Enterprise Scenario
In the enterprise scenario, IPsec is mainly used to interconnect IPsec VPNs between enterprises or allow mobile office employees to remotely access an enterprise network. The typical applications are the site-to-site VPN and GRE over IPsec. IPsec networking modes in the enterprise scenario are diversified.
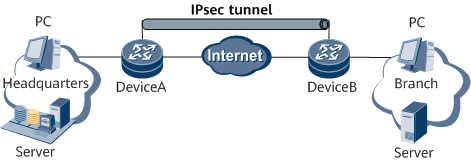
Site-to-Site VPN
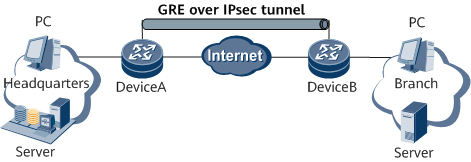
GRE over IPsec
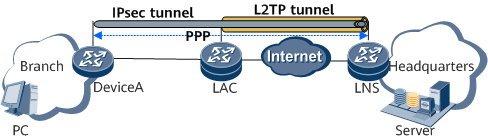
IPsec over L2TP
The IPsec over L2TP mechanism encapsulates packets using IPsec and then L2TP. In this way, the IPsec over L2TP mechanism implements user authentication and address allocation based on L2TP, and ensures security using IPsec.
As shown in Figure 3, Device A, serving as an access server, initiates a PPP session in PPP dial-up mode to trigger the establishment of an L2TP tunnel. After the L2TP tunnel is established, the LNS generates a route to Device A. Device A obtains an IP address and initiates the IPsec tunnel creation.
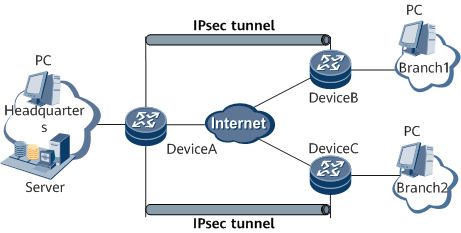
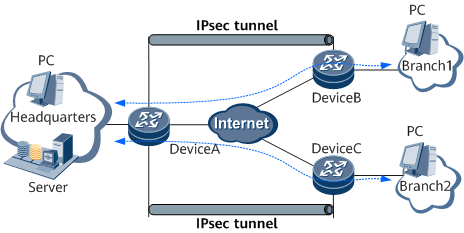
Hub-Spoke VPN
In this networking, you can configure IPsec, or GRE over IPsec based on actual requirements.
Branch networks do not communicate with each other.
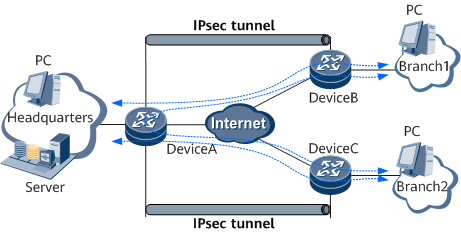
The IPsec VPN is deployed only between the HQ network and the branch networks. That is, service traffic is transmitted only between the HQ network and the branch networks, as shown in Figure 5.Branch networks need to communicate with each other.
Branch networks communicate with each other through the HQ network, as shown in Figure 6.
Internet Access Control for Branch Network Users
In the site-to-site or Hub-Spoke VPN networking, users of the branch networks can access the Internet in following modes:
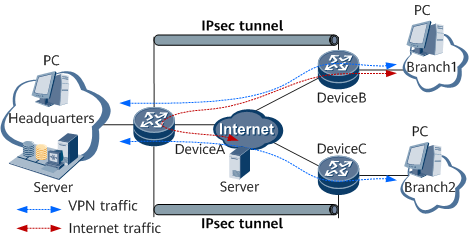
The users of the branch networks access the Internet through the HQ network.
To facilitate unified management and monitoring, the users of the branch networks are prohibited from accessing the Internet using their own gateways, but need to access the HQ network through the VPN and then to the Internet. Generally, traffic from the branch networks to the Internet must experience NAT on the HQ network before reaching the Internet, as shown in Figure 7.The users of the branch networks access the Internet through their own gateways.
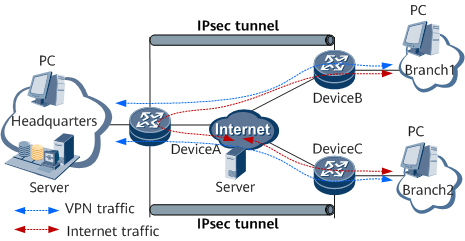
The Internet access traffic of the branch networks is not controlled, as shown in Figure 8.