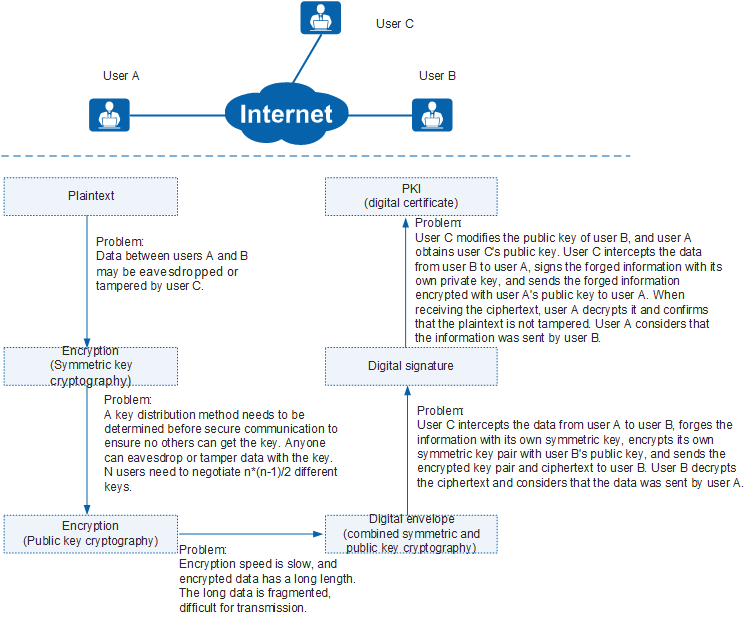
Basic Concepts of PKI
The core of PKI is digital certificate lifecycle management, including applying for, issuing, and using the digital certificates. During the lifecycle, PKI uses the symmetric key cryptographic, public key cryptographic, digital envelope, and digital signature. Figure 1 shows the evolution of these technologies. Users A and B communicate through the Internet, and user C is the attacker who targets the communication data between users A and B.
The concepts mentioned in the figure will be described in later sections.