Example for Configuring Static Routes for Link Backup
Static Route Overview
Static routes use less bandwidth than dynamic routes and do not use CPU resources for route calculation and update analysis. They are manually configured by administrators. If a network fault occurs or the topology changes, static routes must be manually reconfigured as they cannot be automatically updated. Static routes have five parameters: destination IP address, mask, outbound interface, next hop, and priority.
Static routes are generally suitable for simple networks. However, they can be used on complex networks to improve network performance and ensure bandwidth for important applications.
Configuration Notes
- Communication between two devices is bidirectional, so reachable routes must be available in both directions. To enable two devices to communicate through static routes, configure a static route on the local device and then configure a return route on the peer device.
- If an enterprise network has two egresses, two equal-cost static routes can be configured for load balancing. In this case, two non-equal-cost static routes can be configured for active/standby backup. When the active link is faulty, traffic is switched from the active link to the standby link.
- This example applies to all versions of all S series switches.
Networking Requirements
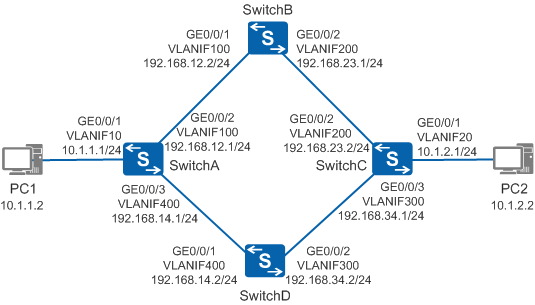
On the network shown in Figure 1, PC1 and PC2 are connected through four switches. Data traffic of PC1 can reach PC2 through two links: PC1->SwitchA->SwitchB->SwitchC->PC2 and PC1->SwitchA->SwitchD->SwitchC->PC2. To improve reliability, users want to implement backup between the two links. That is, traffic from PC1 to PC2 is first transmitted through the link that passes through SwitchB. When faults occur on this link, traffic is automatically switched to the link that passes through SwitchD.

In this scenario, ensure that all connected interfaces have STP disabled. If STP is enabled and VLANIF interfaces of switches are used to construct a Layer 3 ring network, an interface on the network will be blocked. As a result, Layer 3 services on the network cannot run normally.
Configuration Roadmap
The configuration roadmap is as follows:
- Create VLANs, add interfaces to the VLANs, and assign IP addresses to VLANIF interfaces.
- Configure static routes in two directions of data traffic.
- Configure IP address and default gateways for hosts.
Procedure
- Specify the VLANs to which interfaces belong.
# Configure SwitchA. The configurations of SwitchB, SwitchC, and SwitchD are similar.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 10 100 400 [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type access [SwitchA-GigabitEthernet0/0/1] port default vlan 10 [SwitchA-GigabitEthernet0/0/1] quit [SwitchA] interface gigabitethernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] port link-type trunk [SwitchA-GigabitEthernet0/0/2] port trunk allow-pass vlan 100 [SwitchA-GigabitEthernet0/0/2] quit [SwitchA] interface gigabitethernet 0/0/3 [SwitchA-GigabitEthernet0/0/3] port link-type trunk [SwitchA-GigabitEthernet0/0/3] port trunk allow-pass vlan 400 [SwitchA-GigabitEthernet0/0/3] quit
- Configure an IP address for each VLANIF interface.
# Configure SwitchA. The configurations of SwitchB, SwitchC, and SwitchD are similar.
[SwitchA] interface vlanif 10 [SwitchA-Vlanif10] ip address 10.1.1.1 24 [SwitchA-Vlanif10] quit [SwitchA] interface vlanif 100 [SwitchA-Vlanif100] ip address 192.168.12.1 24 [SwitchA-Vlanif100] quit [SwitchA] interface vlanif 400 [SwitchA-Vlanif400] ip address 192.168.14.1 24 [SwitchA-Vlanif400] quit
- Configure static routes from PC1 to PC2.
# On SwitchA, configure two static routes with different priorities. The next hop of one route points to SwitchB, and that of the other route points to SwitchD. Subsequently, data traffic is first forwarded to SwitchB. When faults occur on the link that passes through SwitchB, the traffic is automatically switched to SwitchD.
[SwitchA] ip route-static 10.1.2.0 24 192.168.12.2 [SwitchA] ip route-static 10.1.2.0 24 192.168.14.2 preference 70
# Configure SwitchB.
[SwitchB] ip route-static 10.1.2.0 24 192.168.23.2# Configure SwitchD.
[SwitchD] ip route-static 10.1.2.0 24 192.168.34.1 - Configure static routes from PC2 to PC1 and ensure that
the active and standby links in two directions are the same.
# On SwitchC, configure two static routes with different priorities. The next hop of one route points to SwitchB, and that of the other route points to SwitchD. Subsequently, data traffic is first forwarded to SwitchB. When faults occur on the link that passes through SwitchB, traffic is automatically switched to SwitchD.
[SwitchC] ip route-static 10.1.1.0 24 192.168.23.1 [SwitchC] ip route-static 10.1.1.0 24 192.168.34.2 preference 70
# Configure SwitchB.
[SwitchB] ip route-static 10.1.1.0 24 192.168.12.1# Configure SwitchD.
[SwitchD] ip route-static 10.1.1.0 24 192.168.14.1 - Configure hosts.
Assign IP address 10.1.1.2/24 and default gateway IP address 10.1.1.1 to PC1; assign IP address 10.1.2.2/24 and default gateway IP address 10.1.2.1 to PC2.
- Verify the configuration.
# Check the IP routing table on SwitchA.
[SwitchA] display ip routing-table Route Flags: R - relay, D - download to fib, T - to vpn-instance ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 9 Routes : 9 Destination/Mask Proto Pre Cost Flags NextHop Interface 10.1.1.0/24 Direct 0 0 D 10.1.1.1 Vlanif10 10.1.1.1/32 Direct 0 0 D 127.0.0.1 Vlanif10 10.1.2.0/24 Static 60 0 RD 192.168.12.2 Vlanif100 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 192.168.12.0/24 Direct 0 0 D 192.168.12.1 Vlanif100 192.168.12.1/32 Direct 0 0 D 127.0.0.1 Vlanif100 192.168.14.0/24 Direct 0 0 D 192.168.14.1 Vlanif400 192.168.14.1/32 Direct 0 0 D 127.0.0.1 Vlanif400
# Check detailed information about the IP routing table on SwitchA.
[SwitchA] display ip routing-table 10.1.2.0 24 verbose Route Flags: R - relay, D - download to fib, T - to vpn-instance ------------------------------------------------------------------------------ Routing Table : Public Summary Count : 2 Destination: 10.1.2.0/24 Protocol: Static Process ID: 0 Preference: 60 Cost: 0 NextHop: 192.168.12.2 Neighbour: 0.0.0.0 State: Active Adv Relied Age: 00h13m13s Tag: 0 Priority: medium Label: NULL QoSInfo: 0x0 IndirectID: 0x80000001 RelayNextHop: 0.0.0.0 Interface: Vlanif100 TunnelID: 0x0 Flags: RD Destination: 10.1.2.0/24 Protocol: Static Process ID: 0 Preference: 70 Cost: 0 NextHop: 192.168.14.2 Neighbour: 0.0.0.0 State: Inactive Adv Relied Age: 00h00m45s Tag: 0 Priority: medium Label: NULL QoSInfo: 0x0 IndirectID: 0x80000002 RelayNextHop: 0.0.0.0 Interface: Vlanif400 TunnelID: 0x0 Flags: R
The IP routing table on SwitchA contains only one active route to network segment 10.1.2.0/24. Normally, data traffic from PC1 to PC2 is transmitted through the link that passes through SwitchB. Detailed information about the IP routing table on SwitchA shows two routes to network segment 10.1.2.0/24: one Active route that passes through SwitchB and the other Inactive route that passes through SwitchD. When faults occur on the active link, the Inactive route will become active to take over the traffic. This implements link backup.
Configuration Files
SwitchA configuration file
# sysname SwitchA # vlan batch 10 100 400 # interface Vlanif10 ip address 10.1.1.1 255.255.255.0 # interface Vlanif100 ip address 192.168.12.1 255.255.255.0 # interface Vlanif400 ip address 192.168.14.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type access port default vlan 10 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 100 # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 400 # ip route-static 10.1.2.0 255.255.255.0 192.168.12.2 ip route-static 10.1.2.0 255.255.255.0 192.168.14.2 preference 70 # return
SwitchB configuration file
# sysname SwitchB # vlan batch 100 200 # interface Vlanif100 ip address 192.168.12.2 255.255.255.0 # interface Vlanif200 ip address 192.168.23.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 100 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 200 # ip route-static 10.1.1.0 255.255.255.0 192.168.12.1 ip route-static 10.1.2.0 255.255.255.0 192.168.23.2 # return
SwitchC configuration file
# sysname SwitchC # vlan batch 20 200 300 # interface Vlanif20 ip address 10.1.2.1 255.255.255.0 # interface Vlanif200 ip address 192.168.23.2 255.255.255.0 # interface Vlanif300 ip address 192.168.34.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type access port default vlan 20 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 200 # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 300 # ip route-static 10.1.1.0 255.255.255.0 192.168.23.1 ip route-static 10.1.1.0 255.255.255.0 192.168.34.2 preference 70 # return
SwitchD configuration file
# sysname SwitchD # vlan batch 300 400 # interface Vlanif300 ip address 192.168.34.2 255.255.255.0 # interface Vlanif400 ip address 192.168.14.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 400 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 300 # ip route-static 10.1.1.0 255.255.255.0 192.168.14.1 ip route-static 10.1.2.0 255.255.255.0 192.168.34.1 # return