Cryptography
Cryptography is the basis for secure information transmission on networks. Cryptography is to convert plaintext (to be hidden) into ciphertext (unreadable data) using mathematics.
Symmetric Key Cryptography
Symmetric key cryptography, which is also called shared key cryptography, uses the same key to encrypt and decrypt data.
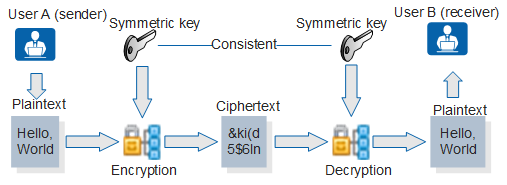
Figure 1 shows the symmetric key encryption and decryption process.
User A uses the symmetric key to encrypt data and sends the encrypted data to user B.
User B decrypts the data using the symmetric key and gets the original data.
Symmetric key cryptography features high efficiency, simple algorithm, and low cost. It is suitable for encrypting a large amount of data. However, it is difficult to implement because the two parties must exchange their keys securely before communication. Besides, it is difficult to expand because each pair of communicating parties needs to negotiate keys, and n users needs to negotiate n*(n-1)/2 different keys.
The algorithms commonly used in symmetric key cryptography include Data Encryption Standard (DES), Triple Data Encryption Standard (3DES), and Advance Encrypt Standard (AES).
Public Key Cryptography
Public key cryptography, which is also called asymmetric key cryptography, uses different keys (public and private) for data encryption and decryption. The public key is open to public, and the private key is possessed by only the owner.
Public key cryptography prevents the security risks in the distribution and management of a symmetric key. In an asymmetric key pair, the public key is used to encrypt data and the private key is used to decrypt data. The two parties do not need to exchange keys before a secure communication session. The sender uses the public key of the receiver to encrypt the data, and the receiver uses its own private key to decrypt data. The receiver's private key is only known by the receiver, so the data is secure.
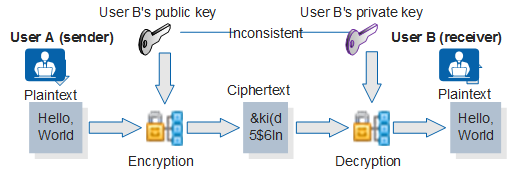
Figure 2 shows the public key encryption and decryption process.
User A uses the public key of user B to encrypt data and sends the encrypted data to user B.
User B decrypts the data using its own private key and gets the original data.
Attackers cannot use one key in a key pair to figure out the other key. The data encrypted by a public key can only be decrypted by the private key of the same user. However, the public key cryptography requires a long time to encrypt a large amount of data, and the encrypted data is too long, consuming much bandwidth.
Public key cryptography is suitable for encrypting sensitive information such as keys and identities to provide higher security.
The algorithms commonly used in public key cryptography include Diffie-Hellman (DH), Ron Rivest, Adi Shamirh, LenAdleman (RSA), and Digital Signature Algorithm (DSA).