Key Exchange
How to securely share a symmetric key is an important issue during encryption and authentication using the key. Two methods are available to address this issue:
Out-of-band key sharing
An encryption key and an authentication key are manually configured on the IPSec sender and receiver. The two parties ensure key consistency in out-of-band mode, for example, by exchanging phone calls or emails. This mode not only has poor security and scalability, but also multiplies the workload in configuring keys in point-to-multipoint networking. In addition, this mode is difficult to implement because the keys need to be modified periodically for security purposes.
Using a secure key distribution protocol
Keys are generated through IKE negotiation. The IKE protocol uses the DH algorithm to implement secure key distribution over an insecure network. This mode is easy to configure and provides high scalability, especially on a large dynamic network. Two communicating parties exchange keying materials to calculate shared keys. Even if a third party obtains all the exchanged data used to calculate the shared keys, it cannot calculate the shared keys. Therefore, this mode greatly improves security.
IKE Protocol
IKE is a UDP-based application-layer protocol built on the Internet Security Association and Key Management Protocol (ISAKMP) framework. IPsec uses the IKE protocol for key auto-negotiation and IPSec SA establishment, simplifying IPSec configuration and maintenance.
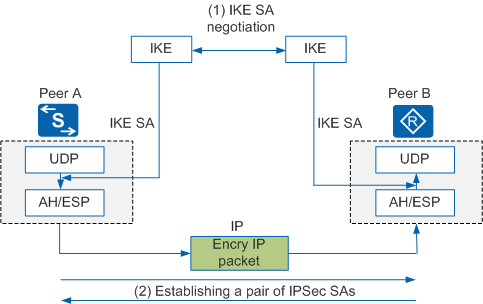
Figure 1 shows the relationship between IKE and IPSec. Two peers establish an IKE SA for identity authentication and key exchange. Protected by the IKE SA, the peers negotiate a pair of IPSec SAs using the AH or ESP protocol and other configured parameters. Subsequently, data is encrypted and transmitted between the peers in an IPSec tunnel.
An IKE SA is bidirectional, so only one IKE SA needs to be established between two peers.
IKE security mechanisms
Identity authentication
Two peers authenticate the identity (IP address or name) of each other, using pre-shared key (PSK) authentication or Rivest-Shamir-Adleman (RSA) signature authentication.

Efficient VPN supports only PKS authentication.
- PSK authentication: Two peers compute the hash value of packets using the PSK and check whether they obtain the same hash value. If the peers obtain the same hash value, the authentication succeeds. Otherwise, authentication fails. For a peer that has multiple remote IPSec peers, PSK authentication requires each pair of peers to have the same PSK. This authentication method can be easily implemented on small-scale networks but has low security.
- RSA signature authentication: Two peers use a certificate issued by a certificate authority (CA) to verify the validity of a digital certificate. Each peer has a public key (transmitted over the network) and a private key (possessed by itself). The sender computes a hash value for original packets, and then encrypts the hash value using its private key to generate a digital signature. The receiver decrypts the digital signature using the public key received from the sender, and then computes a hash value for packets. If the computed hash value is the same as that decrypted from the digital signature, the authentication succeeds. Otherwise, authentication fails. RSA signature authentication provides high security but requires digital certificates issued by a CA. This authentication method is applicable to large-scale networks.
IKE supports the following authentication algorithms: SHA2-256.
Identity protection
After a key is generated, identity data is encrypted using the key to ensure secure transmission.
IKE supports the following encryption algorithms: 3DES, AES-128, AES-192, and AES-256.
DH
DH is a public key exchange method that generates keying materials and uses ISAKMP messages to exchange keying materials between the sender and receiver. The two devices compute the same symmetric key and generate an encryption key and an authentication key based on this symmetric key. The encryption key and authentication key are never exchanged between the two devices. DH key exchange is central to IKE.
Perfect Forward Secrecy (PFS)
If PFS is enabled, an additional DH key exchange is performed when keys used in IPSec SAs are generated based on the keys used in the IKE SA. This ensures that the keys used in IPSec SAs remain indecipherable even if a key used in the IKE SA is deciphered.

To improve security, SHA2-256 authentication algorithm and AES encryption algorithm are recommended.
IKE versions
IKE has two versions: IKEv1 and IKEv2. IKEv2 has the following advantages over IKEv1:
Simplifies SA negotiation and improves negotiation efficiency.
IKEv1 goes through two phases to negotiate the key and establish IPSec SAs. In phase 1, two peers negotiate and establish a secure tunnel, which is an IKE SA. In phase 2, the peers establish a pair of IPSec SAs through the secure channel established in phase 1. IKEv2 generates the key and establishes IPSec SAs in just one negotiation, simplifying the negotiation process. For details, see Establishing SAs Through IKEv1 Negotiation and Establishing SAs Through IKEv2 Negotiation.
Fixes many cryptographic vulnerabilities, enhancing security.