Example for Configuring the Delivery of the EDSG Rate Limiting Service Through a RADIUS Server
This section provides an example for configuring the delivery of the EDSG rate limiting service through a RADIUS server. In this example, the RADIUS server uses authentication packets to deliver EDSG services, and the uplink and downlink bandwiths of EDSG service policies are configured.
Networking Requirements
On the network shown in Figure 1, PPPoE users access network 1 at 192.168.100.0/24 and network 2 at 192.168.200.0/24. Different fees need to be charged for traffic over networks 1 and 2. The users have different bandwidth requirements for networks 1 and 2. The uplink and downlink traffic bandwidths for access to network 1 and network 2 are limited to 1 Mbit/s and 2 Mbit/s, respectively. The AAA server uses RADIUS to deliver EDSG service policies in which parameters, such as the authentication scheme, accounting scheme, and bandwidths for uplink and downlink traffic rate limit, are specified.

In this example, interfaces 1 through 3, sub-interface 3.1, and sub-interface 3.2 represent GE 0/1/2, GE 0/1/1, GE 0/1/0, GE 0/1/0.1, and GE 0/1/0.2, respectively.
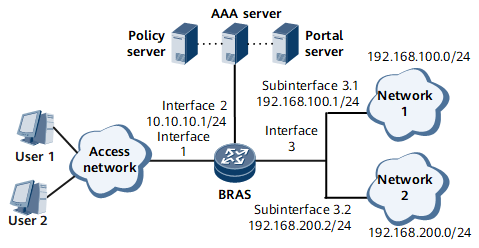

The AAA server shown in Figure 1 also functions as a policy server and delivers services through RADIUS.
Configuration Roadmap
- Enable the VAS function.
- Configure policy servers.
- Configure an EDSG traffic policy.
- Configure AAA authentication and accounting schemes.
- Configure a mode in which EDSG service policies are downloaded.
- Configure EDSG service policies.
- Configure a local address pool.
- Bind the local address pool and RADIUS server group to an AAA domain.
- Configure interfaces.
- Configure access users.
Data Preparation
Policy server parameters, such as the IP address and port number
EDSG traffic policy parameters, such as the service group name, ACL rule, traffic classifier, traffic behavior, and traffic policy
RADIUS server group name, IP address and port number of a RADIUS authentication server, and IP address and port number of a RADIUS accounting server used for an EDSG service policy
Authentication scheme name, authentication mode, accounting scheme name, and accounting mode used for an EDSG service policy
Name of the local address pool used in the domain, gateway address, and address pool range used for a user domain
EDSG service policy parameters, such as the mode in which an EDSG service policy is downloaded, policy name, bound RADIUS server group, authentication scheme, accounting scheme, and bandwidths for uplink and downlink traffic rate limiting for EDSG services
Procedure
- Enable the VAS function.
<HUAWEI> system-view [~HUAWEI] value-added-service enable [*HUAWEI] commit
- Configure policy servers.
# Set the RADIUS server group name to rad_group1, the RADIUS authentication server's IP address and port number to 10.10.10.2 and 1812, the RADIUS accounting server's IP address and port number to 10.10.10.2 and 1813, and the shared key for the RADIUS authentication and accounting servers to huawei_123.
[~HUAWEI] radius-server group rad_group1 [*HUAWEI-radius-rad_group1] radius-server authentication 10.10.10.2 1812 [*HUAWEI-radius-rad_group1] radius-server accounting 10.10.10.2 1813 [*HUAWEI-radius-rad_group1] radius-server shared-key-cipher huawei_123 [*HUAWEI-radius-rad_group1] commit [~HUAWEI-radius-rad_group1] quit

For details about how to configure a RADIUS server group, see Configuring a RADIUS Server in HUAWEI NetEngine 8000 F Series Configuration Guide - User Access.
- Configure an EDSG traffic policy.
- Configure AAA authentication and accounting schemes.
# Configure an AAA authentication scheme named auth1 and specify RADIUS authentication as the authentication mode.
[~HUAWEI] aaa [*HUAWEI-aaa] authentication-scheme auth1 [*HUAWEI-aaa-authen-auth1] authentication-mode radius [*HUAWEI-aaa-authen-auth1] commit
# Configure an AAA accounting scheme named acct1 and specify RADIUS accounting as the accounting mode.
[~HUAWEI-aaa] accounting-scheme acct1 [*HUAWEI-aaa-accounting-acct1] accounting-mode radius [*HUAWEI-aaa-accounting-acct1] quit [*HUAWEI-aaa] commit [~HUAWEI-aaa] quit
- Configure a mode in which EDSG service policies are downloaded.
# Configure the RADIUS mode for downloading EDSG service policies. In this mode, EDSG service policies are downloaded from the RADIUS server through authentication packets.
[~HUAWEI] service-policy download radius rad_group1 password cipher huawei_123 [*HUAWEI] commit
- Configure EDSG service policies. (This step is performed on the RADIUS server.)
- Configure a local address pool.
# Configure a local address pool named edsg_pool, set the gateway address to 172.31.0.1/16, and specify the address range as 172.31.0.2 to 172.31.255.255.
[~HUAWEI] ip pool edsg_pool bas local [*HUAWEI-ip-pool-edsg_pool] gateway 172.31.0.1 255.255.0.0 [*HUAWEI-ip-pool-edsg_pool] section 0 172.31.0.2 172.31.255.255 [*HUAWEI-ip-pool-edsg_pool] commit [~HUAWEI-ip-pool-edsg_pool] quit
- Bind the local address pool and RADIUS server group to an AAA domain.
# Bind the local address pool edsg_pool and the RADIUS server group rad_group1 to an AAA domain.
[~HUAWEI] aaa [*HUAWEI-aaa] domain domain1 [*HUAWEI-aaa-domain-domain1] ip-pool edsg_pool [*HUAWEI-aaa-domain-domain1] radius-server group rad_group1 [*HUAWEI-aaa-domain-domain1] quit [*HUAWEI-aaa] commit [~HUAWEI-aaa] quit
- Configure interfaces.
- Configure access users. (This step is performed on the RADIUS server.)
# Configure the RADIUS server to deliver the RADIUS attribute User-Password with a value of huawei_123 for PPPoE user 1.

The shared key configured for a RADIUS server group determines the value of the User-Password attribute.
# Configure the RADIUS server to deliver the RADIUS attribute Huawei-Account-Info (vendor ID=2011; attribute number=184) with the value of Aservice_edsg1;d1;huawei and Aservice_edsg2;d2;huawei for PPPoE user 1.

The Huawei-Account-Info attribute starting with A followed by the service policy name service_edsg1 is used in authentication response packets to deliver EDSG services that automatically take effect after being delivered; d1 and huawei indicate the authentication name and password, respectively, to be used for service authentication.
The Huawei-Account-Info attribute starting with A followed by the service policy name service_edsg2 is used in authentication response packets to deliver EDSG services that automatically take effect after being delivered; d2 and huawei indicate the authentication name and password, respectively, to be used for service authentication.

For details about the RADIUS attribute dictionary used in this step, see Description > Feature Description > User Access > Appendix: RADIUS Attributes > RADIUS Attribute Dictionary.
The RADIUS attribute names displayed in this step must be the same as those in the RADIUS attribute dictionary loaded to the RADIUS server. If they are different, change the RADIUS attribute names to be the same as those in the RADIUS attribute dictionary based on the vendor ID and attribute number.
- Verify the configuration.
# View the ID of the online user.
<HUAWEI> display value-added-service user The used user id table are: 128000# View the service group name and service status information of the user with an ID of 128000.
<HUAWEI> display value-added-service user user-id 128000 edsg ------------------------------------------------------- User access index : 128000 User name : user1 ------------------------------------------------------- Traffic rate mode : Separate Traffic statistic mode : Separate Inbound rate limit mode : Car Outbound rate limit mode : Car Service change mode : Stop-start ------------------------------------------------------- User edsg service table: ------------------------------------------------------- Index Service name State ------------------------------------------------------- 0 service_edsg1 Active 1 service_edsg2 Active -------------------------------------------------------# View detailed information about the EDSG service with a service index of 0 and a user ID of 128000.
<HUAWEI> display value-added-service user user-id 128000 edsg service-index 0 ------------------------------------------------------- Service index : 0 Service name : service_edsg1 Service type : EDSG Service state : Active Service group : s_1m Service group priority : 0 Authentication method : auth1 Account method : Radius Radius server template : rad_group1 Account session id : HUAWEI05001SSG000100d39d7b128000 Service online time(HH:MM:SS) : 00:04:36 Up committed information rate : 1000(kbps) Up Peak information rate : 1000(kbps) Up committed burst size : 187000(bytes) Up Peak burst size : 187000(bytes) Down committed information rate : 1000(kbps) Down Peak information rate : 1000(kbps) Down committed burst size : 187000(bytes) Down Peak burst size : 187000(bytes) Up flow packets(high, low) : (0, 0) Up flow bytes(high, low) : (0, 0) Down flow packets(high, low) : (0, 0) Down flow bytes(high, low) : (0, 0) ----------------------------------------------
# View the user information in domain1.
<HUAWEI> display access-user domain domain1 verbose ------------------------------------------------------------------- Basic: User access index : 128000 State : Used User name : user1 Domain name : domain1 User backup state : No RUI user state : - User access interface : GigabitEthernet0/1/2.1 User access PeVlan/CeVlan : 100/100 User access slot : 5 User MAC : 00e0-fc12-3456 User IP address : 172.31.24.253 User IP netmask : 255.255.255.255 User gateway address : 172.31.0.1 User Authen IP Type : ipv4/-/- User Basic IP Type : -/-/- User access type : PPPoE User authentication type : PPP authentication Agent-Circuit-Id : - Agent-Remote-Id : - Access-line-id Information(pppoe+): - Access start time : 2013-10-17 10:42:15 User-Group : - Next-hop : - Policy-route-IPV6-address : - AAA: RADIUS-server-template : rad_group1 Server-template of second acct: - Current authen method : RADIUS authentication Authen result : Success Current author method : Idle Author result : Success Action flag : Idle Authen state : Authed Author state : Idle Configured accounting method : RADIUS accounting Quota-out : Offline Current accounting method : RADIUS accounting Realtime-accounting-switch : Close Realtime-accounting-interval(sec) : - Realtime-accounting-send-update : No Realtime-accounting-traffic-update : No Accounting start time : 2013-10-17 10:42:15 Online time (h:min:sec) : 00:07:45 Accounting state : Accounting MTU : 1492 MRU : 1492 Idle-cut direction : Both Idle-cut-data (time,rate,idle): 0 sec, 60 kbyte/min, 0 min 0 sec Ipv4 Realtime speed : 0 kbyte/min Ipv4 Realtime speed inbound : 0 kbyte/min Ipv4 Realtime speed outbound : 0 kbyte/min Dot1X: User MSIDSN name : - EAP user : No MD5 end : No VPN&Policy-route: Vpn-Instance : - Multicast Service: Multicast-profile : - Multicast-profile-ipv6 : - Max Multicast List Number : 4 IGMP enable : Yes ACL&QoS: Link bandwidth auto adapt : Disable UpPriority : Unchangeable DownPriority : Unchangeable EDSG information: Service info : Aservice_edsg1 Flow Statistic: If flow info contain l2-head : Yes Flow-Statistic-Up : Yes Flow-Statistic-Down : Yes Up packets number(high,low) : (0,0) Up bytes number(high,low) : (0,0) Down packets number(high,low) : (0,0) Down bytes number(high,low) : (0,0) IPV6 Up packets number(high,low) : (0,0) IPV6 Up bytes number(high,low) : (0,0) IPV6 Down packets number(high,low) : (0,0) IPV6 Down bytes number(high,low) : (0,0) Dslam information : Circuit ID :- Remote ID :- Actual datarate upstream :0(Kbps) Actual datarate downstream :0(Kbps) Min datarate upstream :0(Kbps) Min datarate downstream :0(Kbps) Attainable datarate upstream :0(Kbps) Attainable datarate downstream :0(Kbps) Max datarate upstream :0(Kbps) Max datarate downstream :0(Kbps) Min lowpower datarate upstream :0(Kbps) Min lowpower datarate downstream :0(Kbps) Max delay upstream :0(s) Max delay downstream :0(s) Actual delay upstream :0(s) Actual delay downstream :0(s) Access loop encapsulation :0x000000 ------------------------------------------------------------------- Are you sure to display some information?(Y/N)[Y]:
# View traffic information of the online user.
<HUAWEI> display access-user domain domain1 verbose ------------------------------------------------------------------- Flow Statistic: If flow info contain l2-head : Yes Flow-Statistic-Up : Yes Flow-Statistic-Down : Yes Up packets number(high,low) : (0,670580346) Up bytes number(high,low) : (19,4229905664) Down packets number(high,low) : (0,670597972) Down bytes number(high,low) : (21,3689402864) IPV6 Up packets number(high,low) : (0,0) IPV6 Up bytes number(high,low) : (0,0) IPV6 Down packets number(high,low) : (0,0) IPV6 Down bytes number(high,low) : (0,0) Value-added-service Flow Statistic: EDSG(service1) Up packets number(high,low) : (0,12774777) EDSG(service1) Up bytes number(high,low) : (2,4069869415) EDSG(service1) Down packets number(high,low) : (0,0) EDSG(service1) Down bytes number(high,low) : (0,0)
Configuration Files
HUAWEI configuration file
# sysname HUAWEI # value-added-service enable # radius-server group rad_group1 radius-server authentication 10.10.10.2 1812 weight 0 radius-server accounting 10.10.10.2 1813 weight 0 radius-server shared-key-cipher %^%#x*CgITP4C~;q,*+DEW'JBWe#)"Q&|7bX]b:Y<{w'%^%# # ip pool edsg_pool bas local gateway 172.31.0.1 255.255.0.0 section 0 172.31.0.2 172.31.255.255 # aaa authentication-scheme auth1 authentication-scheme radius accounting-scheme acct1 accounting-mode radius domain domain1 ip-pool edsg_pool radius-server group rad_group1 # service-group s_1m service-group s_2m # acl number 6020 rule 10 permit ip source service-group s_1m destination ip-address 192.168.100.0 0.0.0.255 rule 20 permit ip source ip-address 192.168.100.0 0.0.0.255 destination service-group s_1m # acl number 6021 rule 15 permit ip source service-group s_2m destination ip-address 192.168.200.0 0.0.0.255 rule 25 permit ip source ip-address 192.168.200.0 0.0.0.255 destination service-group s_2m # traffic classifier c1 operator or if-match acl 6020 # traffic classifier c2 operator or if-match acl 6021 # traffic behavior b1 # traffic behavior b2 # traffic policy traffic_policy_edsg share-mode classifier c1 behavior b1 classifier c2 behavior b2 # traffic-policy traffic_policy_edsg inbound traffic-policy traffic_policy_edsg outbound # service-policy download radius rad_group1 password cipher $$e:TY%^%glhJ;yPG#$=tC&(Is%q!S_";(k.Ef$%^%#:978 # interface GigabitEthernet0/1/1 ip address 10.10.10.1 255.255.255.0 # interface GigabitEthernet0/1/2.1 user-vlan 1000 2000 user-vlan 1 1000 qinq 100 bas # access-type layer2-subscriber default-domain pre-authentication domain1 authentication-method ppp web # interface GigabitEthernet0/1/0.1 vlan-type dot1q 1 ip address 192.168.100.1 255.255.255.0 # return