoT fails the verification, return the device for repair. If the BIOS passes the verification but verification in any of the subsequent steps fails, press Ctrl+B to enter the BootROM menu, replace the system software package, and restart the device.
Benefits
- Trusts the software system of the device that can be properly started.
- Prohibits the startup of the device on which the software system is detected as untrustworthy.