Example for Configuring Multicast VPN Access Through MCE Devices
Multicast VPN Overview
Multicast VPN technology allows multicast services to run on BGP/MPLS IP VPN networks. This technology encapsulates multicast packets from a private network to enable the packets to be forwarded along the multicast distribution tree (MDT) on a public network. When the packets reach the destination network, they are decapsulated and forwarded to receivers as multicast packets of the private network.
Multicast VPN is used to address the following problems occurring during the multicast service deployment on BGP/MPLS IP VPN networks:
VPN multicast packets cannot pass the reverse path forwarding (RPF) check on the public network.
In multicast forwarding, multicast routers perform RPF checks on multicast packets based on the multicast source address and inbound interface. Only multicast packets from the RPF interface are forwarded. Each router needs to know the unicast route to the multicast source. The provider (P) device on a BGP/MPLS IP VPN network does not know the VPN routes; therefore, RPF checks fail on the P device.
Overlapping multicast source addresses or group addresses on VPNs lead to inter-VPN communication.
A BGP/MPLS IP VPN network allows overlapping addresses in sites on each VPN; therefore, the multicast source addresses or group addresses of different VPNs may overlap. A PE device must correctly forward multicast packets from a VPN to only the users at the sites on the same VPN to prevent communication between different VPNs.
VPN packets are forwarded in unicast mode on the public network. When the multicast traffic volume is high, loads on the public network increase greatly.
Multicast technology ensures that each link transmits only one copy of multicast packets. Each device replicates multicast data according to the number of outbound interfaces, and the bandwidth consumed does not increase with the number of receivers. If the public network supports multicast forwarding, multicast packets are replicated only at bifurcation points on the public network. This on-demand replication mechanism reduces loads on the public network and conserves bandwidth.
All PE devices on a VPN can receive multicast packets from a multicast source on the same VPN. When the multicast traffic volume is high, loads on the PE devices increase greatly.
A VPN is composed of multiple sites, each of which connects to a different PE. Some sites may not have receivers. If VPN multicast data is forwarded only to the PE devices with receivers connected, burdens on PE devices are reduced.
Configuration Notes
If multicast VPN in multicast domain (MD) mode is used on switches, the PIM-SM SSM model cannot be used on the public network.
Multicast VPN cannot be deployed on inter-AS BGP/MPLS IPv4 VPN networks.
Multicast VPN cannot be deployed on BGP/MPLS IPv6 VPN networks.
Interfaces on the following interface cards cannot be configured as member interfaces of Eth-Trunk multicast loopback interfaces:
- V200R001 to V200R003: ES0D0G24SA00, ES0D0G24CA00, ES0D0X12SA00, ES1D2G48SBC0, and ES1D2G48TBC0 interface cards for the S7700; EH1D2G24SSA0, EH1D2S24CSA0, EH1D2X12SSA0, EH1D2G48SBC0, and EH1D2G48TBC0 interface cards for the S9700
- V200R005 to V200R009: X1E series, ES0D0G24SA00, ES0D0G24CA00, ES1D2G48SBC0, and ES1D2G48TBC0 interface cards for the S7700; X1E series, EH1D2G48SBC0, and EH1D2G48TBC0 interface cards for the S9700
Applicable products and versions lists applicable products and versions.

For details about software mappings, visit Hardware Query Tool and search for the desired product model.
Networking Requirements
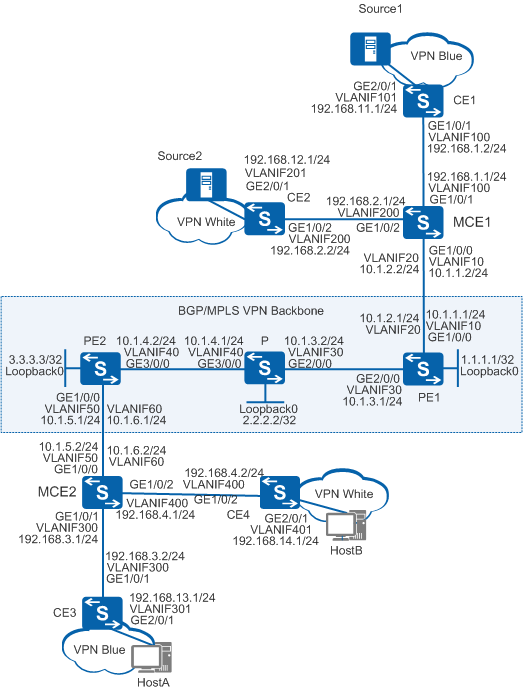
As shown in Figure 1, a company deploys two services, data of which is transmitted in multicast mode. The VPN site blue using service A and the VPN site white using service B both connect to the backbone network through the MCE devices. Multicast VPN in MD mode can be deployed to meet the multicast service requirements of the company. This configuration can isolate data of different services and reduces multicast traffic loads on the public network.
Configuration Roadmap
The configuration roadmap is as follows:
- Configure BGP/MPLS IP VPN to ensure connectivity of the VPN network.
- Configure multicast loopback interfaces, share-group addresses, and multicast tunnel interfaces (MTIs) for VPN instances on the PE devices to implement multicast VPN in MD mode.
- Enable multicast routing and PIM on all the devices. Configure the multicast function in the public network between the PE and P devices. Configure the multicast function in the VPN instances between PE and MCE devices, and between the MCE and CE devices.
Procedure
- Configure BGP/MPLS IP VPN.
- Configure multicast loopback interfaces, share-group addresses, and MTIs for VPN instances on the provider edge devices PE1 and PE2.
# Configure PE1.
[PE1] interface eth-trunk 10 [PE1-Eth-Trunk10] service type multicast-tunnel //Configure Eth-Trunk 10 as a multicast loopback interface. [PE1-Eth-Trunk10] trunkport gigabitethernet 3/0/5 //Bind member interface GE3/0/5 to Eth-Trunk 10. [PE1-Eth-Trunk10] quit [PE1] ip vpn-instance blue [PE1-vpn-instance-blue] multicast routing-enable //Enable multicast routing in VPN instance blue. [PE1-vpn-instance-blue] multicast-domain share-group 239.1.1.1 binding mtunnel 0 //Specify 239.1.1.1 as the Share-Group for VPN instance blue and bind it to multicast tunnel interface MTI0. [PE1-vpn-instance-blue] ipv4-family [PE1-vpn-instance-blue-af-ipv4] multicast-domain source-interface loopback 0 //Configure the MTI to use the address of Loopback0 as the default address. [PE1-vpn-instance-blue-af-ipv4] quit [PE1-vpn-instance-blue] quit [PE1] ip vpn-instance white [PE1-vpn-instance-white] multicast routing-enable //Enable multicast routing in VPN instance white. [PE1-vpn-instance-white] multicast-domain share-group 239.1.2.1 binding mtunnel 10 //Specify 239.1.2.1 as the Share-Group for VPN instance white and bind it to multicast tunnel interface MTI0. [PE1-vpn-instance-white] ipv4-family [PE1-vpn-instance-white-af-ipv4] multicast-domain source-interface loopback 0 //Configure the MTI to use the address of Loopback0 as the default address. [PE1-vpn-instance-white-af-ipv4] quit [PE1-vpn-instance-white] quit
# Configure PE2.
[PE2] interface eth-trunk 10 [PE2-Eth-Trunk10] service type multicast-tunnel //Configure Eth-Trunk 10 as a multicast loopback interface. [PE2-Eth-Trunk10] trunkport gigabitethernet 3/0/5 //Bind member interface GE3/0/5 to Eth-Trunk 10. [PE2-Eth-Trunk10] quit [PE2] ip vpn-instance blue [PE2-vpn-instance-blue] multicast routing-enable //Enable multicast routing in VPN instance blue. [PE2-vpn-instance-blue] multicast-domain share-group 239.1.1.1 binding mtunnel 0 //Specify 239.1.1.1 as the Share-Group for VPN instance blue and bind it to multicast tunnel interface MTI0. [PE2-vpn-instance-blue] ipv4-family [PE2-vpn-instance-blue-af-ipv4] multicast-domain source-interface loopback 0 //Configure the MTI to use the address of Loopback0 as the default address. [PE2-vpn-instance-blue-af-ipv4] quit [PE2-vpn-instance-blue] quit [PE2] ip vpn-instance white [PE2-vpn-instance-white] multicast routing-enable //Enable multicast routing in VPN instance white. [PE2-vpn-instance-white] multicast-domain share-group 239.1.2.1 binding mtunnel 10 //Specify 239.1.2.1 as the Share-Group for VPN instance white and bind it to multicast tunnel interface MTI0. [PE2-vpn-instance-white] ipv4-family [PE2-vpn-instance-white-af-ipv4] multicast-domain source-interface loopback 0 //Configure the MTI to use the address of Loopback0 as the default address. [PE2-vpn-instance-white-af-ipv4] quit [PE2-vpn-instance-white] quit
- Configure the multicast function on the public and private networks.
- Verify the configuration.
After the configuration is complete, receivers on the private networks can receive multicast data from the multicast source.
Configuration Files
Configuration file of provider edge PE1
# sysname PE1 # router id 1.1.1.1 # vlan batch 10 20 30 # multicast routing-enable # ip vpn-instance blue ipv4-family route-distinguisher 100:1 vpn-target 111:1 export-extcommunity vpn-target 111:1 import-extcommunity multicast routing-enable multicast-domain source-interface LoopBack0 multicast-domain share-group 239.1.1.1 binding mtunnel 0 # ip vpn-instance white ipv4-family route-distinguisher 200:1 vpn-target 222:1 export-extcommunity vpn-target 222:1 import-extcommunity multicast routing-enable multicast-domain source-interface LoopBack0 multicast-domain share-group 239.1.2.1 binding mtunnel 10 # mpls lsr-id 1.1.1.1 mpls # mpls ldp # interface Vlanif10 ip binding vpn-instance blue ip address 10.1.1.1 255.255.255.0 pim sm # interface Vlanif20 ip binding vpn-instance white ip address 10.1.2.1 255.255.255.0 pim sm # interface Vlanif30 ip address 10.1.3.1 255.255.255.0 pim sm mpls mpls ldp # interface Eth-Trunk10 service type multicast-tunnel # interface GigabitEthernet1/0/0 port link-type trunk port trunk allow-pass vlan 10 20 # interface GigabitEthernet2/0/0 port link-type trunk port trunk allow-pass vlan 30 # interface GigabitEthernet3/0/5 eth-trunk 10 # interface LoopBack0 ip address 1.1.1.1 255.255.255.255 pim sm # interface MTunnel0 ip binding vpn-instance blue # interface MTunnel10 ip binding vpn-instance white # bgp 100 peer 3.3.3.3 as-number 100 peer 3.3.3.3 connect-interface LoopBack0 # ipv4-family unicast undo synchronization peer 3.3.3.3 enable # ipv4-family vpnv4 policy vpn-target peer 3.3.3.3 enable # ipv4-family vpn-instance blue import-route ospf 2 # ipv4-family vpn-instance white import-route ospf 3 # ospf 1 area 0.0.0.0 network 1.1.1.1 0.0.0.0 network 10.1.3.0 0.0.0.255 # ospf 2 vpn-instance blue import-route bgp area 0.0.0.0 network 10.1.1.0 0.0.0.255 # ospf 3 vpn-instance white import-route bgp area 0.0.0.0 network 10.1.2.0 0.0.0.255 # pim vpn-instance blue c-bsr Vlanif10 c-rp Vlanif10 # pim vpn-instance white c-bsr Vlanif20 c-rp Vlanif20 # return
Configuration file of provider edge PE2
# sysname PE2 # router id 3.3.3.3 # vlan batch 40 50 60 # multicast routing-enable # ip vpn-instance blue ipv4-family route-distinguisher 100:1 vpn-target 111:1 export-extcommunity vpn-target 111:1 import-extcommunity multicast routing-enable multicast-domain source-interface LoopBack0 multicast-domain share-group 239.1.1.1 binding mtunnel 0 # ip vpn-instance white ipv4-family route-distinguisher 200:1 vpn-target 222:1 export-extcommunity vpn-target 222:1 import-extcommunity multicast routing-enable multicast-domain source-interface LoopBack0 multicast-domain share-group 239.1.2.1 binding mtunnel 10 # mpls lsr-id 3.3.3.3 mpls # mpls ldp # interface Vlanif40 ip address 10.1.4.2 255.255.255.0 pim sm mpls mpls ldp # interface Vlanif50 ip binding vpn-instance blue ip address 10.1.5.1 255.255.255.0 pim sm # interface Vlanif60 ip binding vpn-instance white ip address 10.1.6.1 255.255.255.0 pim sm # interface Eth-Trunk10 service type multicast-tunnel # interface GigabitEthernet1/0/0 port link-type trunk port trunk allow-pass vlan 50 60 # interface GigabitEthernet3/0/0 port link-type trunk port trunk allow-pass vlan 40 # interface GigabitEthernet3/0/5 eth-trunk 10 # interface LoopBack0 ip address 3.3.3.3 255.255.255.255 pim sm # interface MTunnel0 ip binding vpn-instance blue # interface MTunnel10 ip binding vpn-instance white # bgp 100 peer 1.1.1.1 as-number 100 peer 1.1.1.1 connect-interface LoopBack0 # ipv4-family unicast undo synchronization peer 1.1.1.1 enable # ipv4-family vpnv4 policy vpn-target peer 1.1.1.1 enable # ipv4-family vpn-instance blue import-route ospf 2 # ipv4-family vpn-instance white import-route ospf 3 # ospf 1 area 0.0.0.0 network 3.3.3.3 0.0.0.0 network 10.1.4.0 0.0.0.255 # ospf 2 vpn-instance blue import-route bgp area 0.0.0.0 network 10.1.5.0 0.0.0.255 # ospf 3 vpn-instance white import-route bgp area 0.0.0.0 network 10.1.6.0 0.0.0.255 # return
Configuration file of provider intermediate device P
# sysname P # router id 2.2.2.2 # vlan batch 30 40 # multicast routing-enable # mpls lsr-id 2.2.2.2 mpls # mpls ldp # interface Vlanif30 ip address 10.1.3.2 255.255.255.0 pim sm mpls mpls ldp # interface Vlanif40 ip address 10.1.4.1 255.255.255.0 pim sm mpls mpls ldp # interface GigabitEthernet2/0/0 port link-type trunk port trunk allow-pass vlan 30 # interface GigabitEthernet3/0/0 port link-type trunk port trunk allow-pass vlan 40 # interface LoopBack0 ip address 2.2.2.2 255.255.255.255 pim sm # ospf 1 area 0.0.0.0 network 2.2.2.2 0.0.0.0 network 10.1.3.0 0.0.0.255 network 10.1.4.0 0.0.0.255 # pim c-bsr LoopBack0 c-rp LoopBack0 # return
Configuration file of branches' aggregate egress MCE1
# sysname MCE1 # vlan batch 10 20 100 200 # multicast routing-enable # ip vpn-instance blue ipv4-family route-distinguisher 100:1 vpn-target 111:1 export-extcommunity vpn-target 111:1 import-extcommunity multicast routing-enable # ip vpn-instance white ipv4-family route-distinguisher 200:1 vpn-target 222:1 export-extcommunity vpn-target 222:1 import-extcommunity multicast routing-enable # interface Vlanif10 ip binding vpn-instance blue ip address 10.1.1.2 255.255.255.0 pim sm # interface Vlanif20 ip binding vpn-instance white ip address 10.1.2.2 255.255.255.0 pim sm # interface Vlanif100 ip binding vpn-instance blue ip address 192.168.1.1 255.255.255.0 pim sm # interface Vlanif200 ip binding vpn-instance white ip address 192.168.2.1 255.255.255.0 pim sm # interface GigabitEthernet1/0/0 port link-type trunk port trunk allow-pass vlan 10 20 # interface GigabitEthernet1/0/1 port link-type trunk port trunk allow-pass vlan 100 # interface GigabitEthernet1/0/2 port link-type trunk port trunk allow-pass vlan 200 # ospf 1 vpn-instance blue vpn-instance-capability simple area 0.0.0.0 network 10.1.1.0 0.0.0.255 network 192.168.1.0 0.0.0.255 # ospf 2 vpn-instance white vpn-instance-capability simple area 0.0.0.0 network 10.1.2.0 0.0.0.255 network 192.168.2.0 0.0.0.255 # return
Configuration file of branches' aggregate egress MCE2
# sysname MCE2 # vlan batch 50 60 300 400 # multicast routing-enable # ip vpn-instance blue ipv4-family route-distinguisher 100:1 vpn-target 111:1 export-extcommunity vpn-target 111:1 import-extcommunity multicast routing-enable # ip vpn-instance white ipv4-family route-distinguisher 200:1 vpn-target 222:1 export-extcommunity vpn-target 222:1 import-extcommunity multicast routing-enable # interface Vlanif50 ip binding vpn-instance blue ip address 10.1.5.2 255.255.255.0 pim sm # interface Vlanif60 ip binding vpn-instance white ip address 10.1.6.2 255.255.255.0 pim sm # interface Vlanif300 ip binding vpn-instance blue ip address 192.168.3.1 255.255.255.0 pim sm # interface Vlanif400 ip binding vpn-instance white ip address 192.168.4.1 255.255.255.0 pim sm # interface GigabitEthernet1/0/0 port link-type trunk port trunk allow-pass vlan 50 60 # interface GigabitEthernet1/0/1 port link-type trunk port trunk allow-pass vlan 300 # interface GigabitEthernet1/0/2 port link-type trunk port trunk allow-pass vlan 400 # ospf 1 vpn-instance blue vpn-instance-capability simple area 0.0.0.0 network 10.1.5.0 0.0.0.255 network 192.168.3.0 0.0.0.255 # ospf 2 vpn-instance white vpn-instance-capability simple area 0.0.0.0 network 10.1.6.0 0.0.0.255 network 192.168.4.0 0.0.0.255 # return
Configuration file of CE1, egress for a site of service A
# sysname CE1 # vlan batch 100 to 101 # multicast routing-enable # interface Vlanif100 ip address 192.168.1.2 255.255.255.0 pim sm # interface Vlanif101 ip address 192.168.11.1 255.255.255.0 pim sm # interface GigabitEthernet1/0/1 port link-type trunk port trunk allow-pass vlan 100 # interface GigabitEthernet2/0/1 port link-type trunk port trunk allow-pass vlan 101 # ospf 1 area 0.0.0.0 network 192.168.1.0 0.0.0.255 network 192.168.11.0 0.0.0.255 # return
Configuration file of CE2, egress for a site of service B
# sysname CE2 # vlan batch 200 to 201 # multicast routing-enable # interface Vlanif200 ip address 192.168.2.2 255.255.255.0 pim sm # interface Vlanif201 ip address 192.168.12.1 255.255.255.0 pim sm # interface GigabitEthernet1/0/2 port link-type trunk port trunk allow-pass vlan 200 # interface GigabitEthernet2/0/1 port link-type trunk port trunk allow-pass vlan 201 # ospf 1 area 0.0.0.0 network 192.168.2.0 0.0.0.255 network 192.168.12.0 0.0.0.255 # return
Configuration file of CE3, egress for a site of service A.
# sysname CE3 # vlan batch 300 to 301 # multicast routing-enable # interface Vlanif300 ip address 192.168.3.2 255.255.255.0 pim sm # interface Vlanif301 ip address 192.168.13.1 255.255.255.0 pim sm igmp enable # interface GigabitEthernet1/0/1 port link-type trunk port trunk allow-pass vlan 300 # interface GigabitEthernet2/0/1 port link-type trunk port trunk allow-pass vlan 301 # ospf 1 area 0.0.0.0 network 192.168.3.0 0.0.0.255 network 192.168.13.0 0.0.0.255 # return
Configuration file of CE4, egress for a site of service B
# sysname CE4 # vlan batch 400 to 401 # multicast routing-enable # interface Vlanif400 ip address 192.168.4.2 255.255.255.0 pim sm # interface Vlanif401 ip address 192.168.14.1 255.255.255.0 pim sm igmp enable # interface GigabitEthernet1/0/2 port link-type trunk port trunk allow-pass vlan 400 # interface GigabitEthernet2/0/1 port link-type trunk port trunk allow-pass vlan 401 # ospf 1 area 0.0.0.0 network 192.168.4.0 0.0.0.255 network 192.168.14.0 0.0.0.255 # return
Applicable products and versions
Product |
Software Version |
|---|---|
S7700 |
All versions |
S9700 |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005C00, V200R006C00, V200R007(C00&C10), V200R008C00, V200R009C00, V200R010C00, V200R011C10, V200R012C00, V200R013C00 |
S5700-HI |
Only V200R005C01 and V200R005C02 |
S5710-HI |
Only V200R005C02 |
S5720-HI |
V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
S5720-EI, S6720-EI, S6720S-EI |
V200R010C00 and later versions |
S6720-HI, S5730-HI |
V200R012C00 and later versions |
S5731-H |
V200R013C02, V200R019C00, V200R019C10 |
S5731-S, S5731S-S |
V200R019C00, V200R019C10 |
S5731S-H |
V200R019C00, V200R019C10 |
S5732-H |
V200R019C00, V200R019C10 |
S6730-H |
V200R013C02, V200R019C00, V200R019C10 |
S6730S-H |
V200R019C10 |
S6730-S, S6730S-S |
V200R019C00, V200R019C10 |