Example for Configuring H-VPN
Networking Requirements
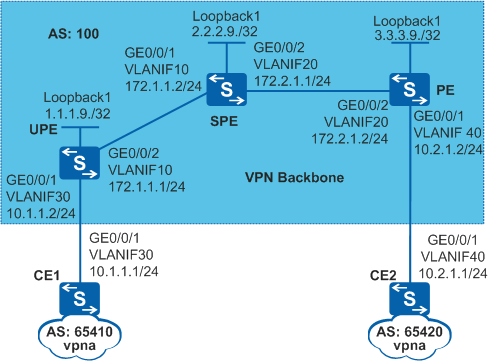
As shown in Figure 1, CE1 and CE2 belong to the same VPN, and CE1 and CE2 are connected to the UPE and NPE, respectively. OSPF is configured on the UPE, SPE, and NPE to implement interworking. Most networks use the traditional hierarchical architecture that consists of the core, aggregation, and access layers. Devices at each layer have different performance requirements. To meet such requirements, deploy HVPN. To enable the SPE to send specific routes to the UPE and implement refined control over routes, deploy the H-VPN solution of HVPN.
Configuration Roadmap
HVPN enables multiple PEs to play different roles and form a hierarchical architecture. The H-VPN solution of HVPN allows an SPE to send specific routes to a UPE. The UPE selects a route based on a destination address to implement refined control over routes.
The configuration roadmap is as follows:
- Configure an IGP on the backbone network to implement IP interworking.
- Configure basic MPLS capabilities and MPLS LDP on the backbone network to establish MPLS LSPs.
- Establish MP-IBGP peer relationships between the UPE and SPE and between the NPE and SPE to exchange VPN routing information.
- On the UPE and NPE, create VPN instances and establish EBGP peer relationships with CEs to exchange VPN routing information.
- Configure a route reflector (RR) on the SPE and specify the UPE as the SPE's client so that the UPE receives specific routes reflected by the SPE.
Procedure
- Configure VLANs on interfaces and assign IP addresses to the VLANIF interfaces and loopback interfaces according to Figure 1.
# Configure UPE.
<HUAWEI> system-view [HUAWEI] sysname UPE [UPE] interface loopback 1 [UPE-LoopBack1] ip address 1.1.1.9 32 [UPE-LoopBack1] quit [UPE] vlan batch 10 30 [UPE] interface gigabitethernet 0/0/1 [UPE-GigabitEthernet0/0/1] port link-type trunk [UPE-GigabitEthernet0/0/1] port trunk allow-pass vlan 30 [UPE-GigabitEthernet0/0/1] quit [UPE] interface gigabitethernet 0/0/2 [UPE-GigabitEthernet0/0/2] port link-type trunk [UPE-GigabitEthernet0/0/2] port trunk allow-pass vlan 10 [UPE-GigabitEthernet0/0/2] quit [UPE] interface vlanif 10 [UPE-Vlanif10] ip address 172.1.1.1 255.255.255.0 [UPE-Vlanif10] quit
The configuration on SPE, NPE, CE1, and CE2 is similar to the configuration on PE1 and is not mentioned here.
- Configure OSPF on the backbone network to implement IP interworking.
# Configure the UPE.
[UPE] ospf 1 [UPE-ospf-1] area 0 [UPE-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0 [UPE-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255 [UPE-ospf-1-area-0.0.0.0] quit [UPE-ospf-1] quit
The configuration on the SPE and NPE is similar to the configuration on the UPE and is not mentioned here.
After the configuration is complete, OSPF neighbor relationships are established between the UPE and SPE, and between the SPE and NPE. Run the display ospf peer command on these devices. The command output shows that the neighbor relationships are in Full state. Run the display ip routing-table command on these devices. The command output shows that they have learned the route to the loopback interface of each other.
- Configure basic MPLS capabilities and MPLS LDP on the backbone network to establish LDP LSPs.
# Configure the UPE.
[UPE] mpls lsr-id 1.1.1.9 [UPE] mpls [UPE-mpls] quit [UPE] mpls ldp [UPE-mpls-ldp] quit [UPE] interface vlanif 10 [UPE-Vlanif10] mpls [UPE-Vlanif10] mpls ldp [UPE-Vlanif10] quit
The configuration on the SPE and NPE is similar to the configuration on the UPE and is not mentioned here.
After the configuration is complete, LDP sessions are established between the UPE and SPE, and between the SPE and NPE. Run the display mpls ldp session command on these devices. The command output shows that the Status is Operational. Run the display mpls ldp lsp command. Information about the established LDP LSPs is displayed.
- Establish MP-IBGP peer relationships between the UPE and SPE and between the NPE and SPE.
# Configure the UPE.
[UPE] bgp 100 [UPE-bgp] peer 2.2.2.9 as-number 100 [UPE-bgp] peer 2.2.2.9 connect-interface loopback 1 [UPE-bgp] ipv4-family vpnv4 [UPE-bgp-af-vpnv4] peer 2.2.2.9 enable [UPE-bgp-af-vpnv4] quit [UPE-bgp] quit
# Configure the SPE.
[SPE] bgp 100 [SPE-bgp] peer 1.1.1.9 as-number 100 [SPE-bgp] peer 1.1.1.9 connect-interface loopback 1 [SPE-bgp] peer 3.3.3.9 as-number 100 [SPE-bgp] peer 3.3.3.9 connect-interface loopback 1 [SPE-bgp] ipv4-family vpnv4 [SPE-bgp-af-vpnv4] peer 1.1.1.9 enable [SPE-bgp-af-vpnv4] peer 3.3.3.9 enable [SPE-bgp-af-vpnv4] quit [SPE-bgp] quit
# Configure the NPE.
[NPE] bgp 100 [NPE-bgp] peer 2.2.2.9 as-number 100 [NPE-bgp] peer 2.2.2.9 connect-interface loopback 1 [NPE-bgp] ipv4-family vpnv4 [NPE-bgp-af-vpnv4] peer 2.2.2.9 enable [NPE-bgp-af-vpnv4] quit [NPE-bgp] quit
- On the UPE and NPE, create VPN instances and establish EBGP peer relationships with the CEs.
# Configure the UPE.
[UPE] ip vpn-instance vpna [UPE-vpn-instance-vpna] ipv4-family [UPE-vpn-instance-vpna-af-ipv4] route-distinguisher 100:1 [UPE-vpn-instance-vpna-af-ipv4] vpn-target 1:1 [UPE-vpn-instance-vpna-af-ipv4] quit [UPE-vpn-instance-vpna] quit [UPE] interface vlanif 30 [UPE-Vlanif30] ip binding vpn-instance vpna [UPE-Vlanif30] ip address 10.1.1.2 24 [UPE-Vlanif30] quit [UPE] bgp 100 [UPE-bgp] ipv4-family vpn-instance vpna [UPE-bgp-vpna] peer 10.1.1.1 as-number 65410 [UPE-bgp-vpna] import-route direct [UPE-bgp-vpna] quit [UPE-bgp] quit
# Configure CE1.
[CE1] bgp 65410 [CE1-bgp] peer 10.1.1.2 as-number 100 [CE1-bgp] import-route direct [CE1-bgp] quit
# Configure the NPE.
[NPE] ip vpn-instance vpna [NPE-vpn-instance-vpna] ipv4-family [NPE-vpn-instance-vpna-af-ipv4] route-distinguisher 100:2 [NPE-vpn-instance-vpna-af-ipv4] vpn-target 1:1 [NPE-vpn-instance-vpna-af-ipv4] quit [NPE-vpn-instance-vpna] quit [NPE] interface vlanif 40 [NPE-Vlanif40] ip binding vpn-instance vpna [NPE-Vlanif40] ip address 10.2.1.2 24 [NPE-Vlanif40] quit [NPE] bgp 100 [NPE-bgp] ipv4-family vpn-instance vpna [NPE-bgp-vpna] peer 10.2.1.1 as-number 65420 [NPE-bgp-vpna] import-route direct [NPE-bgp-vpna] quit [NPE-bgp] quit
# Configure CE2.
[CE2] bgp 65420 [CE2-bgp] peer 10.2.1.2 as-number 100 [CE2-bgp] import-route direct [CE2-bgp] quit
After the configuration is complete, run the display ip vpn-instance verbose command on the UPE and NPE to check the configuration of VPN instances. Run the ping -vpn-instance command on the UPE and NPE to ping the connected CEs. The ping operations succeed.

If a PE has multiple interfaces bound to the same VPN instance, specify a source IP addresses by setting -a source-ip-address in the ping -vpn-instance vpn-instance-name -a source-ip-address dest-ip-address command to ping a remote CE. If the source IP address is not specified, the ping operation fails.
- Configure the SPE as an RR.
# Configure an RR.
[SPE] bgp 100 [SPE-bgp] ipv4-family vpnv4 [SPE-bgp-af-vpnv4] undo policy vpn-target [SPE-bgp-af-vpnv4] peer 1.1.1.9 reflect-client [SPE-bgp-af-vpnv4] peer 1.1.1.9 next-hop-local [SPE-bgp-af-vpnv4] quit [SPE-bgp] quit
- Verify the configurations.
After the configuration is complete, CE1 and CE2 can receive each other's specific route and can ping each other.
[CE1] display ip routing-table Route Flags: R - relay, D - download to fib, T - to vpn-instance ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 5 Routes : 5 Destination/Mask Proto Pre Cost Flags NextHop Interface 10.1.1.0/24 Direct 0 0 D 10.1.1.1 Vlanif30 10.1.1.1/32 Direct 0 0 D 127.0.0.1 Vlanif30 10.2.1.0/24 EBGP 255 0 D 10.1.1.2 Vlanif30 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0[CE1] ping 10.2.1.1 PING 10.2.1.1: 56 data bytes, press CTRL_C to break Reply from 10.2.1.1: bytes=56 Sequence=1 ttl=251 time=1 ms Reply from 10.2.1.1: bytes=56 Sequence=2 ttl=251 time=1 ms Reply from 10.2.1.1: bytes=56 Sequence=3 ttl=251 time=1 ms Reply from 10.2.1.1: bytes=56 Sequence=4 ttl=251 time=1 ms Reply from 10.2.1.1: bytes=56 Sequence=5 ttl=251 time=1 ms --- 10.2.1.1 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 1/1/1 ms[CE2] display ip routing-table Route Flags: R - relay, D - download to fib, T - to vpn-instance ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 5 Routes : 5 Destination/Mask Proto Pre Cost Flags NextHop Interface 10.1.1.0/24 EBGP 255 0 D 10.2.1.2 Vlanif40 10.2.1.0/24 Direct 0 0 D 10.2.1.1 Vlanif40 10.2.1.1/32 Direct 0 0 D 127.0.0.1 Vlanif40 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0Run the display bgp vpnv4 all routing-table command on the UPE. The command output shows that the UPE has received specific routes from the SPE.
[UPE] display bgp vpnv4 all routing-table BGP Local router ID is 172.1.1.1 Status codes: * - valid, > - best, d - damped, h - history, i - internal, s - suppressed, S - Stale Origin : i - IGP, e - EGP, ? - incomplete Total number of routes from all PE: 4 Route Distinguisher: 100:1 Network NextHop MED LocPrf PrefVal Path/Ogn *> 10.1.1.0/24 0.0.0.0 0 0 ? * 10.1.1.1 0 0 65410? *> 10.1.1.2/32 0.0.0.0 0 0 ? Route Distinguisher: 100:2 Network NextHop MED LocPrf PrefVal Path/Ogn *>i 10.2.1.0/24 2.2.2.9 0 100 0 ? VPN-Instance vpna, Router ID 172.1.1.1: Total Number of Routes: 4 Network NextHop MED LocPrf PrefVal Path/Ogn *> 10.1.1.0/24 0.0.0.0 0 0 ? 10.1.1.1 0 0 65410? *> 10.1.1.2/32 0.0.0.0 0 0 ? *>i 10.2.1.0/24 2.2.2.9 0 100 0 ?
Configuration Files
CE1 configuration file
# sysname CE1 # vlan batch 30 # interface Vlanif30 ip address 10.1.1.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 30 # bgp 65410 peer 10.1.1.2 as-number 100 # ipv4-family unicast undo synchronization import-route direct peer 10.1.1.2 enable # return
UPE configuration file
# sysname UPE # vlan batch 10 30 # ip vpn-instance vpna ipv4-family route-distinguisher 100:1 vpn-target 1:1 export-extcommunity vpn-target 1:1 import-extcommunity # mpls lsr-id 1.1.1.9 mpls # mpls ldp # interface Vlanif10 ip address 172.1.1.1 255.255.255.0 mpls mpls ldp # interface Vlanif30 ip binding vpn-instance vpna ip address 10.1.1.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 30 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 10 # interface LoopBack1 ip address 1.1.1.9 255.255.255.255 # bgp 100 peer 2.2.2.9 as-number 100 peer 2.2.2.9 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 2.2.2.9 enable # ipv4-family vpnv4 policy vpn-target peer 2.2.2.9 enable # ipv4-family vpn-instance vpna import-route direct peer 10.1.1.1 as-number 65410 # ospf 1 area 0.0.0.0 network 1.1.1.9 0.0.0.0 network 172.1.1.0 0.0.0.255 # return
SPE configuration file
# sysname SPE # vlan batch 10 20 # mpls lsr-id 2.2.2.9 mpls # mpls ldp # interface Vlanif10 ip address 172.1.1.2 255.255.255.0 mpls mpls ldp # interface Vlanif20 ip address 172.2.1.1 255.255.255.0 mpls mpls ldp # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 20 # interface LoopBack1 ip address 2.2.2.9 255.255.255.255 # bgp 100 peer 1.1.1.9 as-number 100 peer 1.1.1.9 connect-interface LoopBack1 peer 3.3.3.9 as-number 100 peer 3.3.3.9 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 1.1.1.9 enable peer 3.3.3.9 enable # ipv4-family vpnv4 undo policy vpn-target peer 1.1.1.9 enable peer 1.1.1.9 reflect-client peer 1.1.1.9 next-hop-local peer 3.3.3.9 enable # ospf 1 area 0.0.0.0 network 2.2.2.9 0.0.0.0 network 172.1.1.0 0.0.0.255 network 172.2.1.0 0.0.0.255 # return
NPE configuration file
# sysname NPE # vlan batch 20 40 # ip vpn-instance vpna ipv4-family route-distinguisher 100:2 vpn-target 1:1 export-extcommunity vpn-target 1:1 import-extcommunity # mpls lsr-id 3.3.3.9 mpls # mpls ldp # interface Vlanif20 ip address 172.2.1.2 255.255.255.0 mpls mpls ldp # interface Vlanif40 ip binding vpn-instance vpna ip address 10.2.1.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 40 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 20 # interface LoopBack1 ip address 3.3.3.9 255.255.255.255 # bgp 100 peer 2.2.2.9 as-number 100 peer 2.2.2.9 connect-interface LoopBack1 # ipv4-family unicast undo synchronization peer 2.2.2.9 enable # ipv4-family vpnv4 policy vpn-target peer 2.2.2.9 enable # ipv4-family vpn-instance vpna import-route direct peer 10.2.1.1 as-number 65420 # ospf 1 area 0.0.0.0 network 3.3.3.9 0.0.0.0 network 172.2.1.0 0.0.0.255 # return
CE2 configuration file
# sysname CE2 # vlan batch 40 # interface Vlanif40 ip address 10.2.1.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 40 # bgp 65420 peer 10.2.1.2 as-number 100 # ipv4-family unicast undo synchronization import-route direct peer 10.2.1.2 enable # return