Example for Configuring IPoEoVLAN Access Together with NAT
This section provides an example for configuring IPoEoVLAN access together with NAT so that home users can access the Internet through NAT processing.
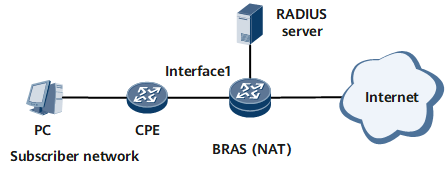
Networking Requirements
In Figure 1, home users access a BRAS using IPoE. The BRAS implements user authentication, authorization, and accounting. It also provides the NAT service to convert between the private and public IP addresses of home users, so that the home users can access the Internet.
Home users of user group 1 can access the Internet.
Configuration Roadmap
The configuration roadmap is as follows:
- Configure basic NAT functions.
- Configure NAT user information.
- Configure a NAT diversion policy.
- Configure a BAS interface.
Data Preparation
To complete the configuration, you need the following data:
- Name of a NAT instance
- NAT address pool's number and start and end IP addresses
- User group name
- ACL and UCL numbers
- NAT traffic diversion policy information
Procedure
- Create a NAT instance named nat1.
<HUAWEI> system-view [~HUAWEI] service-location 1 [*HUAWEI-service-location-1] location slot 1 [*HUAWEI-service-location-1] commit [~HUAWEI-service-location-1] quit [~HUAWEI] service-instance-group group1 [*HUAWEI-service-instance-group-group1] service-location 1 [*HUAWEI-service-instance-group-group1] commit [~HUAWEI-service-instance-group-group1] quit [~HUAWEI] nat instance nat1 id 1 [*HUAWEI-nat-instance-nat1] service-instance-group group1 [*HUAWEI-nat-instance-nat1] commit [~HUAWEI-nat-instance-nat1] quit
- Configure a NAT address pool.
[~HUAWEI] nat instance nat1 id 1 [~HUAWEI-nat-instance-nat1] nat address-group address-group1 group-id 1 11.1.1.1 mask 26 [*HUAWEI-nat-instance-nat1] commit [~HUAWEI-nat-instance-nat1] quit
- Configure NAT user information.
- Configure a traffic classification rule, a NAT behavior, and a NAT traffic policy and apply the policy.

A UCL number ranges from 6000 to 9999.
- Configure a BAS interface.
[~HUAWEI] interface Eth-Trunk 2.1 [*HUAWEI-Eth-Trunk2.1] user-vlan 1 2 [*HUAWEI-Eth-Trunk2.1-1-2] quit [*HUAWEI-Eth-Trunk2.1] bas [*HUAWEI-Eth-Trunk2.1-bas] access-type layer2-subscriber default-domain authentication isp1 [*HUAWEI-Eth-Trunk2.1-bas] client-option82 [*HUAWEI-Eth-Trunk2.1-bas] option82-relay-mode include allvalue [*HUAWEI-Eth-Trunk2.1-bas] authentication-method bind [*HUAWEI-Eth-Trunk2.1-bas] quit [*HUAWEI-Eth-Trunk2.1] quit
Configuration Files
BRAS configuration file
# service-location 1 location slot 1 # service-instance-group group1 service-location 1 # nat instance nat1 id 1 service-instance-group group1 nat address-group group1 group-id 1 11.1.1.1 mask 26 # radius-server group rd1 radius-server shared-key-cipher %^%#x*CgITP4C~;q,*+DEW'JBWe#)"Q&|7bX]b:Y<{w'%^%# radius-server authentication 192.168.8.9 1812 weight 0 radius-server accounting 192.168.8.9 1813 weight 0 radius-server type standard # ip pool pool1 bas local gateway 100.64.0.1 255.255.0.0 section 0 100.64.0.2 100.64.255.254 dns-server 192.168.8.2 # aaa authentication-scheme auth1 # accounting-scheme acct1 # domain isp1 authentication-scheme auth1 accounting-scheme acct1 radius-server group rd1 ip-pool pool1 user-group group1 # user-group group1 # acl number 6001 rule 1 permit ip source user-group group1 # traffic classifier c1 operator or if-match acl 6001 # traffic behavior b1 nat bind instance nat1 # traffic policy p1 share-mode classifier c1 behavior b1 precedence 1 # traffic-policy p1 inbound # interface Eth-Trunk2.1 user-vlan 1 2 # bas access-type layer2-subscriber default-domain authentication isp1 client-option82 option82-relay-mode include allvalue authentication-method bind # # return