Example for Configuring RADIUS for User Authentication and Accounting (Through Flexible Interoperation of RADIUS Attributes)
This section provides an example for configuring RADIUS for user authentication and accounting. The RADIUS attributes supported by a Huawei device and a RADIUS server may be different. Python scripts can be loaded to implement flexible interoperation of RADIUS attributes.
Networking Requirements
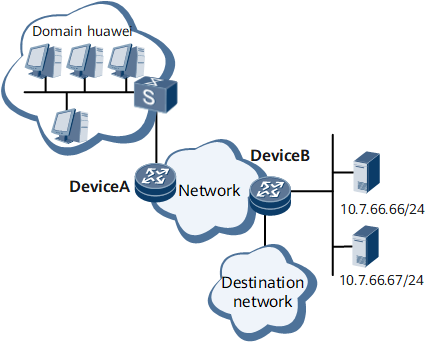
As shown in Figure 1, users access the network by logging in to Device A and the users belong to the domain huawei. Device B functions as an access server on the target network. To access the target network, users must first traverse the networks on which Device A and Device B reside and can access the network through Device B after being authenticated by a remote RADIUS server. Remote authentication and accounting modes on Device B are as follows:
RADIUS servers are used to perform authentication and accounting on the access users.
The RADIUS server at 10.7.66.66/24 functions as the primary authentication and accounting server, and the RADIUS server at 10.7.66.67/24 functions as the secondary authentication and accounting server. The default authentication and accounting port numbers 1812 and 1813 are used.
However, when Device B interoperates with the RADIUS server, the attributes carried in authentication and accounting request packets are not all the same. Therefore, you need to load the python script package to implement flexible interoperation of RADIUS attributes.
Configuration Roadmap
The configuration roadmap is as follows:
Configure a RADIUS server group, an authentication scheme, and an accounting scheme.
Bind the RADIUS server group, authentication scheme, and accounting scheme to the domain.
Load the python script package.
Configure a python policy template.
Bind the python policy template to the RADIUS server group.

The python script package must have been uploaded to the cfcard: directory.
Data Preparation
To complete the configuration, you need the following data:
IP addresses of the primary and secondary RADIUS authentication servers
IP addresses of the primary and secondary RADIUS accounting servers
Python script package
access-request.py, the python script that processes Access-Request packets
acct-request.py, the python script that processes Accounting-Request packets
Procedure
- Configure a RADIUS server group, an authentication scheme, and an accounting scheme.
# Configure a RADIUS server group named shiva.
<HUAWEI> system-view [~Device] radius-server group shiva
# Configure an IP address and a port number for the master RADIUS authentication and accounting server.
[*Device-radius-shiva] radius-server authentication 10.7.66.66 1812 [*Device-radius-shiva] radius-server accounting 10.7.66.66 1813
# Configure an IP address and a port number for the backup RADIUS authentication and accounting server.
[*Device-radius-shiva] radius-server authentication 10.7.66.67 1812 [*Device-radius-shiva] radius-server accounting 10.7.66.67 1813
# Configure a shared key and the number of retransmissions for the RADIUS server.
[*Device-radius-shiva] radius-server shared-key-cipher it-is-my-secret1 [*Device-radius-shiva] radius-server retransmit 2 [*Device-radius-shiva] commit [~Device-radius-shiva] quit
# Enter the AAA view.
[~Device] aaa
# Configure authentication scheme 1, with RADIUS as the authentication mode.
[~Device-aaa] authentication-scheme 1 [*Device-aaa-authen-1] authentication-mode radius [*Device-aaa-authen-1] commit [~Device-aaa-authen-1] quit
# Configure accounting scheme 1, with RADIUS as the accounting mode.
[~Device-aaa] accounting-scheme 1 [~Device-aaa-accounting-1] accounting-mode radius [*Device-aaa-accounting-1] commit [~Device-aaa-accounting-1] quit
- Configure a domain named huawei and bind authentication scheme 1, accounting scheme 1, and RADIUS server group shiva to the domain.
[~Device-aaa] domain huawei [*Device-aaa-domain-huawei] authentication-scheme 1 [*Device-aaa-domain-huawei] accounting-scheme 1 [*Device-aaa-domain-huawei] radius-server group shiva [*Device-aaa-domain-huawei] commit
- Enable the python script extension function.
<HUAWEI> system-view [~HUAWEI] access enable python extend script-package V800R021C00SPC100.zip [*HUAWEI] commit
- Configure a python policy template for packet processing.
# Create a python policy template.
[~HUAWEI] access python-policy py [*HUAWEI-python-policy py] commit
# Configure the association between packets and scripts in the python policy template named py.
[~HUAWEI-python-policy py] protocol radius packet access-request direction egress python-script access-request.py [*HUAWEI-python-policy py] protocol radius packet accounting-request direction egress python-script acct-request.py [*HUAWEI-python-policy py] protocol radius packet process-fail passthrough [*HUAWEI-python-policy py] commit [~HUAWEI-python-policy py] quit
- Bind the RADIUS server group to the python policy template.
[~HUAWEI] radius-server group shiva [*HUAWEI-radius-shiva] python-policy py [*HUAWEI-radius-shiva] commit
- Verify the configuration.
Run the display radius-server configuration group shiva command on the router to check the RADIUS server group configuration. The command output shows that the RADIUS server group configuration meets the requirements.
<HUAWEI> display radius-server configuration group shiva ------------------------------------------------------- Server-group-name : shiva Authentication-server: IP:10.7.66.66 Port:1812 Weight[0] [UP] Vpn: - Authentication-server: IP:10.7.66.67 Port:1812 Weight[0] [UP] Vpn: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Authentication-server: - Accounting-server : IP:10.7.66.66 Port:1813 Weight[0] [UP] Vpn: - Accounting-server : IP:10.7.66.67 Port:1813 Weight[0] [UP] Vpn: - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Accounting-server : - Protocol-version : radius Shared-secret-key : ****** Retransmission : 2 Timeout-interval(s) : 5 Acct-Stop-Packet Resend : NO Acct-Stop-Packet Resend-Times : 0 Traffic-unit : B ClassAsCar : NO User-name-format : Domain-included Option82 parse mode : - Attribute-translation: NO Packet send algorithm: Master-Backup Tunnel password : cipherRun the display domain domain-name command on the router to check the domain configuration.
<HUAWEI> display domain huawei ------------------------------------------------------------------------------ Domain-name : huawei Domain-state : Active Authentication-scheme-name : 1 Accounting-scheme-name : 1 Authorization-scheme-name : Primary-DNS-IP-address : - Second-DNS-IP-address : - Primary-NBNS-IP-address : - Second-NBNS-IP-address : - User-group-name : - Idle-data-attribute (time,flow) : 0, 60 Install-BOD-Count : 0 Report-VSM-User-Count : 0 Value-added-service : default User-access-limit : 279552 Online-number : 0 Web-IP-address : - Web-URL : - Portal-server-IP : - Portal-URL : - Portal-force-times : 2 PPPoE-user-URL : Disable IPUser-ReAuth-Time(second) : 300 Ancp auto qos adapt : Disable RADIUS-server-template : shiva Two-acct-template : - HWTACACS-server-template : - Bill Flow : Disable Tunnel-acct-2867 : Disabled Flow Statistic: Flow-Statistic-Up : Yes Flow-Statistic-Down : Yes Source-IP-route : Disable IP-warning-threshold : - Multicast Forwarding : Yes Multicast Virtual : No Max-multilist num : 4 Multicast-profile : - Quota-out : Offline ------------------------------------------------------------------------------Run the display access python-script information command on the router to check related information about the loading of a python script package.
<HUAWEI> display access python-script information Script Package Name : cfcard:/V800R021C00SPC100.zip Script Package Version : V800R021C00SPC100 Script Package Run Time : 2018-05-21 05:06:22 Script Info: --------------------------------------------------------------- ScriptName State --------------------------------------------------------------- acct-request.py Running access-request.py Running --------------------------------------------------------------- Total = 2
Configuration Files
# sysname HUAWEI # radius-server group shiva radius-server authentication 10.7.66.66 1812 weight 0 radius-server authentication 10.7.66.67 1812 weight 0 radius-server accounting 10.7.66.66 1813 weight 0 radius-server accounting 10.7.66.67 1813 weight 0 radius-server shared-key-cipher %^%#h{FXVBLZX9#`VI]EWUUaOSHGd5E!.1DGeVYEie=%^% radius-server retransmit 2 python-policy py # aaa authentication-scheme 1 authentication-mode radius # authorization-scheme default # accounting-scheme 1 accounting-mode radius # domain huawei authentication-scheme 1 accounting-scheme 1 radius-server group shiva # access enable python extend script-package cfcard:/V800R021C00SPC100c.zip # access python-policy py protocol radius packet access-request direction egress python-script access-request.py protocol radius packet accounting-request direction egress python-script acct-request.py # # return