Example for Configuring LDP Authentication
Networking Requirements
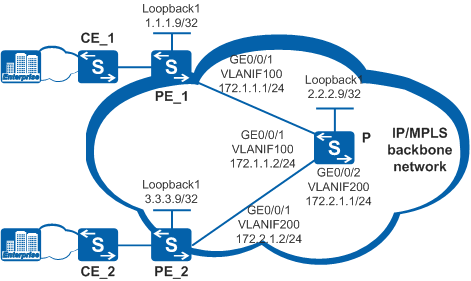
On the network shown in Figure 1, LDP sessions between PE_1 and the P and between PE_2 and the P are established. LDP LSPs are to be established over the LDP sessions. As the user network connected to PE_1 and PE_2 transmits important services, the LDP sessions between PE_1 and the P and between PE_2 and the P have high security requirements.
Configuration Roadmap
To meet the security requirements of LDP sessions, configure LDP Keychain authentication between PE_1 and the P and between PE_2 and the P. The configuration roadmap is as follows:
- Configure OSPF between the PEs and P to implement IP connectivity on the backbone network.
- Configure local LDP sessions on PEs and P so that LDP LSPs can be set up to transmit network services.
- Configure LDP Keychain authentication between PE_1 and the P and between PE_2 and the P to meet high security requirements.
Procedure
- Create VLANs and VLANIF interfaces on the switch, configure IP addresses
for the VLANIF interfaces, and add physical interfaces to the VLANs.
# Configure PE_1. The configurations of P, and PE_2 are similar to the configuration of PE_1, and are not mentioned here.
<HUAWEI> system-view [HUAWEI] sysname PE_1 [PE_1] interface loopback 1 [PE_1-LoopBack1] ip address 1.1.1.9 32 [PE_1-LoopBack1] quit [PE_1] vlan batch 100 [PE_1] interface vlanif 100 [PE_1-Vlanif100] ip address 172.1.1.1 24 [PE_1-Vlanif100] quit [PE_1] interface gigabitethernet 0/0/1 [PE_1-GigabitEthernet0/0/1] port link-type trunk [PE_1-GigabitEthernet0/0/1] port trunk allow-pass vlan 100 [PE_1-GigabitEthernet0/0/1] quit
- Configure OSPF to advertise the network segments connecting
to interfaces on each node and to advertise the routes of hosts with
LSR IDs.
# Configure PE_1. The configurations of P, and PE_2 are similar to the configuration of PE_1, and are not mentioned here.
[PE_1] ospf 1 [PE_1-ospf-1] area 0 [PE_1-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0 [PE_1-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255 [PE_1-ospf-1-area-0.0.0.0] quit [PE_1-ospf-1] quit
After the configuration is complete, run the display ip routing-table command on each node, and you can view that the nodes learn routes from each other.
- Configure local LDP sessions.
# Configure PE_1. The configurations of P, and PE_2 are similar to the configuration of PE_1, and are not mentioned here.
[PE_1] mpls lsr-id 1.1.1.9 [PE_1] mpls [PE_1-mpls] quit [PE_1] mpls ldp [PE_1-mpls-ldp] quit [PE_1] interface vlanif 100 [PE_1-Vlanif100] mpls [PE_1-Vlanif100] mpls ldp [PE_1-Vlanif100] quit
- Configure Keychain.
# Configure PE_1.
[PE_1] keychain kforldp1 mode periodic weekly [PE_1-keychain-kforldp1] tcp-kind 180 [PE_1-keychain-kforldp1] tcp-algorithm-id sha-256 8 [PE_1-keychain-kforldp1] receive-tolerance 15 [PE_1-keychain-kforldp1] key-id 1 [PE_1-keychain-kforldp1-keyid-1] algorithm sha-256 [PE_1-keychain-kforldp1-keyid-1] key-string cipher huaweiwork [PE_1-keychain-kforldp1-keyid-1] send-time day mon to thu [PE_1-keychain-kforldp1-keyid-1] receive-time day mon to thu [PE_1-keychain-kforldp1-keyid-1] quit [PE_1-keychain-kforldp1] key-id 2 [PE_1-keychain-kforldp1-keyid-2] algorithm sha-256 [PE_1-keychain-kforldp1-keyid-2] key-string cipher testpass [PE_1-keychain-kforldp1-keyid-2] send-time day fri to sun [PE_1-keychain-kforldp1-keyid-2] receive-time day fri to sun [PE_1-keychain-kforldp1-keyid-2] quit [PE_1-keychain-kforldp1] quit
# Configure the P.
[P] keychain kforldp1 mode periodic weekly [P-keychain-kforldp1] tcp-kind 180 [P-keychain-kforldp1] tcp-algorithm-id sha-256 8 [P-keychain-kforldp1] receive-tolerance 15 [P-keychain-kforldp1] key-id 1 [P-keychain-kforldp1-keyid-1] algorithm sha-256 [P-keychain-kforldp1-keyid-1] key-string cipher huaweiwork [P-keychain-kforldp1-keyid-1] send-time day mon to thu [P-keychain-kforldp1-keyid-1] receive-time day mon to thu [P-keychain-kforldp1-keyid-1] quit [P-keychain-kforldp1] key-id 2 [P-keychain-kforldp1-keyid-2] algorithm sha-256 [P-keychain-kforldp1-keyid-2] key-string cipher testpass [P-keychain-kforldp1-keyid-2] send-time day fri to sun [P-keychain-kforldp1-keyid-2] receive-time day fri to sun [P-keychain-kforldp1-keyid-2] quit [P-keychain-kforldp1] quit
- Configure LDP Keychain authentication.
# Configure PE_1.
[PE_1] mpls ldp [PE_1-mpls-ldp] authentication key-chain peer 2.2.2.9 name kforldp1 [PE_1-mpls-ldp] quit
# Configure the P.
[P] mpls ldp [P-mpls-ldp] authentication key-chain peer 1.1.1.9 name kforldp1 [P-mpls-ldp] quit
- Configure Keychain.
# Configure PE_2.
[PE_2] keychain kforldp2 mode periodic weekly [PE_2-keychain-kforldp2] tcp-kind 180 [PE_2-keychain-kforldp2] tcp-algorithm-id sha-256 8 [PE_2-keychain-kforldp2] receive-tolerance 15 [PE_2-keychain-kforldp2] key-id 1 [PE_2-keychain-kforldp2-keyid-1] algorithm sha-256 [PE_2-keychain-kforldp2-keyid-1] key-string cipher huaweiwork [PE_2-keychain-kforldp2-keyid-1] send-time day mon to thu [PE_2-keychain-kforldp2-keyid-1] receive-time day mon to thu [PE_2-keychain-kforldp2-keyid-1] quit [PE_2-keychain-kforldp2] key-id 2 [PE_2-keychain-kforldp2-keyid-2] algorithm sha-256 [PE_2-keychain-kforldp2-keyid-2] key-string cipher testpass [PE_2-keychain-kforldp2-keyid-2] send-time day fri to sun [PE_2-keychain-kforldp2-keyid-2] receive-time day fri to sun [PE_2-keychain-kforldp2-keyid-2] quit [PE_2-keychain-kforldp2] quit
# Configure the P.
[P] keychain kforldp2 mode periodic weekly [P-keychain-kforldp2] tcp-kind 180 [P-keychain-kforldp2] tcp-algorithm-id sha-256 8 [P-keychain-kforldp2] receive-tolerance 15 [P-keychain-kforldp2] key-id 1 [P-keychain-kforldp2-keyid-1] algorithm sha-256 [P-keychain-kforldp2-keyid-1] key-string cipher huaweiwork [P-keychain-kforldp2-keyid-1] send-time day mon to thu [P-keychain-kforldp2-keyid-1] receive-time day mon to thu [P-keychain-kforldp2-keyid-1] quit [P-keychain-kforldp2] key-id 2 [P-keychain-kforldp2-keyid-2] algorithm sha-256 [P-keychain-kforldp2-keyid-2] key-string cipher testpass [P-keychain-kforldp2-keyid-2] send-time day fri to sun [P-keychain-kforldp2-keyid-2] receive-time day fri to sun [P-keychain-kforldp2-keyid-2] quit [P-keychain-kforldp2] quit
- Configure LDP Keychain authentication.
# Configure PE_2.
[PE_2] mpls ldp [PE_2-mpls-ldp] authentication key-chain peer 2.2.2.9 name kforldp2 [PE_2-mpls-ldp] quit
# Configure the P.
[P] mpls ldp [P-mpls-ldp] authentication key-chain peer 3.3.3.9 name kforldp2 [P-mpls-ldp] quit
- Verify the configuration.
# Run the display mpls ldp session verbose command on the P. You can see that LDP Keychain authentication and referenced Keychain names are configured in the LDP sessions between PE_1 and the P and between PE_2 and the P.
[P] display mpls ldp session verbose LDP Session(s) in Public Network ------------------------------------------------------------------------------ Peer LDP ID : 1.1.1.9:0 Local LDP ID : 2.2.2.9:0 TCP Connection : 2.2.2.9 -> 1.1.1.9 Session State : Operational Session Role : Active Session FT Flag : Off MD5 Flag : Off Reconnect Timer : --- Recovery Timer : --- Keychain Name : kforldp1 Authentication applied: Peer Negotiated Keepalive Hold Timer : 45 Sec Configured Keepalive Send Timer : --- Keepalive Message Sent/Rcvd : 19/19 (Message Count) Label Advertisement Mode : Downstream Unsolicited Label Resource Status(Peer/Local) : Available/Available Session Age : 0000:00:04 (DDDD:HH:MM) Session Deletion Status : No Capability: Capability-Announcement : Off mLDP P2MP Capability : Off mLDP MP2MP Capability : Off mLDP MBB Capability : Off Outbound&Inbound Policies applied : NULL Addresses received from peer: (Count: 2) 1.1.1.9 172.1.1.1 ------------------------------------------------------------------------------ Peer LDP ID : 3.3.3.9:0 Local LDP ID : 2.2.2.9:0 TCP Connection : 2.2.2.9 <- 3.3.3.9 Session State : Operational Session Role : Active Session FT Flag : Off MD5 Flag : Off Reconnect Timer : --- Recovery Timer : --- Keychain Name : kforldp2 Authentication applied: Peer Negotiated Keepalive Hold Timer : 45 Sec Configured Keepalive Send Timer : --- Keepalive Message Sent/Rcvd : 18/18 (Message Count) Label Advertisement Mode : Downstream Unsolicited Label Resource Status(Peer/Local) : Available/Available Session Age : 0000:00:04 (DDDD:HH:MM) Session Deletion Status : No Capability: Capability-Announcement : Off mLDP P2MP Capability : Off mLDP MP2MP Capability : Off mLDP MBB Capability : Off Outbound&Inbound Policies applied : NULL Addresses received from peer: (Count: 2) 3.3.3.9 172.2.1.2 ------------------------------------------------------------------------------
Configuration Files
PE_1 configuration file
# sysname PE_1 # vlan batch 100 # mpls lsr-id 1.1.1.9 mpls # mpls ldp authentication key-chain peer 2.2.2.9 name kforldp1 # keychain kforldp1 mode periodic weekly receive-tolerance 15 tcp-kind 180 key-id 1 algorithm sha-256 key-string cipher %^%#RHk(LEvyUBmkls=i(>8L9i=M!}mM4FCvcuVu&@-G%^%# send-time day mon to thu receive-time day mon to thu key-id 2 algorithm sha-256 key-string cipher %^%#="+W)uY+N$8',5Lhem%H4ZyT@h{24%Lm6A'HAnS!%^%# send-time day fri to sun receive-time day fri to sun # interface Vlanif100 ip address 172.1.1.1 255.255.255.0 mpls mpls ldp # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 100 # interface LoopBack1 ip address 1.1.1.9 255.255.255.255 # ospf 1 area 0.0.0.0 network 1.1.1.9 0.0.0.0 network 172.1.1.0 0.0.0.255 # return
P configuration file
# sysname P # vlan batch 100 200 # mpls lsr-id 2.2.2.9 mpls # mpls ldp authentication key-chain peer 1.1.1.9 name kforldp1 authentication key-chain peer 3.3.3.9 name kforldp2 # keychain kforldp1 mode periodic weekly receive-tolerance 15 tcp-kind 180 key-id 1 algorithm sha-256 key-string cipher %^%#Se}$HiYed".qRuT,/=~2X47R:*Yl,Nx5&[8_p$kP%^%# send-time day mon to thu receive-time day mon to thu key-id 2 algorithm sha-256 key-string cipher %^%#vse|>n^<W6R&=p20J7*8'7'+KTBI8Rs_eX7#'Q_<%^%# send-time day fri to sun receive-time day fri to sun # keychain kforldp2 mode periodic weekly receive-tolerance 15 tcp-kind 180 key-id 1 algorithm sha-256 key-string cipher %^%#WTl)$zT5!X#LH[~.zr9Y@8k#<h"wF)pJLv"!U~A1%^%# send-time day mon to thu receive-time day mon to thu key-id 2 algorithm sha-256 key-string cipher %^%#:N6U5oq@^+,c0P/mh,OC&P}r3_L)~N8~2IXq5$iP%^%# send-time day fri to sun receive-time day fri to sun # interface Vlanif100 ip address 172.1.1.2 255.255.255.0 mpls mpls ldp # interface Vlanif200 ip address 172.2.1.1 255.255.255.0 mpls mpls ldp # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 100 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 200 # interface LoopBack1 ip address 2.2.2.9 255.255.255.255 # ospf 1 area 0.0.0.0 network 2.2.2.9 0.0.0.0 network 172.1.1.0 0.0.0.255 network 172.2.1.0 0.0.0.255 # return
PE_2 configuration file
# sysname PE_2 # vlan batch 200 # mpls lsr-id 3.3.3.9 mpls # mpls ldp authentication key-chain peer 2.2.2.9 name kforldp2 # keychain kforldp2 mode periodic weekly receive-tolerance 15 tcp-kind 180 key-id 1 algorithm sha-256 key-string cipher %^%#]~3=Y;alm>(cdcV<;`+O1}M`0Pd!GKCb#<9S+ovC%^%# send-time day mon to thu receive-time day mon to thu key-id 2 algorithm sha-256 key-string cipher %^%#C$UBYKU7=,:(\iI_3dyH^C#5Trq~wRQc.3I$&Hj*%^%# send-time day fri to sun receive-time day fri to sun # interface Vlanif200 ip address 172.2.1.2 255.255.255.0 mpls mpls ldp # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 200 # interface LoopBack1 ip address 3.3.3.9 255.255.255.255 # ospf 1 area 0.0.0.0 network 3.3.3.9 0.0.0.0 network 172.2.1.0 0.0.0.255 # return