Encryption and Authentication
IPSec provides two security mechanisms: encryption and authentication. The encryption mechanism ensures data confidentiality and prevents data from being intercepted during transmission. The authentication mechanism ensures data integrity and reliability and prevents data from being forged or tampered with during transmission.
Encryption
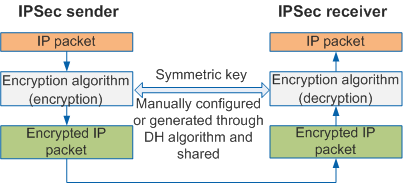
IPSec uses symmetric encryption algorithms to encrypt and decrypt data. Figure 1 shows the process of encrypting and decrypting data through the same key (that is, a symmetric key) between two IPSec peers.
A symmetric key used for encryption and decryption can be configured manually or generated automatically through IKE negotiation.
Common symmetric encryption algorithms include Data Encryption Standard (DES), Triple Data Encryption Standard (3DES), and Advanced Encryption Standard (AES). DES and 3DES are not recommended because they are insecure and pose security risks.
Authentication
IPSec uses the Keyed-Hash Message Authentication Code (HMAC) function to compare digital signatures to check integrity and authenticity of data packets.
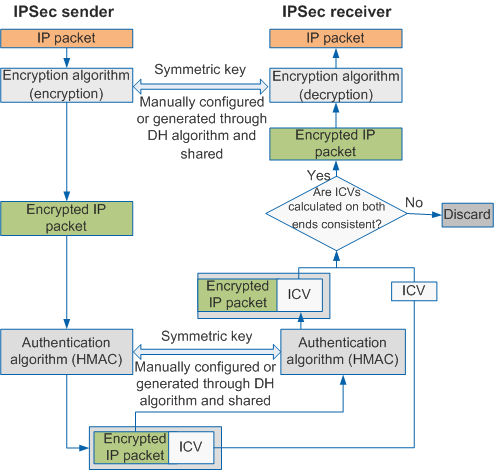
Encryption and authentication are often used together. As shown in Figure 2, the IPSec sender encrypts an IP packet, generates a digital signature through an authentication algorithm and a symmetric key, and then sends both the encrypted IP packet and digital signature to the IPSec receiver. The digital signature is included in the Integrity Check Value (ICV) field of an AH or ESP header. For details, see Security Protocols. The IPSec receiver processes the encrypted packet using the same authentication algorithm and symmetric key, and compares the received digital signature with the locally generated one to check integrity and authenticity of data in the received IP packet. The IPSec receiver discards any packets that fail the authentication and decrypts only those that pass the authentication.
Similar to a symmetric key used for encryption, a symmetric key used for authentication can be configured manually or generated automatically through IKE Protocol negotiation.
Common authentication algorithms include Message Digest 5 (MD5), Secure Hash Algorithm 1 (SHA1), and SHA2. MD5 and SHA1 are not recommended because they are insecure and pose security risks.