Example for Configuring 802.1X Authentication (Authentication Point on the Access Switch)
Networking Requirements
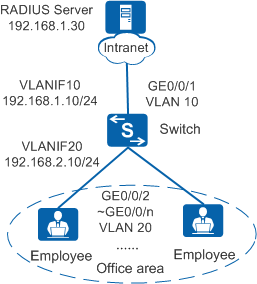
In Figure 1, terminals in a company's offices are connected to the company's intranet through the switch. GE0/0/2 to GE0/0/n on the switch are directly connected to terminals in offices. GE0/0/1 on the switch is connected to the RADIUS server through the intranet.
Configuration Roadmap
The configuration roadmap is as follows:
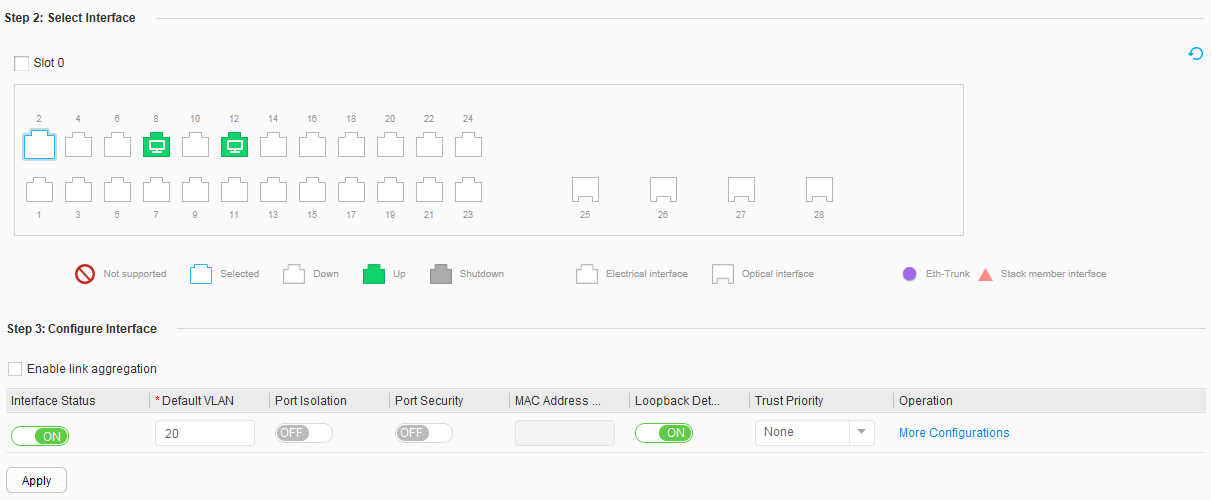
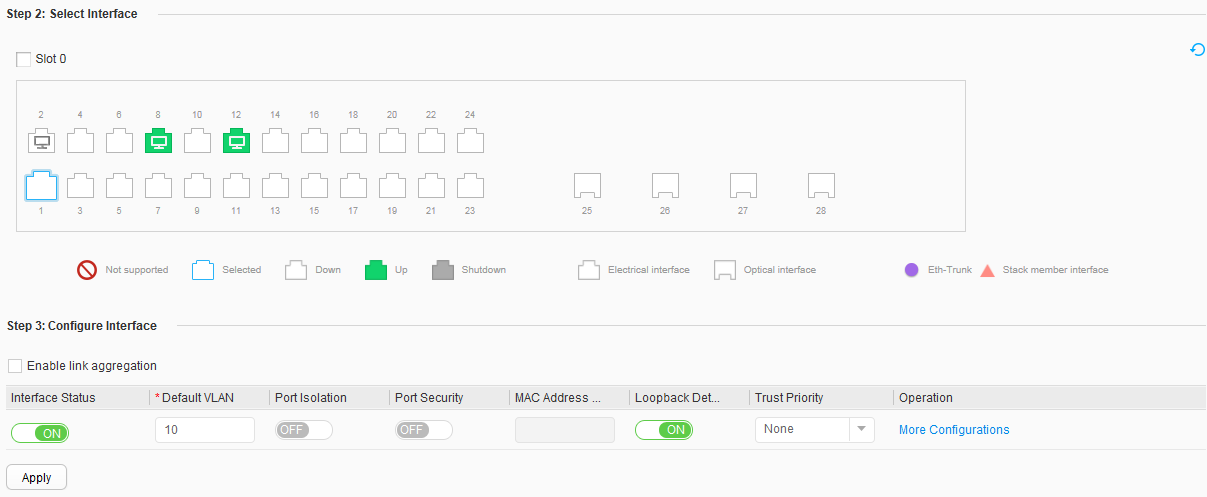
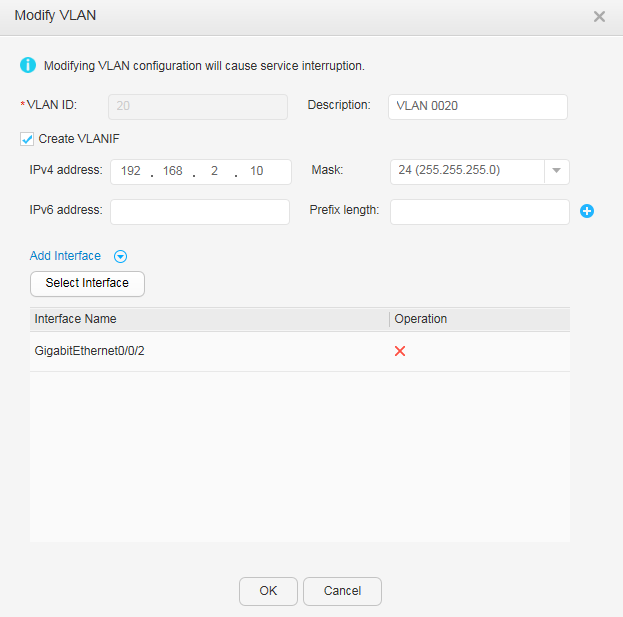
- Specify the VLANs to which interfaces belong.
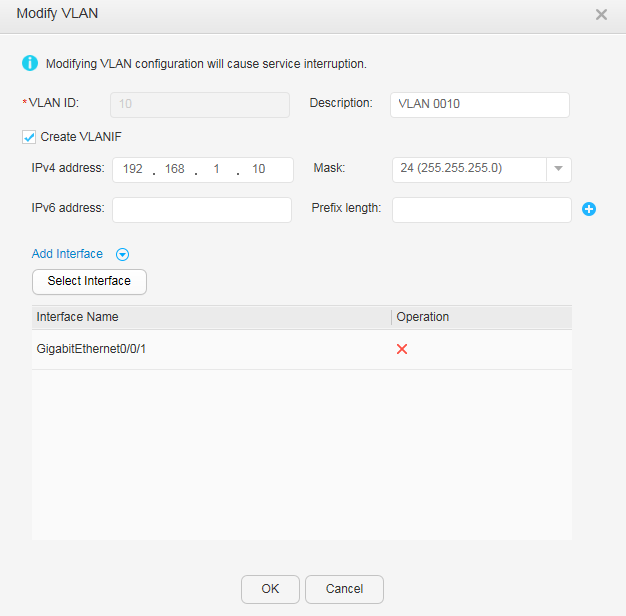
- Configure an IP address for each VLANIF interface.
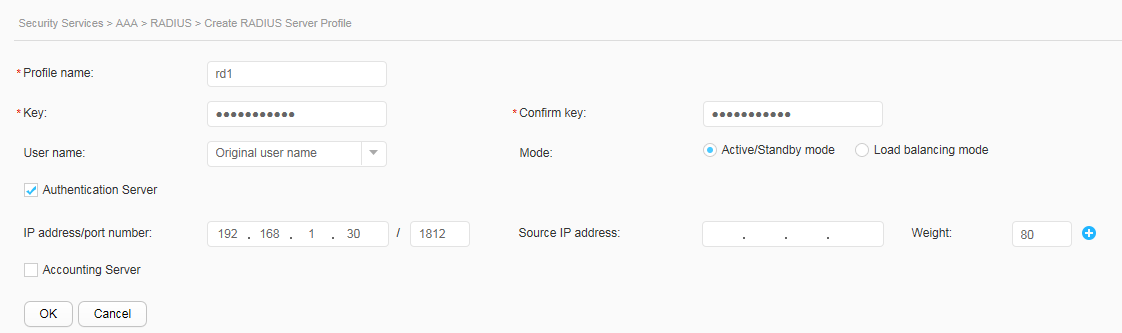
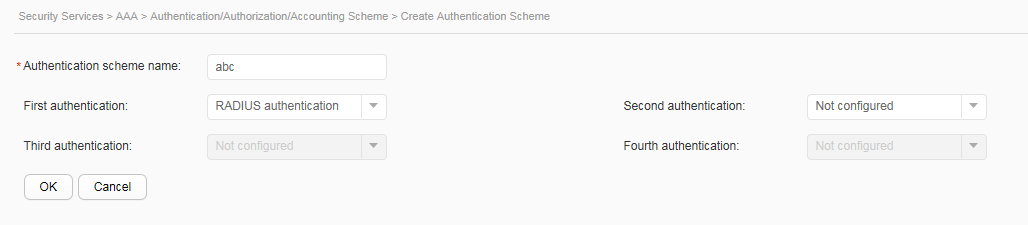
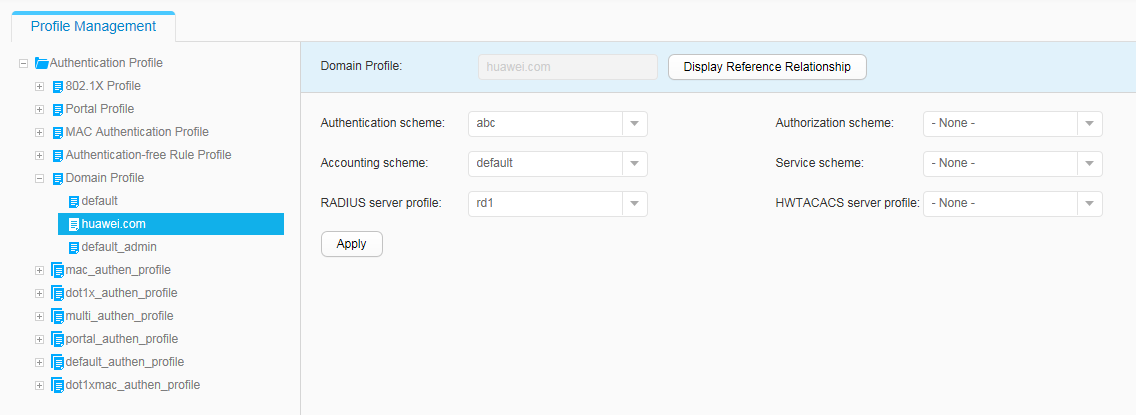
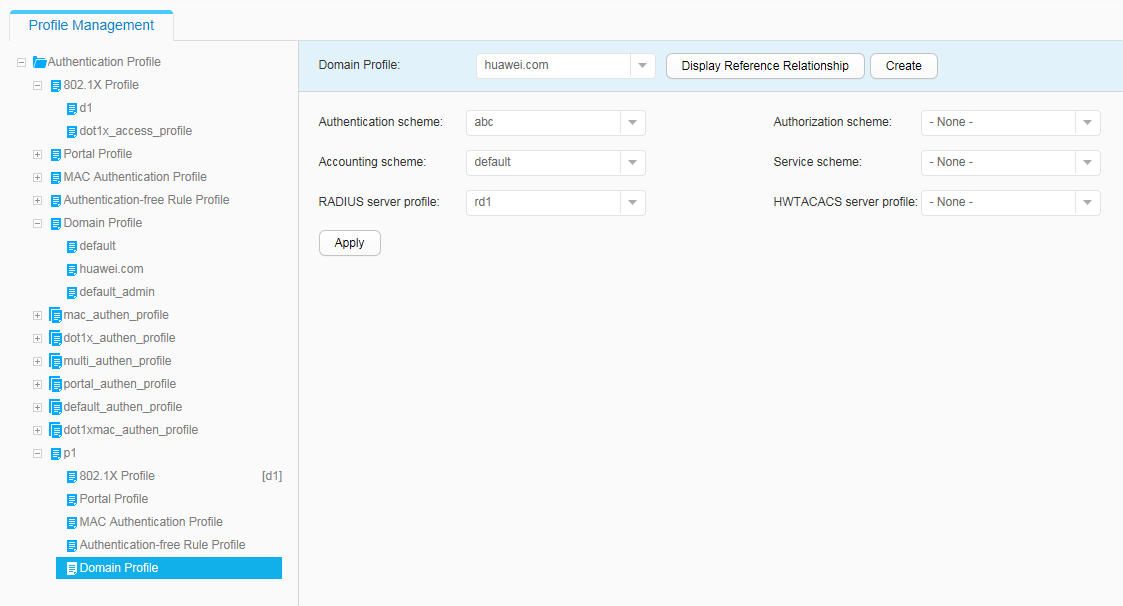
- Configure AAA on the switch to implement identity authentication on access users through the RADIUS server. The configuration includes configuring a RADIUS server template, an AAA scheme, and an authentication domain, and binding the RADIUS server template and AAA scheme to the authentication domain.
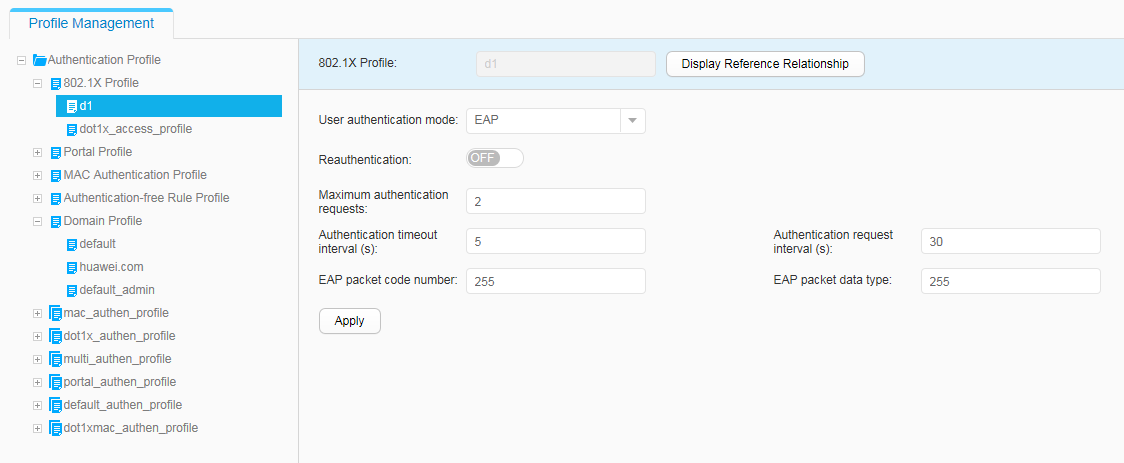
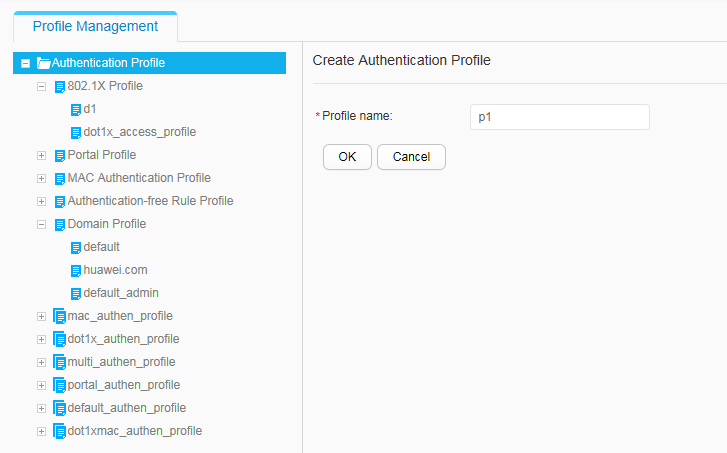
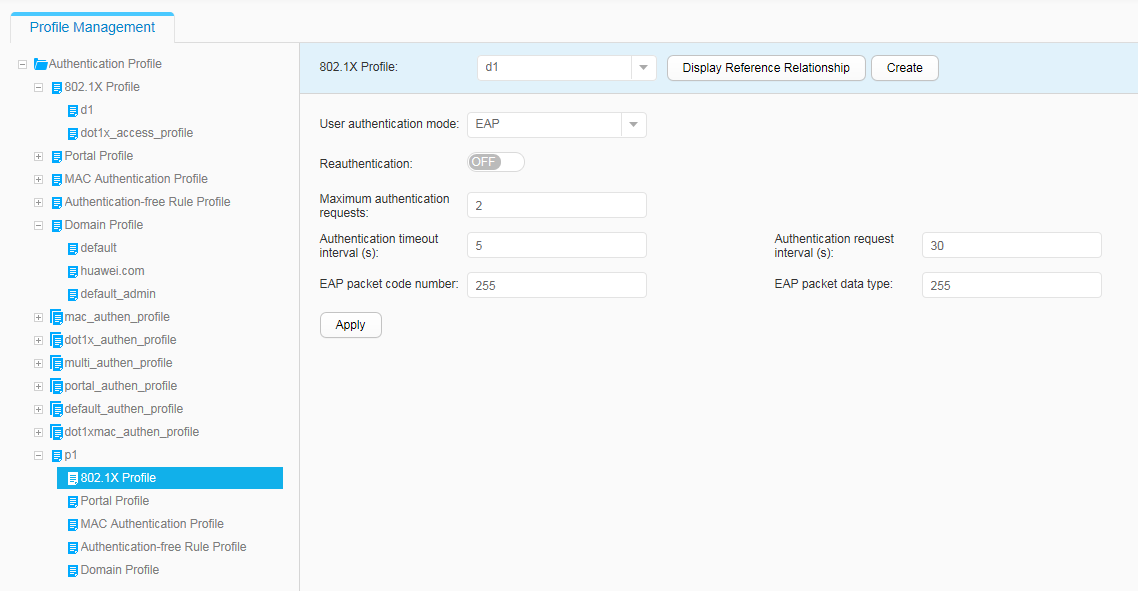
- Configure 802.1X authentication to control network access rights of the employees in offices, including the 802.1X profile, authentication profile, and 802.1X authentication on interfaces.

Before performing the following operations, ensure that there are reachable routes between user terminals and the server.
Procedure
- Specify the VLANs to which interfaces belong.
- Configure an IP address for each VLANIF interface.
- Configure AAA.
- Configure 802.1X authentication.
Operation Result
- Start the 802.1X client on a terminal, and enter the user name and password for authentication.
- If the user name and password are correct, a client page displays an authentication success information and you can access the Internet.
- After going online, log in to the web system. Choose . The 802.1X user information is displayed.