Key Exchange
In IKE, key exchange needs to be performed between both ends of a tunnel to ensure that they use the same key to encrypt and decrypt data.
Key Exchange Methods
In encryption and authentication using symmetric key, how to share keys securely is an important problem. The following methods can be used to resolve the problem:
Out-of-band key sharing
Manually configure static encryption and authentication keys on the initiator and responder devices. The consistency of keys on both ends can be ensured through out-of-band key sharing (through telephone calls or emails). The method does not provide much scalability. The workload increases by multiple times in site-to-multisite networking. Besides, to enhance network security, the key requires periodic changes, which is difficult to implement in this method.
Key delivery using a secure connection
IPsec implements secure key negotiation between the initiator and responder devices using the IKE protocol. IKE uses the DH algorithm to exchange key information on insecure networks and generates encryption and authentication keys. This method provides simple configuration and high scalability, which becomes more remarkable on large-scale dynamic networks.
IKE provides services such as key exchange and the establishment of SAs through automatic negotiation. The IKE protocol makes the configuration and management of IPsec more simple and flexible.
Internet Security Association and Key Management Protocol (ISAKMP) is the foundation of IKE. IKE uses ISAKMP to define the procedure for key exchange. ISAKMP provides methods for security service negotiation, information exchange during key exchange, and authentication of peers.
The essence of IKE is that it never transmits the key directly on insecure networks, but calculates the key by exchanging a series of data. Even if a third party intercept all the exchanged data used for key calculation, it cannot figure out the real key. The core technology is Diffie Hellman (DH) switching technology.
DH Key Exchange
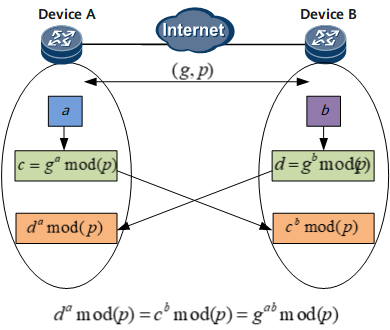
DH, also called the public key exchange method, is used to generate key materials. It uses ISAKMP messages to perform key material exchange between the initiator and responder devices. Then, the devices at both ends calculate the same symmetric key. The symmetric key is used for the calculation of encryption and authentication keys. The two devices do not exchange the real key in any cases.
Each party for exchanging the DH keys generates a random number, for example, a or b.
Based on base number g and mode number p, power arithmetic and modular arithmetic are performed using random numbers a and b to obtain results c and d. The calculation formula is as follows:
c = gamod(p)
d = gbmod(p)
Calculation results c and d are exchanged.
Both parties perform further calculation to obtain a public DH value: damod(p)=cbmod(p)=gabmod(p). This formula can be proved mathematically. The public DH value is the key for both parties.
The DH key exchange process is implemented by exchanging two packets:
- First packet: The sender randomly generates parameters g, p, and a based on the negotiated DH group, calculates c, and sends g, p, and c to the receiver.
- Second packet: After receiving the packet, the receiver randomly generates parameter b, calculates d based on parameter b and the received parameters g and p, and sends the second packet carrying d to the sender.
If a third party on the network intercepts c and d, the third party needs to obtain a and b to calculate the public DH value (gabmod(p)). However, a and b are not transmitted directly on the network. If the third party intends to calculate a or b using c and d, discrete logarithm operation is required. However, p is a prime number. When p is large enough (generally, a binary number with more than 768 bits), the calculation is extremely complex, proved mathematically. It is considered that it is impossible to calculate a or b in this method. Therefore, the DH key exchange technology ensures that both parties securely obtain key information.
The DH defines the length of a generated key using the key group. The longer the key length, the more secure the key. However, the calculation time prolongs with the key length increase.
Key Group |
Length |
|---|---|
1 |
768 bits |
2 |
1024 bits |
5 |
1536 bits |
14 |
2048 bits |
15 |
3072 bits |
16 |
4096 bits |
19 |
256 bits elliptic curve group |
20 |
384 bits elliptic curve group |
21 |
512 bits elliptic curve group |