Example for Configuring a Device to Communicate with the NMS Using SNMPv3
SNMP Overview
The Simple Network Management Protocol (SNMP) is a standard network management protocol widely used on TCP/IP networks. SNMP manages network elements by using a central computer (a network management station) running network management software.
SNMP has the following advantages:
- Automatic configuration management:
A network administrator can use SNMP to quickly query information, modify data, locate faults, and so forth on any SNMP agent. SNMP greatly improves work efficiency of network administrators.
- Multi-vendor management:
SNMP shields the physical differences between devices of different vendors. SNMP provides only a basic function set, so the managed tasks are separated from the managed physical features and lower-layer interoperation technologies. Therefore, SNMP can uniformly manage devices of multiple vendors simultaneously.
SNMP is available in three versions. SNMPv1 is the initial version of SNMP. It provides authentication based on community names. SNMPv1 has low security, and can return only a few error codes. SNMPv2c issued by IETF is the second release of SNMP. SNMPv2c has enhancements to standard error codes, data types (Counter 64 and Counter 32), and operations including GetBulk and Inform. SNMPv2c does not improve the security, so IETF issued SNMPv3 that provides encryption and authentication based on the user-based security model (USM) and access control based on the view-based access control model (VACM).
SNMPv3 is applicable to networks of various scales, especially networks that have strict security requirements and can be managed only by authorized network administrators. For example, SNMPv3 can be used if data between the NMS and managed device needs to be transmitted over a public network.
Configuration Notes
This configuration example applies to all switches running all versions.
In this example, eSight running V300R007C00 is used as the NMS.
Networking Requirements
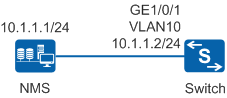
As shown in Figure 1, the NMS server manages all devices on the network. The network is large and is prone to attack. Therefore, devices on the network use SNMPv3 to communicate with the NMS server. A new switch is added to the network. The network administrator wants to use the existing network resources to manage the new switch and quickly locate and rectify network faults.
Configuration Roadmap
The configuration roadmap is as follows:
Configure SNMPv3 on the switch so that the NMS running SNMPv3 can manage the switch.
Configure access control so that only the NMS with the specified IP address can perform read/write operations on the specified MIB objects of the switch.
Configure a user group and user based on which the switch permits access of the NMS.
Configure a trap host and enable the switch to automatically send traps to the NMS.
Add the switch to the NMS. The user group and user configured on the switch must be the same as those used by the NMS; otherwise, the NMS cannot manage the switch.
Procedure
- Configure SNMPv3 on the switch so that the NMS running SNMPv3 can manage the switch.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] snmp-agent sys-info version v3 //By default, SNMPv3 is supported. If SNMPv3 is not disabled, skip this command.
- Configure access control so that only the NMS with the specified IP address can perform read/write operations on the specified MIB objects of the switch.
# Configure an ACL to permit only the NMS 10.1.1.1 to access the switch.
[Switch] acl 2001 [Switch-acl-basic-2001] rule permit source 10.1.1.1 0 [Switch-acl-basic-2001] rule deny [Switch-acl-basic-2001] quit
# Configure the MIB view to specify the MIB objects that can be accessed by the NMS.
[Switch] snmp-agent mib-view included isoview iso //Configure the MIB view isoview to access the iso subtree. - Configure a user group and user based on which the switch permits access of the NMS.
# Configure the user group group001, set the security level to privacy, and configure access control to restrict the access of NMS to the switch.
[Switch] snmp-agent group v3 group001 privacy read-view isoview write-view isoview notify-view isoview acl 2001# Configure an SNMPv3 user named user001 and add the user to group001.
[Switch] snmp-agent usm-user v3 user001 group group001# Set the user authentication algorithm to sha (indicating HMAC-SHA-96), authentication password to Authe@1234.
[Switch] snmp-agent usm-user v3 user001 authentication-mode sha Please configure the authentication password (8-64) Enter Password: //Enter the authentication password. Confirm Password: //Confirm the password.

In versions earlier than V200R003C00, the user name is configured using snmp-agent usm-user v3 user001 group001 authentication-mode sha Authe@1234 privacy-mode des56 Priva@1234.
In V200R019C00, the system software does not support the sha parameter. To use the sha parameter, you need to install the V200R019SPH007 patch or the SHA1 plug-in. For higher security purposes, you are advised to specify the sha2-256 parameter, which indicates the more secure HMAC-SHA2-256-192 algorithm.
# Set the user encryption algorithm to aes256 (indicating AES-256), and encryption password to Priva@1234.
[Switch] snmp-agent usm-user v3 user001 privacy-mode aes128 Please configure the privacy password (8-64) Enter Password: //Enter the encryption password. Confirm Password: //Confirm the password.
- Configure a trap host and enable the switch to automatically send traps to the NMS.
[Switch] snmp-agent trap enable Warning: All switches of SNMP trap/notification will be open. Continue? [Y/N]:y //Enable all trap functions on the switch. By default, only some trap functions are enabled. You can run the display snmp-agent trap all command to check trap status. [Switch] snmp-agent target-host trap address udp-domain 10.1.1.1 params securityname user001 v3 privacy //Configure a trap host. By default, traps are sent by UDP port 162. The security name must be the same as the user name; otherwise, the NMS cannot manage the device.
- Add the switch to the NMS.
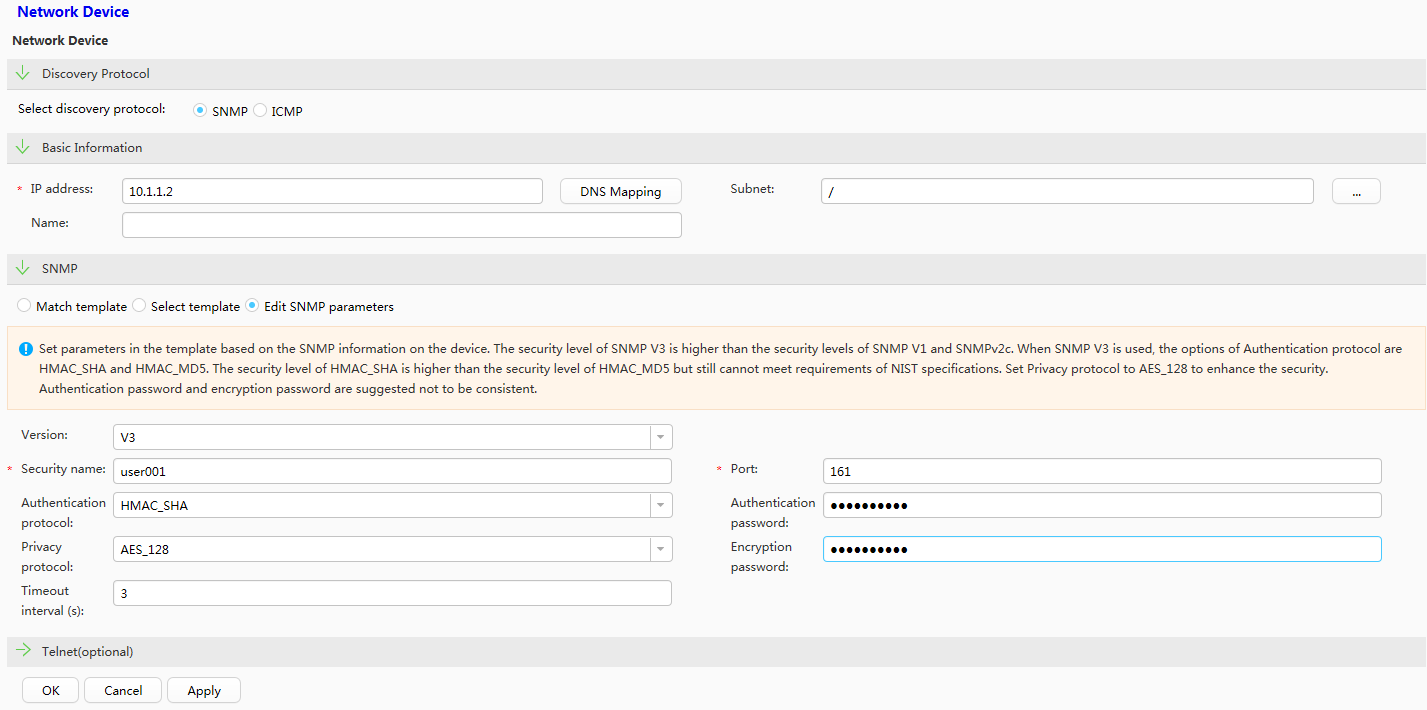
# Log in to eSight and choose . Set SNMP parameters based on Table 1 and click OK. A switch is added to and can be managed by eSight. The switch will proactively send trap messages to eSight.
Table 1 SNMP parameters Parameter
Setting
Select discovery protocol
SNMP
IP address
10.1.1.2
SNMP
Edit SNMP parameters
Version
V3
Security name
user001
Port
161
Authentication protocol
HMAC_SHA
Authentication password
Authe@1234
Privacy protocol
AES_128
Encryption password
Priva@1234

The parameter settings on the NMS and switch must be the same; otherwise, the switch cannot be added to the NMS.
If authentication is required for remote logins to the switch, Telnet parameters need to be set so that the NMS can manage the switch. In this example, administrators can remotely log in to the switch using Telnet, password authentication is used, and the password is huawei2012.
Configuration Files
Configuration file of the switch
# sysname Switch # acl number 2001 rule 5 permit source 10.1.1.1 0 rule 10 deny # snmp-agent snmp-agent local-engineid 800007DB03360102101100 snmp-agent sys-info version v3 snmp-agent group v3 group001 privacy read-view isoview write-view isoview notify-view isoview acl 2001 snmp-agent target-host trap address udp-domain 10.1.1.1 params securityname user001 v3 privacy snmp-agent mib-view included isoview iso snmp-agent usm-user v3 user001 snmp-agent usm-user v3 user001 group group001 snmp-agent usm-user v3 user001 authentication-mode sha cipher %^%#*2C%=4LZn1L>ni9xaybHdbXFW&[c_Wv0m!0MpTj!%^%# snmp-agent usm-user v3 user001 privacy-mode aes128 cipher %^%#i\Fv-cC(u)+x26S2'rEX<.;V+e~nP)*.J$Ulr($/%^%# snmp-agent trap enable # return