Digital Envelope and Digital Signature
Digital Envelope
A digital envelope contains the symmetric key encrypted using the peer's public key. When receiving a digital envelope, the receiver uses its own private key to decrypt the digital envelope and obtains the symmetric key.
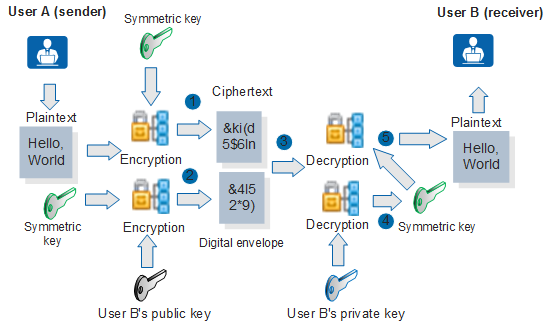
Figure 1 shows the encryption and decryption process for a digital envelope.
Assume that user A has the public key of user B. The encryption and decryption process is as follows:
- User A uses a symmetric key to encrypt data.
- User A uses the public key of user B to encrypt the symmetric key and generate a digital envelope.
- User A sends the digital envelope and encrypted data to user B.
- User B uses its own private key to decrypt the digital envelope and obtains the symmetric key.
- User B uses the symmetric key to decrypt the data and obtains the original data.
The digital envelope has the advantages of both symmetric key cryptography and public key cryptography. It speeds up key distribution and encryption and improves key security, extensibility, as well as efficiency.
However, the digital envelope still has a vulnerability. The attacker may obtain information from user A, use its own symmetric key to encrypt the forged information, use the public key of user B to encrypt its own symmetric key, and send the information to user B. After receiving the information, user B decrypts it and considers that the information is sent from user A. To address this problem, the digital signature is used to ensure that the received information was sent from the correct sender.
Digital Signature
Digital signature is generated by the sender by encrypting the digital fingerprint using its own private key. The receiver uses the sender's public key to decrypt the digital signature and obtain the digital fingerprint.
A digital fingerprint, which is also called message digest, is generated by the sender using the hash algorithm on plaintext information. The sender sends both digital fingerprint and plaintext to the receiver, and the receiver uses the same hash algorithm to calculate the digital fingerprint on the plaintext. If the two fingerprints are the same, the receiver knows that the information has not been tampered with.
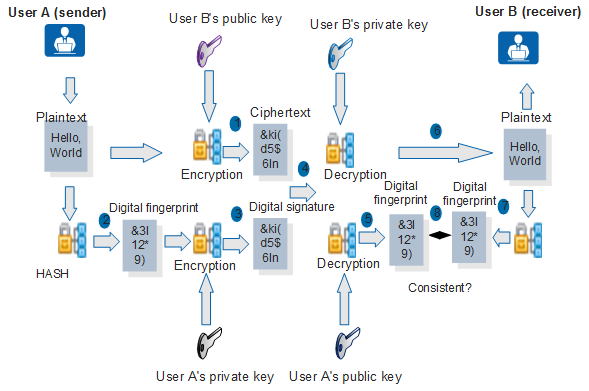
Figure 2 shows the encryption and decryption process for a digital signature.
Assume that user A has the public key of user B. The encryption and decryption process is as follows:
- User A uses the public key of user B to encrypt data.
- User A performs hash on the plaintext and generates a digital fingerprint.
- User A uses its own private key to encrypt the digital fingerprint, generating the digital signature.
- User A sends both the ciphertext and digital signature to user B.
- User B uses the public key of user A to decrypt the digital signature, obtaining the digital fingerprint.
- After receiving the ciphertext from user A, user B uses its own private key to decrypt the information, obtaining the plaintext information.
- User B performs hash on the plaintext and generates a digital fingerprint.
- User B compares the generated fingerprint with the received one. If the two fingerprints are the same, user B accepts the plaintext; otherwise, user B discards it.
The digital signature proves that information is not tampered with and verifies the sender's identity. The digital signature and digital envelope can be used together.
However, the digital signature still has a vulnerability. If the attacker modifies the public key of user B, then user A obtains the attacker's public key. The attacker can obtain information from user B to user A, sign the forged information using its own private key, and send the forged information encrypted using user A's public key to user A. After receiving the encrypted information, user A decrypts the information and verifies that the information has not been tampered with. In addition, user A considers that the information was sent by user B. The digital certificate can fix this vulnerability. It ensures that one public key is possessed by only one owner.